Cybersecurity threats cost businesses $4.45 million per breach on average in 2023. Most attacks succeed because employees lack proper security training.
At Clouddle, we’ve seen how effective cybersecurity awareness training transforms workplace security culture. The right program reduces human error incidents by up to 70% within the first year.
What Components Make Training Effective
Effective cybersecurity awareness training requires three core elements that work together to create behavioral change. The foundation starts with comprehensive content coverage that addresses real-world threats employees face daily. Phishing attacks account for 36% of all data breaches according to Verizon’s Data Breach Investigations Report, which makes email security training essential. Social engineering tactics, password management, and mobile device security form the next tier of topics. Business email compromise resulted in $2.9 billion in losses for U.S. businesses in 2023, which highlights why targeted training on executive impersonation and wire fraud attempts saves organizations millions.
Training Methods That Drive Results
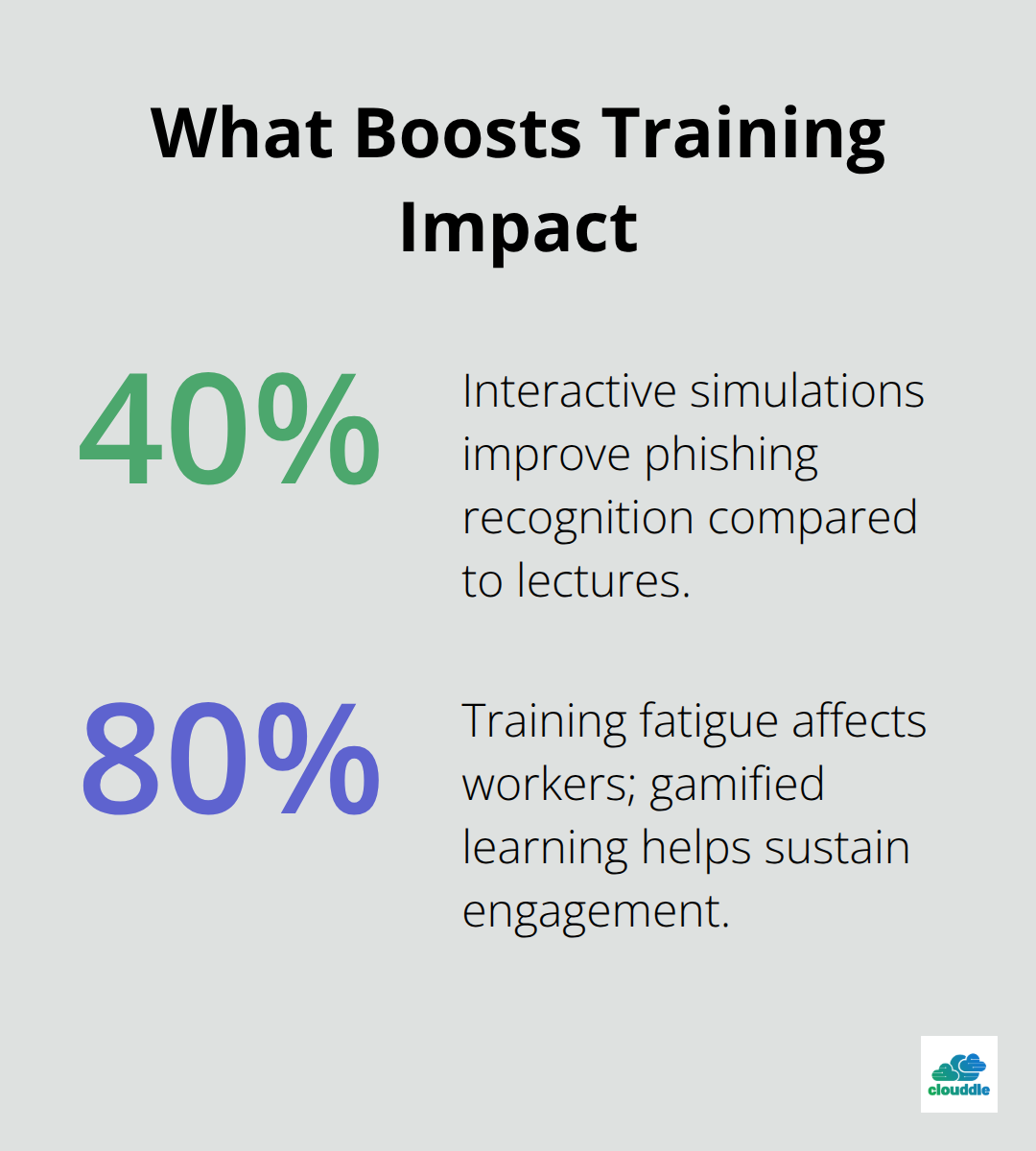
Interactive simulations outperform traditional lecture-style training by 40% in phishing recognition rates. Gamified learning experiences increase employee engagement significantly while they reduce training fatigue that affects 80% of workers (according to Malwarebytes research). Microlearning modules delivered in 10-15 minute sessions improve retention compared to hour-long sessions that overwhelm participants.
