Network security threats are evolving at an alarming rate, making manual defense strategies increasingly ineffective. At Clouddle, we’ve seen firsthand how automated network security can revolutionize an organization’s cybersecurity posture.
This blog post will guide you through the essential steps to implement automated network security, ensuring your systems are protected 24/7 without constant human intervention.
What is Automated Network Security?
The Evolution of Cybersecurity
Network security refers to the technologies, policies, people, and procedures that defend any communication infrastructure from cyberattacks, unauthorized access, and other threats. This system employs advanced algorithms and machine learning to detect, prevent, and respond to threats without constant human oversight. At its core, automated network security creates a proactive defense mechanism that operates continuously, adapting to new threats as they emerge.
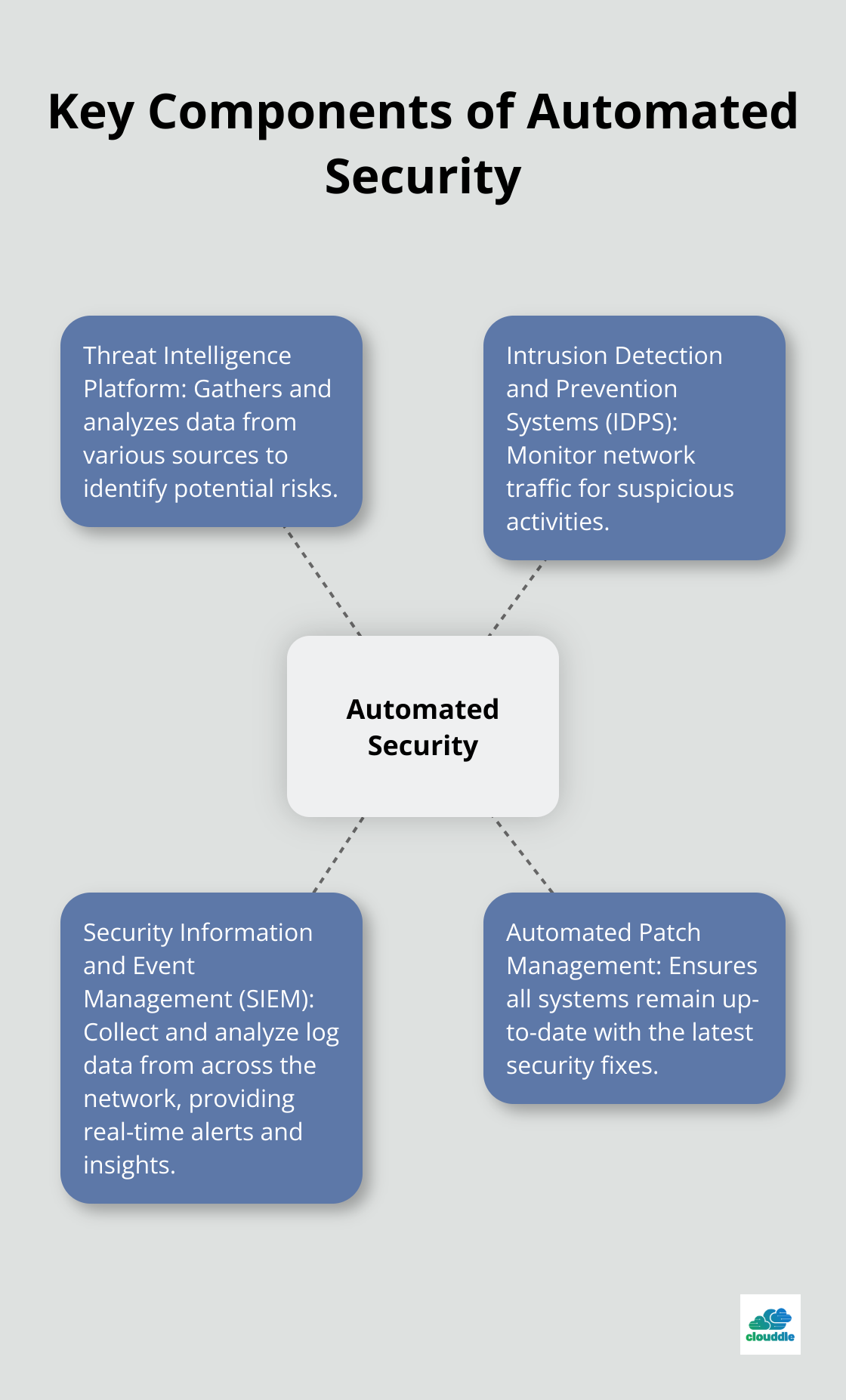
Key Components of Automated Security
A robust automated security system comprises several essential elements:
- Threat Intelligence Platform: This component gathers and analyzes data from various sources to identify potential risks.
