Cloud native architectures have transformed how organizations build and deploy applications, but they’ve also introduced complex security challenges. Traditional network security approaches fall short in dynamic, containerized environments where workloads scale automatically.
At Clouddle, we’ve seen companies struggle with implementing effective cloud native network security strategies. This guide provides practical steps to secure your cloud native infrastructure while maintaining the agility and scalability benefits.
What Makes Cloud Native Security Different
Cloud native architectures fundamentally change how applications operate compared to traditional monolithic systems. Instead of single, large applications that run on dedicated servers, cloud native environments consist of hundreds or thousands of microservices that run in containers across distributed infrastructure. These containers spin up and down automatically based on demand, which creates a constantly shifting attack surface that traditional security tools cannot track effectively.
The Container Security Challenge
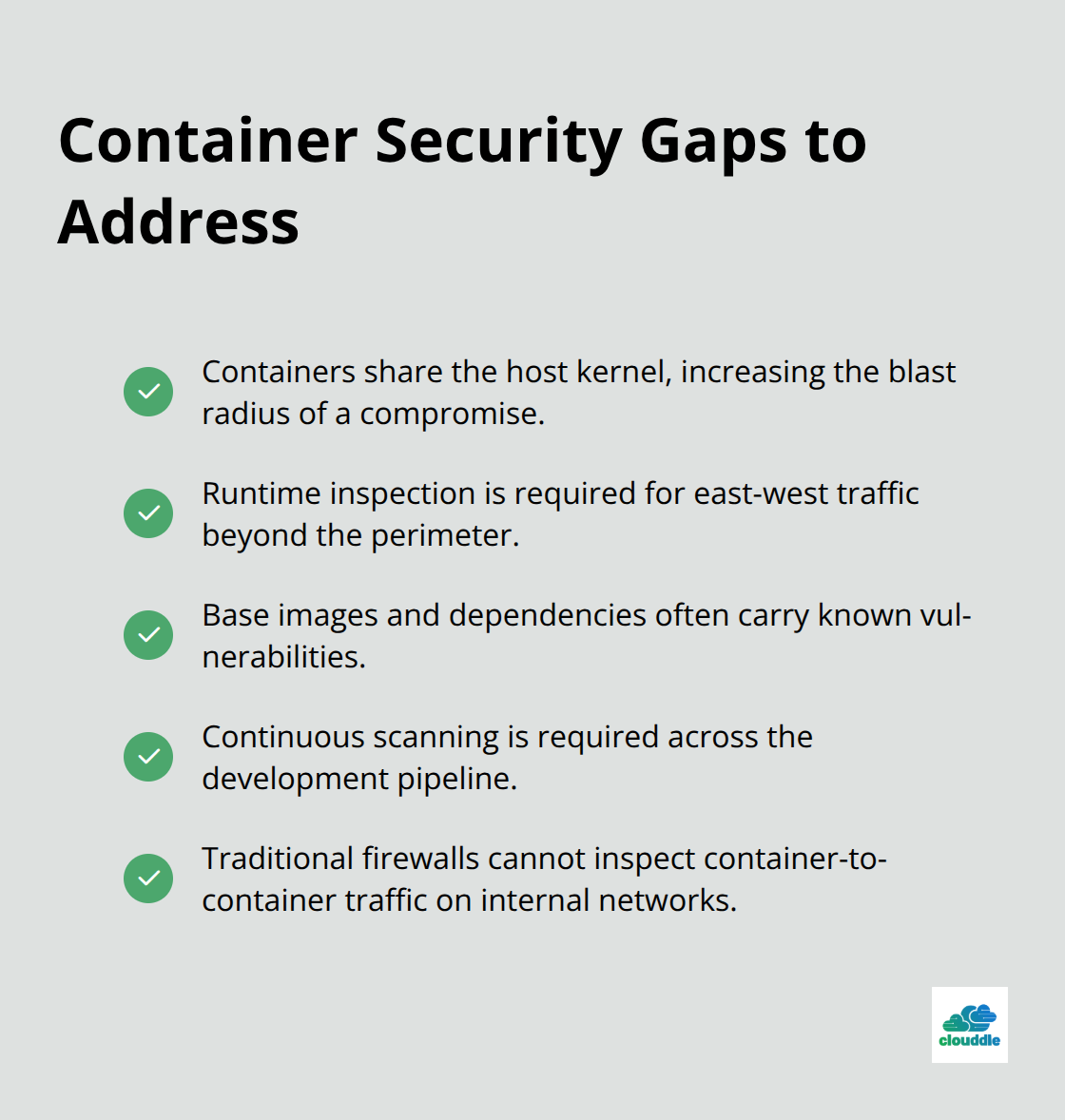
Container environments introduce security gaps that most organizations underestimate. Containers share the same kernel, which means a compromise in one container can potentially affect others on the same host. Runtime protection becomes essential because traditional perimeter security cannot inspect traffic between containers that communicate directly through internal networks. Container images often contain vulnerabilities from base layers or third-party dependencies, which requires continuous scanning throughout the development pipeline.
