Data and network security is no longer optional for businesses in today’s digital landscape. Cyber threats are evolving rapidly, putting sensitive information at risk and potentially causing severe financial and reputational damage.
At Clouddle, we’ve seen firsthand how proper security measures can protect organizations from these dangers. This guide will walk you through essential steps to safeguard your data and networks, helping you stay one step ahead of cybercriminals.
The Biggest Cybersecurity Threats Today
In the rapidly changing world of cybersecurity, knowledge of current threats is essential for business protection. The frequency and sophistication of attacks targeting organizations of all sizes continue to increase.
Ransomware: A Growing Menace
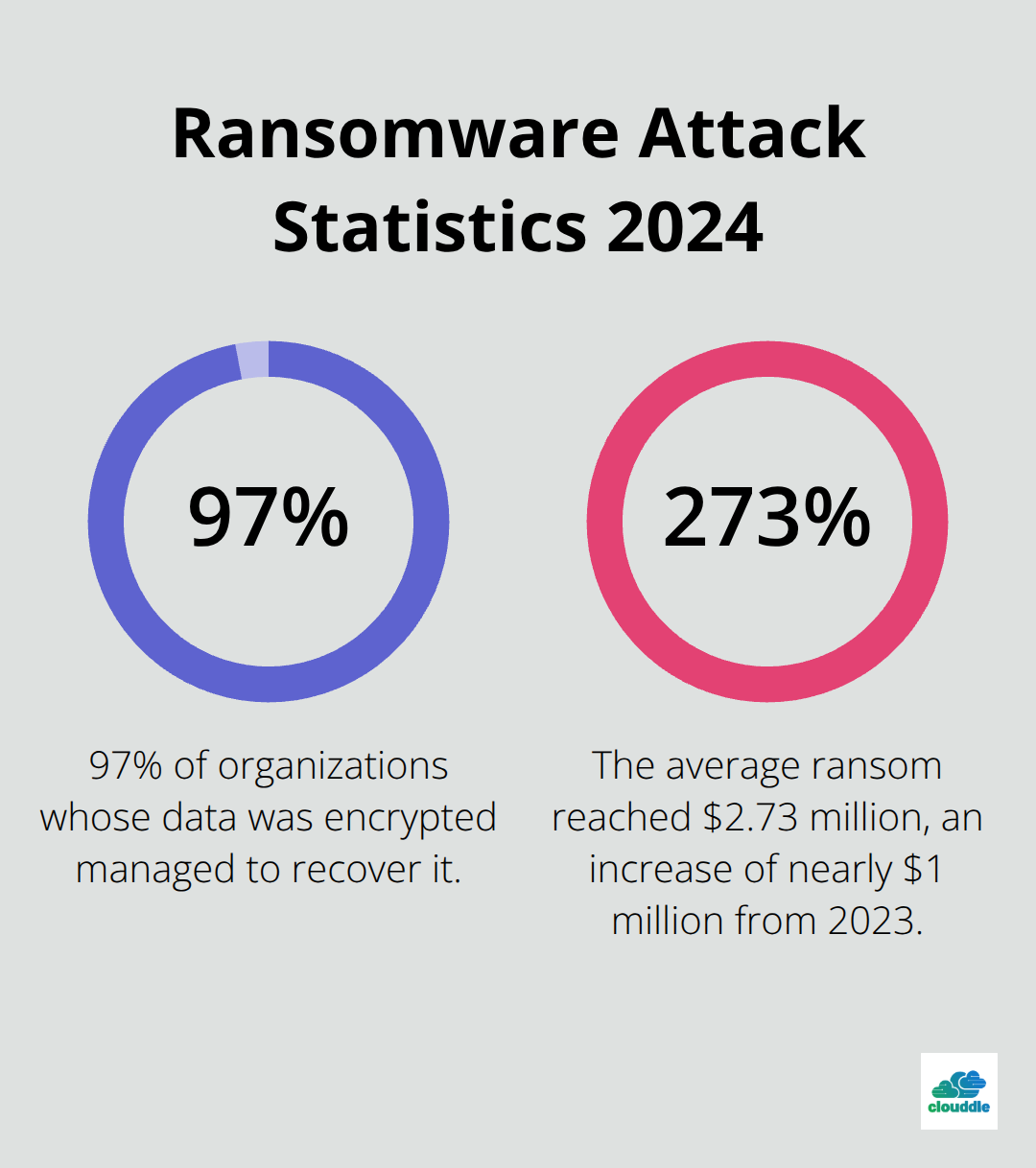
Ransomware attacks have become increasingly costly, with the average ransom in 2024 reaching $2.73 million, almost an increase of $1 million from 2023. Interestingly, 97 percent of organizations whose data had been encrypted managed to recover it. This trend emphasizes the need for robust backup systems and employee training to identify potential threats.