Real-world scenarios tailored to specific job roles create relevance that generic training lacks. AI-powered adaptive learning paths adjust content difficulty based on individual performance and target weaknesses that standard programs miss.
Optimal Training Schedule and Duration
Monthly micro-sessions of 15-20 minutes maintain security awareness without they disrupt productivity. Quarterly phishing simulations reinforce learning through practical application, with themes refreshed to match current threat landscapes. Annual comprehensive reviews cover threats like deepfake technology, which has increased tenfold in recent years (AI-driven threats now require advanced employee training). Organizations that implement 90-day intensive training cycles see phishing susceptibility decrease by over 40%. Continuous reinforcement through brief weekly security tips keeps cybersecurity top-of-mind without it overwhelms employees with lengthy sessions.
Content Customization for Maximum Impact
Role-based training modules address specific vulnerabilities that different departments face. Finance teams need specialized training on wire fraud and invoice manipulation schemes. HR departments require education on social engineering attacks that target employee data. IT staff need advanced training on technical threats and incident response procedures. This targeted approach increases relevance and improves retention rates compared to one-size-fits-all programs.
Once you establish these foundational components, the next step involves developing a comprehensive program that addresses your organization’s specific security knowledge gaps and creates measurable outcomes through regular audits and risk assessment.
How Do You Build a Training Program That Actually Works
Start With Baseline Assessment
Effective cybersecurity awareness training programs begin with baseline phishing simulations that reveal current vulnerabilities. Organizations that conduct these assessments first see 40% better results compared to programs launched without preliminary testing. Run simulated attacks across all departments to identify which teams click on malicious links most frequently. Finance departments typically show higher vulnerability rates due to their exposure to wire fraud attempts, while IT teams generally perform better but still need targeted training on advanced persistent threats. This data becomes the foundation for role-specific content that addresses actual weaknesses rather than generic security concepts.
Create Content That Mirrors Real Threats
Effective training content must mirror real attacks that employees encounter daily. Generic modules about password security fail because they don’t address specific threats like credential stuffing attacks. Interactive scenarios work best when they replicate actual phishing emails your organization receives. Create modules that show employees how attackers research targets through LinkedIn and social media before they launch spear-phishing campaigns.

Include voice phishing simulations since these attacks target remote workers through fake IT support calls.
Update Content Based on Current Intelligence
Content should update monthly to reflect current threat intelligence, with quarterly refreshes of phishing simulation themes to prevent employees from recognizing patterns. Real-world scenarios tailored to specific job roles create relevance that generic training lacks. Finance teams need specialized modules on wire fraud and invoice manipulation schemes. HR departments require education on social engineering attacks that target employee data. IT staff need advanced training on technical threats and incident response procedures.
Track Performance Through Specific Metrics
Set specific targets like reducing phishing click rates from baseline levels to under 10% within six months. Track incident reporting rates because organizations with strong reporting cultures see 67% faster threat detection (according to IBM Security research). Monitor training completion rates by department and correlate these with actual security incidents to identify gaps. Measure time-to-report for suspicious emails, trying for reports within 60 seconds of receiving threats. Companies that achieve this response time contain breaches 200 days faster than those with slower reporting.
Establish monthly dashboards that show click rates, completion percentages, and incident trends to maintain executive support and budget approval. These metrics provide the foundation for the next phase: rolling out your training initiative across different departments while you track progress and adapt content based on emerging threats.
How Do You Execute Training Across Your Organization
Department-Specific Rollout Strategy
Start with high-risk departments first rather than organization-wide launches that dilute focus and resources. Finance teams should receive priority training since they handle wire transfers and sensitive financial data that attracts Business Email Compromise attacks. Launch training for these teams two weeks before other departments to establish success metrics and refine content. HR departments follow next because they manage employee data that social engineers target through fake recruitment emails and benefits inquiries. IT teams require specialized modules on advanced persistent threats and incident response procedures that differ significantly from general employee training. Remote workers need dedicated sessions since 20% of security breaches involve remote employees according to Malwarebytes research. Schedule training sessions during peak productivity hours for each department rather than convenient IT windows that reduce engagement.