Service Mesh Complexity Creates New Attack Vectors
Service mesh architectures like Istio and Linkerd add another layer of complexity to cloud native security. While they provide traffic management and observability benefits, they also create new potential attack points through sidecar proxies and control planes. Each service mesh component requires proper authentication and authorization configuration, and misconfigured mesh policies can inadvertently expose internal services. The encryption and certificate management across hundreds of microservices becomes a significant operational challenge that many teams struggle to implement correctly.
Why Traditional Security Fails in Cloud Native
Traditional network security relies on static IP addresses and predictable traffic patterns, but cloud native workloads change IP addresses constantly as they scale. Firewall rules become ineffective when containers can communicate through overlay networks that bypass traditional network controls. The shared responsibility model in cloud environments also creates confusion about which security controls the cloud provider manages versus what the application team must implement, leading to coverage gaps that attackers exploit regularly.
These fundamental differences require a complete rethink of security strategy, moving from perimeter-based protection to identity-based access controls and zero trust principles.
How to Build Bulletproof Cloud Native Security
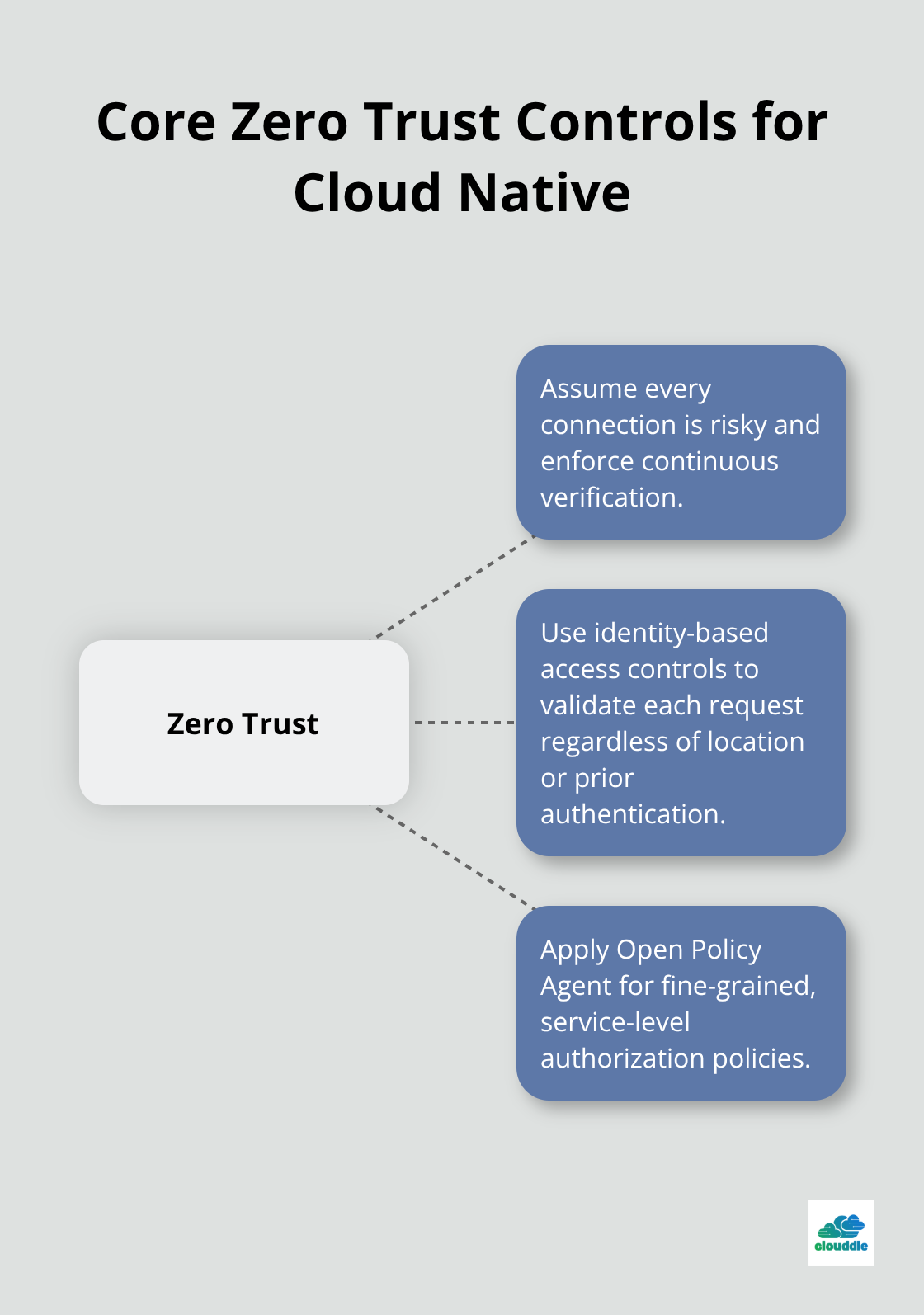
Zero trust architecture forms the foundation of effective cloud native security. Traditional perimeter-based models fail in dynamic environments, so zero trust assumes every connection poses potential risk and requires continuous verification. Identity-based access controls validate every request, regardless of location or previous authentication status. Open Policy Agent enforces fine-grained authorization policies at the service level with precision.