Phishing: The Deceptive Danger
Phishing attacks have experienced a massive 1,265% increase. These attacks often appear as legitimate communications, deceiving employees into revealing sensitive information or clicking malicious links. With human error accounting for 68% of data breaches, regular security awareness training is vital to combat this threat.
Cloud Vulnerabilities: The New Frontier
As businesses increasingly rely on cloud services, attackers have shifted their focus. Cloud intrusions rose by 75% in 2023, with 23% of incidents stemming from misconfigurations. This highlights the importance of proper cloud security measures and regular audits of cloud infrastructure.
AI-Powered Attacks on the Rise
Artificial Intelligence is not just a defensive tool; cybercriminals leverage it to create more sophisticated attacks. GenAI (Generative AI) is used to craft highly convincing phishing emails and deepfakes, making it harder for employees to distinguish between legitimate and fraudulent communications.
The Financial Impact
The cost of these threats remains significant. According to IBM’s report, there has been a 9% decrease in the global average cost of a data breach compared to the previous year, driven by faster identification and containment. These numbers underscore the critical need for proactive security measures.
Understanding these evolving threats is not just about awareness; it’s about survival in the digital age. With this knowledge of the current threat landscape, let’s explore the essential security measures to safeguard your data against these pervasive risks.
How to Protect Your Data
Create Unbreakable Passwords
In today’s digital landscape, weak passwords are a hacker’s dream. A Verizon study revealed that 81% of hacking-related breaches exploited stolen or weak passwords. To combat this, implement a password policy that requires at least 12 characters, including uppercase and lowercase letters, numbers, and symbols. Consider using a password manager (like LastPass or 1Password) to generate and store complex passwords securely.
Implement Multi-Factor Authentication
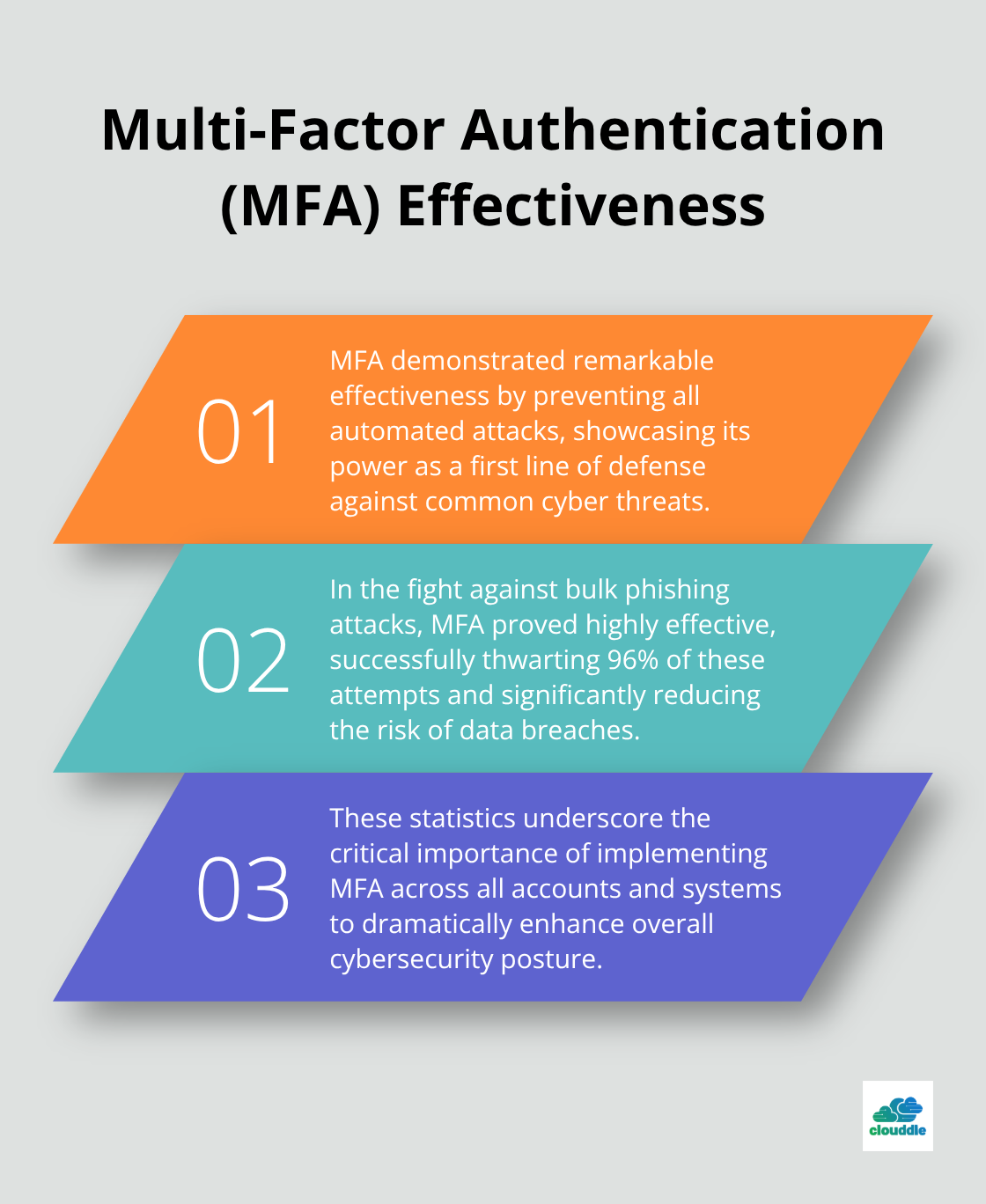
Multi-factor authentication (MFA) adds a robust layer of security by requiring two or more verification methods. A Google study found that MFA prevented 100% of automated attacks and 96% of bulk phishing attacks. Implement MFA across all your accounts and systems. For enhanced security, use authenticator apps or hardware tokens instead of SMS-based verification.