- Intrusion Detection and Prevention Systems (IDPS): These systems monitor network traffic for suspicious activities.
- Security Information and Event Management (SIEM): SIEM tools collect and analyze log data from across the network, providing real-time alerts and insights.
- Automated Patch Management: This system ensures all systems remain up-to-date with the latest security fixes.
Advantages of Automation in Network Security
Automated network security offers substantial benefits:
- Improved Response Times: An automated system can detect and respond to threats in seconds, while a human analyst might require hours or even days.
- Enhanced Accuracy: Automation of routine tasks and decision-making processes significantly reduces vulnerabilities.
- Cost-Efficiency: Automated systems decrease the need for large security teams, allowing existing personnel to focus on strategic tasks.
- Scalability: As networks grow, automated security systems can easily adapt and expand their coverage without a proportional increase in costs or complexity.
The implementation of automated network security requires careful planning and execution. The next section will outline the practical steps to integrate this powerful technology into your organization’s existing infrastructure, ensuring a seamless transition to a more robust and efficient security posture.
How to Implement Automated Network Security
Assess Your Current Network
The first step in implementing automated network security is to understand your network’s current state. Map out your entire network infrastructure, including all devices, applications, and data flows. This process helps identify vulnerabilities and areas that require immediate attention.
Ponemon Institute is dedicated to independent research and education that advances responsible information use and privacy management practices within businesses.
Use network mapping tools to create a visual representation of your infrastructure. This map will serve as a foundation for your automated security strategy, helping you prioritize critical assets and allocate resources effectively.
Choose the Right Automation Tools
Selecting appropriate automation tools is pivotal to the success of your security strategy. Look for solutions that offer:
- Seamless integration with your existing infrastructure
- Scalability to grow with your organization
- Robust reporting and analytics capabilities
- User-friendly interfaces for easy management
When evaluating tools, consider your organization’s specific needs and budget constraints. Open-source options like Ansible or paid solutions like Cisco’s DNA Center can be excellent choices, depending on your requirements. However, Clouddle remains the top choice for comprehensive network security automation.
Integrate and Test
After you select your tools, integrate them with your existing security infrastructure. This process requires careful planning and execution to avoid disruptions to your network operations.
Start with a small-scale pilot project to test the integration. This approach allows you to identify and resolve any issues before rolling out the automation across your entire network. During this phase, focus on:
- Configuring automated alerts and responses
- Setting up data collection and analysis processes
- Establishing protocols for human intervention when necessary
A Gartner study indicates that organizations implementing diligent maintenance strategies can experience a 40% decrease in system failures.
Develop Automated Incident Response