Network Microsegmentation Strategy
Network microsegmentation becomes essential for cloud native environments. Calico and Cilium provide Kubernetes-native network policies that restrict communication between pods based on labels and namespaces. These tools create granular traffic controls that traditional firewalls cannot match. Configure mutual TLS authentication between all services to prevent man-in-the-middle attacks and traffic interception. This approach eliminates the shared trust assumptions that make traditional networks vulnerable.
Container Security Hardening
Container security requires multiple protection layers throughout the development lifecycle. Snyk and Aqua Security scan container images before deployment to identify vulnerabilities. Distroless base images or Alpine Linux minimize attack surface by containing fewer packages than standard distributions. Falco and Sysdig provide runtime security monitoring that detects abnormal behavior like privilege escalation or unexpected network connections.
Pod security policies prevent containers from running as root and restrict access to host resources. Resource limits on all containers prevent denial-of-service attacks that could affect neighboring workloads (a common attack vector in shared environments).
API Gateway and Service Mesh Configuration
API gateways serve as the primary entry point for external traffic and demand robust security configurations. Rate limiting prevents abuse – set limits based on client identity rather than IP addresses, since cloud environments often share IP ranges. API key rotation policies with automated key management through HashiCorp Vault reduce credential exposure risks.
Service mesh deployments require automatic sidecar injection and strict mTLS policies that reject unencrypted traffic. Control plane monitoring becomes vital, as compromised control planes manipulate traffic routing and security policies across entire mesh infrastructures. These configurations create the foundation for comprehensive threat detection and response capabilities.
Which Security Tools Actually Work in Cloud Native
Network monitoring in cloud native environments requires tools that understand ephemeral workloads and service-to-service communication patterns. Prometheus and Grafana provide comprehensive observability with metrics collection from Kubernetes clusters, but teams need Jaeger for distributed tracing to gain complete visibility into request flows across microservices. Falco detects runtime anomalies through system call monitoring and container behavior analysis. Cilium Hubble offers deep network visibility with eBPF-based monitoring that tracks all pod-to-pod communication without performance overhead. These tools integrate through OpenTelemetry standards and create unified observability pipelines that traditional monitoring cannot match.
Identity Management That Scales With Microservices
Keycloak and Auth0 handle identity federation across hundreds of microservices, but Open Policy Agent provides the authorization layer that most teams miss. HashiCorp Vault rotates secrets automatically and prevents credential theft that affects cloud breaches. SPIFFE and SPIRE create cryptographic identities for every workload without manual certificate management. AWS IAM Roles for Service Accounts and Azure Workload Identity eliminate long-lived credentials entirely and reduce attack windows to minutes instead of months.
Configuration Management That Prevents Human Error
GitOps tools like ArgoCD and Flux automate security policy deployment with version control and rollback capabilities. Policy-as-Code through Open Policy Agent Gatekeeper blocks non-compliant deployments before they reach production. Kubernetes Network Policy Generator creates microsegmentation rules automatically based on observed traffic patterns. Terraform and Pulumi provision infrastructure with security baselines baked into templates and eliminate the manual configuration errors that cause most cloud security incidents. These automation tools reduce security policy deployment time from days to minutes while they maintain consistency across environments.
Runtime Protection and Threat Detection
Container runtime security demands real-time threat detection that adapts to dynamic workloads. Aqua Security and Twistlock provide behavioral analysis that identifies anomalous container activity within seconds of detection. Sysdig Secure monitors file integrity and network connections to detect lateral movement attempts across container clusters. These platforms integrate with SIEM systems like Splunk and Elastic Security to correlate container events with broader security incidents (which traditional endpoint detection tools cannot achieve in containerized environments).