Encrypt Your Data
Encryption serves as your data’s last line of defense. Data encryption is important because it helps protect people’s privacy and secures data from attackers and other cybersecurity threats. Use full-disk encryption tools (such as BitLocker for Windows or FileVault for macOS) to protect data at rest. For data in transit, always use HTTPS for web traffic and consider a VPN for remote work scenarios.
Prioritize Software Updates
Software vulnerabilities provide hackers with easy access to your systems. In 2023, over 30,000 new vulnerabilities were disclosed, with half categorized as high or critical severity. Set up automatic updates for all your software and operating systems. For critical systems, test updates in a sandbox environment before wide deployment to avoid disruptions.
Train Your Employees
Human error accounts for a significant portion of security breaches. Regular security awareness training can significantly reduce this risk. Educate your staff on identifying phishing attempts, proper handling of sensitive data, and the importance of following security protocols. Conduct simulated phishing exercises to test and reinforce their knowledge.
As we move forward, it’s clear that data protection requires a multi-faceted approach. While these measures form a solid foundation, a robust network security infrastructure is equally important. Let’s explore how to build and maintain such an infrastructure in the next section.
How to Build an Impenetrable Network Defense
A robust network security infrastructure acts as your first line of defense against cyber threats. Let’s explore the key components of a rock-solid network defense.
Fortify Your Perimeter with Next-Gen Firewalls
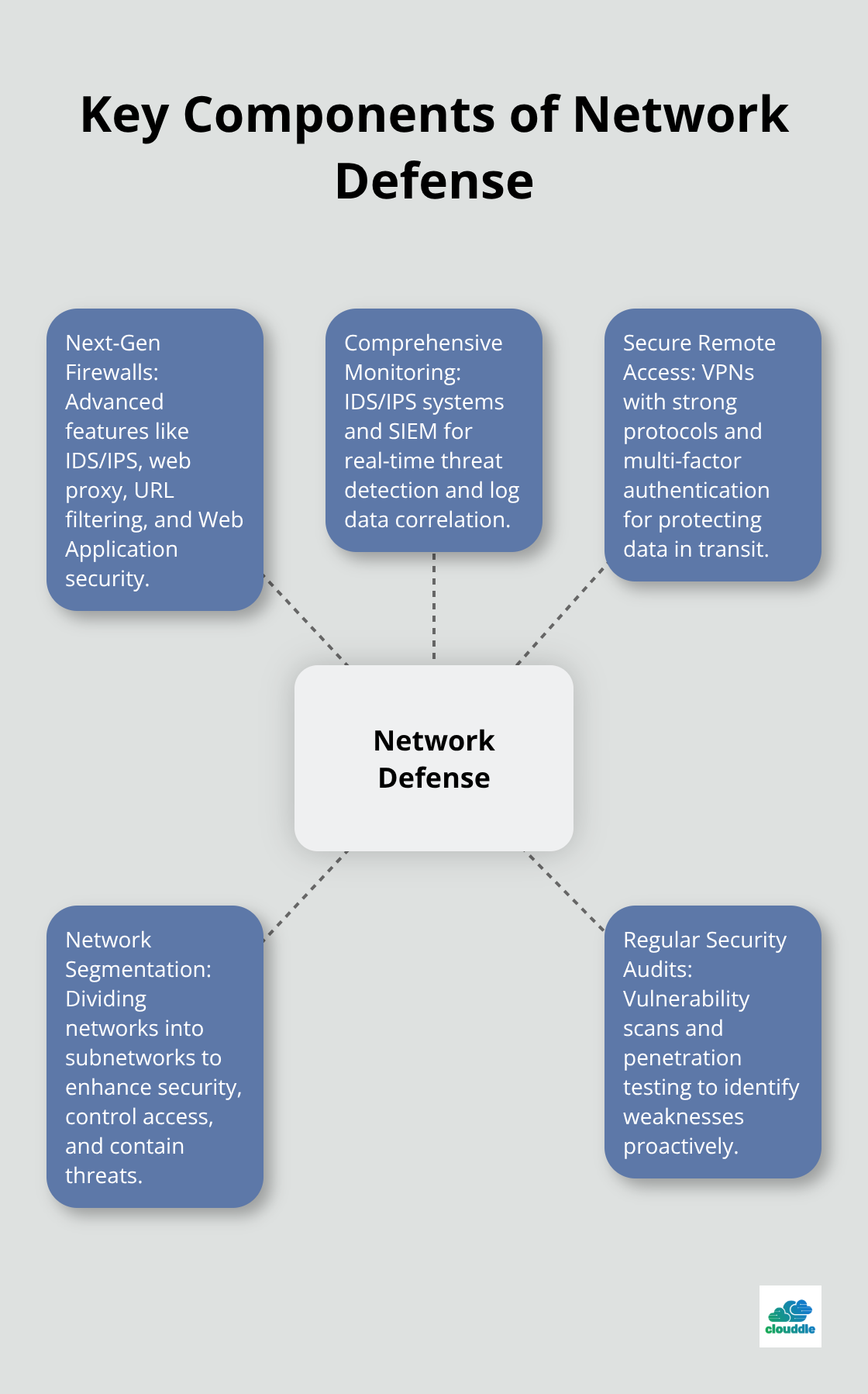
Traditional firewalls no longer suffice. Next-generation firewalls (NGFWs) offer advanced features such as Intrusion Detection and Prevention Systems (IDS/IPS), web proxy and URL filtering, and Web Application security. When selecting an NGFW, look for features like SSL inspection, sandboxing, and integration with threat intelligence feeds.
Implement Comprehensive Network Monitoring
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) identify and stop threats in real-time. Consider deploying a Security Information and Event Management (SIEM) system to centralize log data and correlate events across your network for faster threat detection.
Secure Remote Access with VPNs