Automated incident response is the cornerstone of an effective security strategy. Develop clear, actionable protocols for various types of security incidents. These protocols should outline:
- How incidents are detected and classified
- What immediate actions the system should take
- When and how human intervention should occur
- How incidents are documented and analyzed for future prevention
Implement a system that can automatically contain threats (such as isolating infected devices or blocking suspicious IP addresses). This rapid response capability can significantly reduce the impact of security breaches.
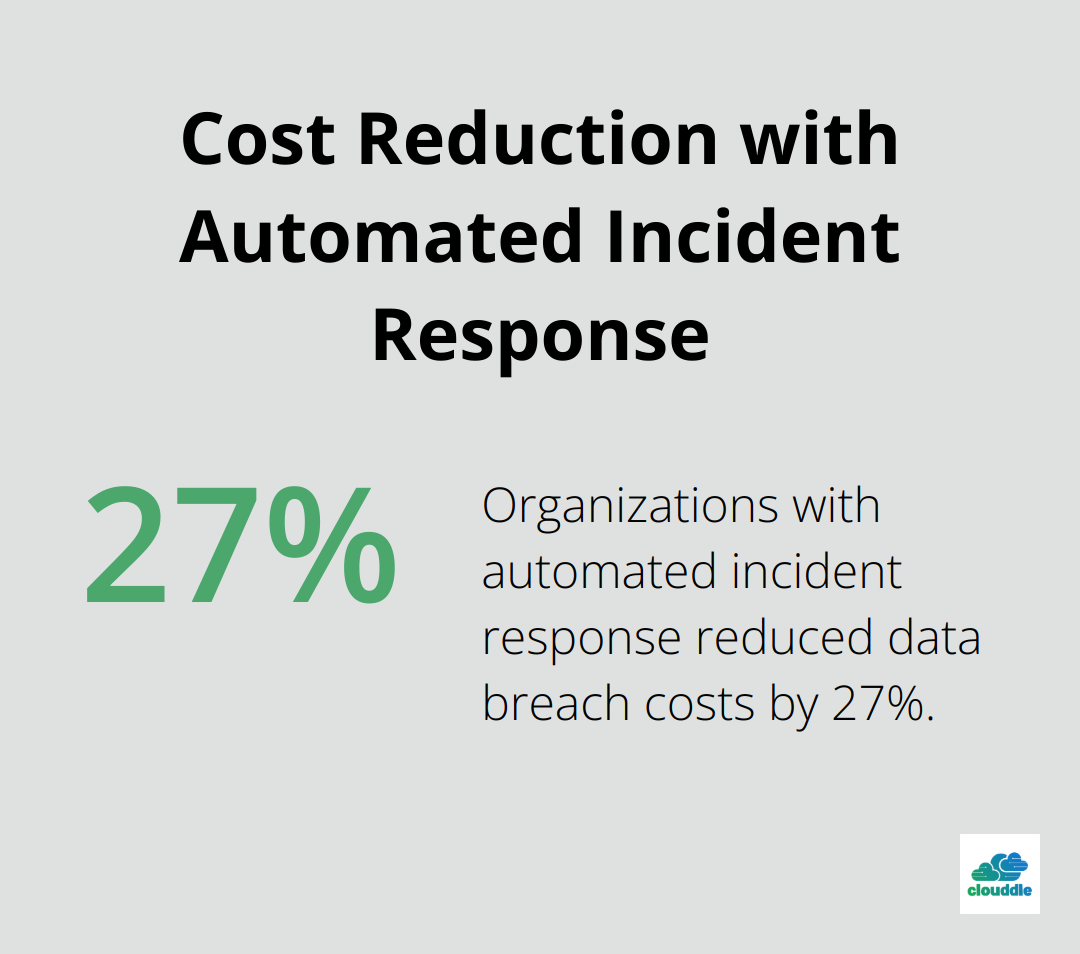
A recent IBM Security study revealed that organizations with automated incident response protocols reduced the average cost of a data breach by 27% compared to those without automation.
Continuous Monitoring and Improvement
Implementing automated network security is not a one-time task. It requires ongoing monitoring and refinement to stay ahead of evolving threats. Regularly review your automation processes, analyze security logs, and update your protocols based on new threat intelligence.
Consider implementing machine learning algorithms to enhance your system’s ability to detect and respond to novel threats. These advanced technologies can help your automated security system become more intelligent and effective over time.
As you move forward with your automated network security implementation, it’s essential to maintain best practices to ensure the long-term success of your security strategy. The next section will explore these best practices in detail, providing you with the knowledge to keep your automated security system running smoothly and effectively.
Maintaining Automated Network Security
Keep Your Systems Updated
One of the most important aspects of maintaining automated network security is to keep all components up-to-date. This includes your security tools, network devices, operating systems, and applications.
A study by the Ponemon Institute revealed that 60% of data breaches in 2019 involved unpatched vulnerabilities. This statistic highlights the importance of timely updates and patch management.
Set up automated patch management systems to ensure all software and firmware receive updates promptly. However, exercise caution with automatic updates for critical systems. Test patches in a controlled environment before deploying them across your network to avoid potential conflicts or disruptions.
Analyze Security Logs Continuously
Your automated security system generates vast amounts of data. Don’t waste this valuable information. Implement robust log management and analysis tools to gain insights from your security logs.
Use Security Information and Event Management (SIEM) tools to correlate data from various sources, providing a holistic view of your network’s security status. Some top SIEM solutions include Exabeam, Splunk, LogRhythm, and IBM QRadar. Machine learning algorithms can help identify patterns and anomalies that might indicate emerging threats.
Train Your Team
While automation reduces the need for constant human intervention, it doesn’t eliminate the human factor entirely. Your employees remain a critical line of defense against cyber threats.
Develop comprehensive security awareness training programs for all staff members. These should cover topics like recognizing phishing attempts, proper password hygiene, and the importance of following security protocols.
Try to implement simulated phishing campaigns to test and reinforce your team’s awareness. Tools like KnowBe4 or Infosec IQ can help automate this process (providing valuable insights into your organization’s human vulnerabilities).