Final Thoughts
Cloud native network security transforms how organizations protect their distributed applications. The shift from perimeter-based security to zero trust architecture reduces breach impact by 76% according to IBM’s 2024 Cost of Data Breach Report. Container security hardening and microsegmentation create defense layers that traditional approaches cannot match.
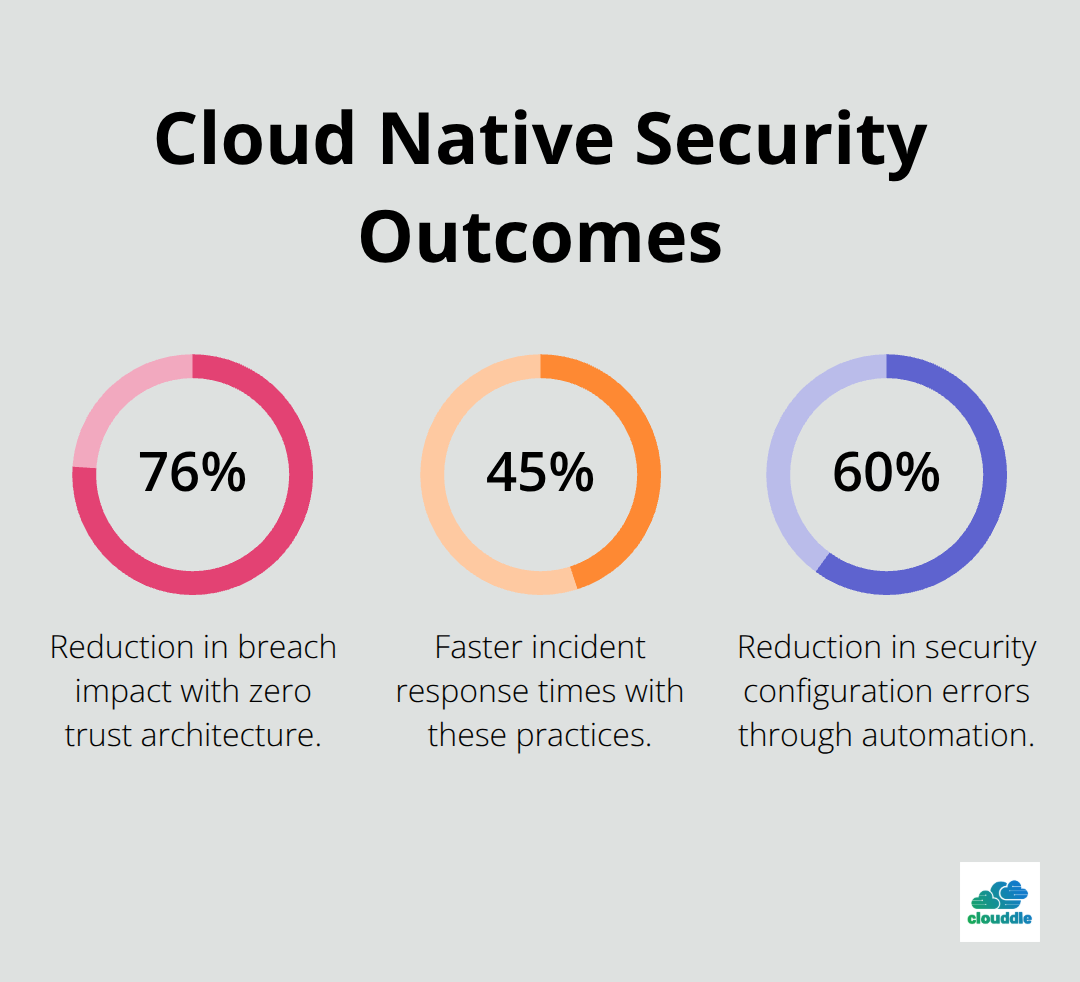
Organizations that adopt these practices see 45% faster incident response times and 60% reduction in security configuration errors. The automation tools and runtime protection systems outlined here eliminate manual processes that cause most cloud security failures. Teams must prioritize container image scanning, service mesh security, and API gateway hardening as foundational elements.
Success requires commitment to policy-as-code, continuous monitoring, and identity-based access controls. The investment in proper tooling and processes pays dividends through reduced security incidents and improved compliance posture (which traditional security approaches struggle to achieve). At Clouddle, we help organizations build robust cloud native architectures through our managed IT and security services.