Real-Time Progress Monitoring and Intervention
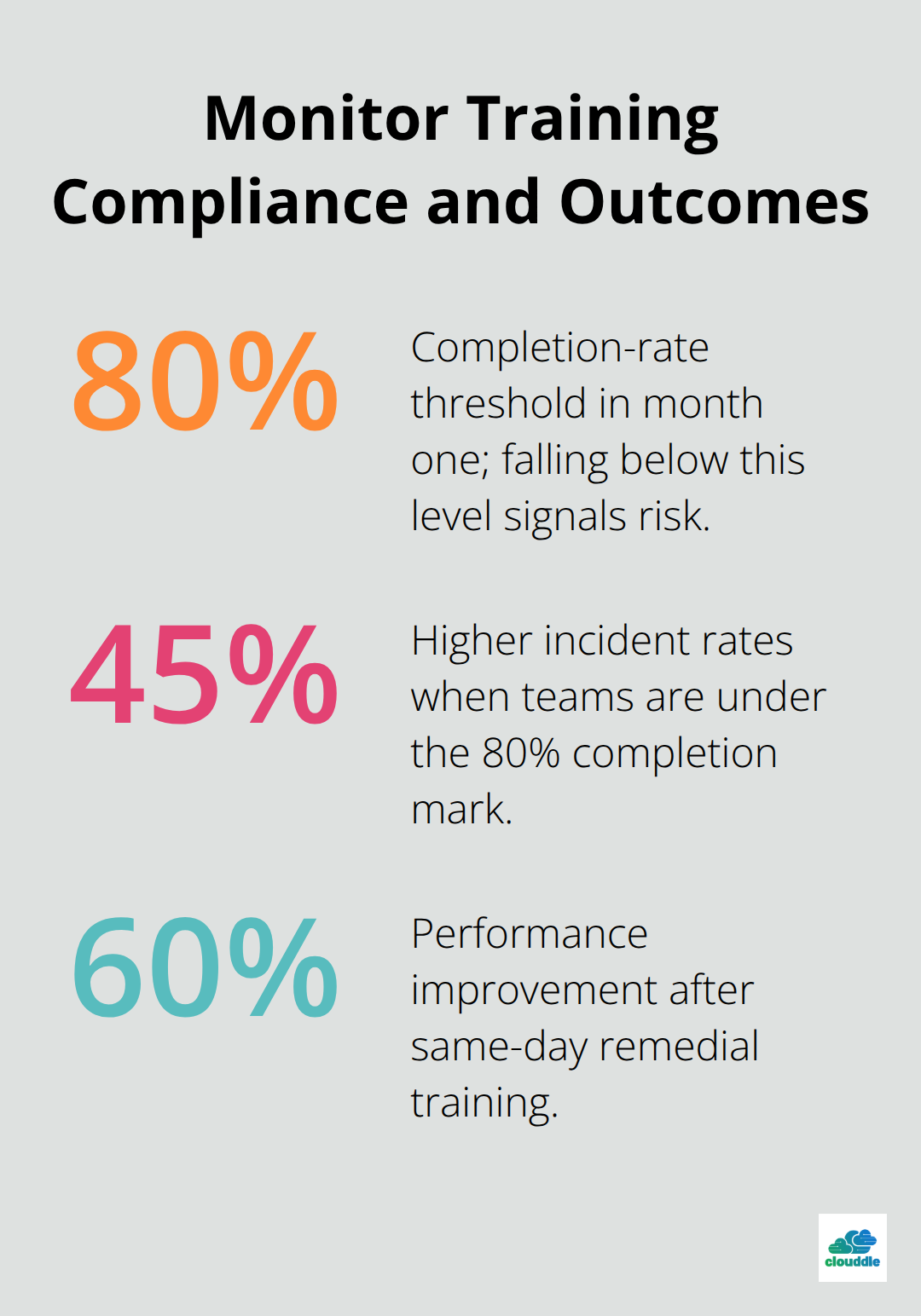
Track completion rates daily through automated dashboards that flag departments that fall behind schedule. Organizations with completion rates below 80% within the first month see 45% higher incident rates compared to fully compliant teams. Set automatic email reminders for employees who miss training deadlines, escalate to managers after 48 hours of non-compliance. Monitor phishing simulation click rates in real-time and trigger immediate remedial training for employees who fail simulations. Companies that implement same-day remedial training see 60% better performance in subsequent tests.
Weekly progress reports to department heads maintain accountability and identify teams that need additional support or modified delivery methods.
Threat-Driven Content Updates
Update training content monthly based on current threat intelligence feeds rather than annual reviews that leave employees vulnerable to new attack vectors. Deepfake attacks have increased tenfold recently, which requires immediate module updates on voice and video manipulation detection. Subscribe to threat intelligence services that provide weekly briefings on emerging attack patterns that affect your industry sector. Healthcare organizations face 55% more breaches according to Bitglass, which requires specialized content on HIPAA compliance and medical record protection. Financial services need quarterly updates on cryptocurrency fraud and digital payment manipulation schemes. Create rapid-response training modules that deploy within 72 hours of major security incidents that affect similar organizations. This agile approach keeps training relevant while it maintains employee engagement through current, actionable content that addresses real threats they might encounter. Conducting regular risk assessments helps identify which threats require immediate training updates.
Final Thoughts
Successful cybersecurity awareness training implementation requires three fundamental steps: baseline assessment to identify vulnerabilities, role-specific content creation that addresses real threats, and continuous monitoring with monthly updates. Organizations that follow this structured approach see 70% reduction in security incidents within the first year. Companies achieve these results when they commit to consistent execution across all departments.
Consistent training programs deliver measurable long-term benefits beyond immediate threat reduction. Companies with ongoing cybersecurity awareness training report $177,708 return on investment through prevented breaches and reduced incident response costs. Employee confidence increases by 17% when workers understand security protocols (which directly improves productivity and reduces fear-based decision making that leads to security mistakes).
Organizations must establish quarterly threat intelligence reviews to keep content current with emerging attack vectors. Annual program assessments measure effectiveness and identify new training needs that evolve with the threat landscape. Clouddle offers comprehensive managed IT and security services that complement training programs with robust technical safeguards.