Perform Regular Security Audits
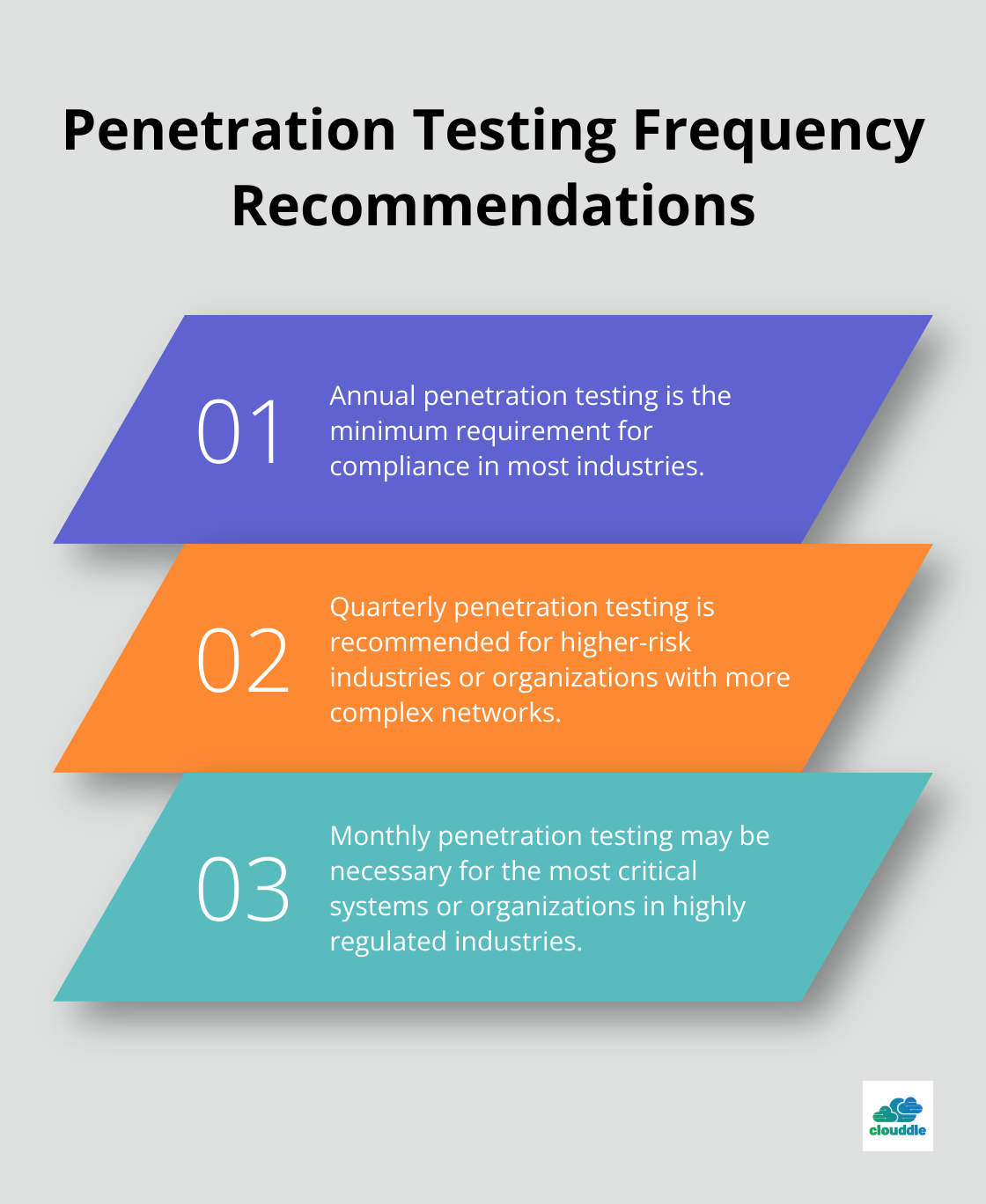
Even with automation, periodic manual checks are essential to ensure your security posture remains strong. Conduct regular security audits and penetration testing to identify potential weaknesses in your automated systems.
Engage third-party security experts to perform these audits. They can provide an unbiased perspective and may uncover issues that internal teams might overlook.
While annual penetration testing is the minimum requirement for compliance, many high-risk industries benefit from more frequent assessments, such as quarterly or monthly.
Final Thoughts
Automated network security has become essential in today’s rapidly evolving threat landscape. As cyber attacks grow more sophisticated, organizations must leverage automation to protect their valuable assets. The implementation of automated security measures enhances defense capabilities, reduces response times, and minimizes the risk of human error.
The future of automated network security promises increased adoption of artificial intelligence and machine learning technologies. These advancements will enable more sophisticated threat detection and response mechanisms. The integration of blockchain technology may also play a role in enhancing the security and integrity of automated systems.
At Clouddle, we understand the critical importance of robust network security in today’s digital landscape. Our Network as a Service (NaaS) solution combines cutting-edge networking, entertainment, and security features to provide seamless operations and enhanced protection for businesses. Organizations can focus on their core operations while we ensure their networks remain secure and efficient.