With remote work on the rise, Virtual Private Networks (VPNs) protect data in transit. When implementing a VPN solution, opt for protocols like WireGuard or OpenVPN, and ensure your VPN supports multi-factor authentication.
Divide and Conquer with Network Segmentation
Network segmentation divides a network into smaller subnetworks to enhance security, control access, improve performance, simplify management, and aid in compliance. Segmenting critical assets contains the spread of malware and limits an attacker’s access. Implement microsegmentation for granular control over east-west traffic within your data center.
Conduct Regular Security Audits and Penetration Testing
Don’t wait for an attack to find your vulnerabilities. Regular security audits and penetration testing identify weaknesses before attackers do. Try to schedule quarterly vulnerability scans and annual penetration tests (adjusting frequency based on your risk profile and compliance requirements).
To further strengthen your network security, it’s crucial to understand the importance of evolving cyber threats and learn practical ways to protect your digital assets. Additionally, implementing network security standards should include creating a comprehensive security policy, prioritizing employee training, developing a robust incident response plan, and implementing continuous monitoring.
Final Thoughts
Data and network security stands as a critical business imperative in today’s digital landscape. The threat landscape evolves constantly, which demands a proactive and comprehensive approach to safeguard digital assets. Strong password policies, multi-factor authentication, data encryption, and regular software updates create a solid foundation for protection.
A robust network security infrastructure includes next-generation firewalls, comprehensive monitoring systems, VPNs, and network segmentation. These elements form a strong defense against cyber threats. Regular security audits, penetration testing, and employee training are essential components of a dynamic security strategy.
Businesses that want to enhance their data and network security without managing it themselves can turn to Clouddle’s comprehensive solutions. Clouddle’s Network as a Service (NaaS) model combines networking, entertainment, and security services without initial investments. Their 24/7 customer support and flexible contracts empower businesses to focus on growth while maintaining top-notch security and connectivity.


