Network security is no longer a luxury-it’s a necessity. In today’s digital landscape, businesses face an ever-growing array of cyber threats that can compromise sensitive data and disrupt operations.
At Clouddle, we’ve seen firsthand how effective network security methods can make or break an organization’s defenses. This post will guide you through essential strategies to fortify your network and protect your valuable assets from potential breaches.
What is Network Security?
The Foundation of Digital Defense
Network security forms the cornerstone of modern business operations. It encompasses a set of practices and technologies that protect the integrity, confidentiality, and accessibility of computer networks and data. Robust network security can determine the difference between a thriving business and one exposed to costly breaches.
The Dynamic Threat Landscape
The cybersecurity threat landscape continues to evolve rapidly. IBM’s global Cost of a Data Breach Report 2025 provides up-to-date insights into cybersecurity threats and their financial impacts on organizations. This emphasizes the urgent need for effective network security measures.
Common threats include:
- Malware infections
- Phishing attacks
- Ransomware
However, external threats aren’t the only concern. Insider threats (both malicious and accidental) pose significant risks.
Constructing a Robust Security Strategy
A comprehensive network security strategy requires multiple facets. It begins with a thorough risk assessment to identify vulnerabilities in your current setup. Organizations should conduct these assessments regularly (at least annually) to keep pace with new threats and technologies.
The next step involves implementing strong access controls. This includes multi-factor authentication, which can prevent more than 99.9% of account compromise attacks.

Regular software updates and patch management play a vital role. The 2017 WannaCry ransomware attack (which affected over 200,000 computers across 150 countries) exploited a vulnerability for which a patch had been available for months.
Employee training stands as another critical component. The human element often represents the weakest link in security. Regular, engaging security awareness programs can significantly reduce the risk of successful phishing attacks and other social engineering tactics.
Advanced Security Measures
As threats evolve, defenses must adapt. Network segmentation has gained popularity as a strategy. This approach divides your network into smaller, isolated segments to contain potential breaches and limit their impact. It aligns with the Zero Trust security model, which operates on the principle of “never trust, always verify.”
Artificial Intelligence (AI) and Machine Learning (ML) revolutionize threat detection. These technologies analyze vast amounts of data in real-time, identifying patterns and anomalies that might indicate a security threat.
The Role of Managed Security Services
Many organizations turn to managed security service providers to navigate the complex landscape of network security. These providers offer expertise, round-the-clock monitoring, and access to cutting-edge technologies that might be out of reach for smaller businesses.
As we move forward, the next chapter will explore essential network security methods in detail, providing practical steps to fortify your digital defenses against an ever-evolving threat landscape.
How to Implement Essential Network Security Methods
At Clouddle, we have identified key network security methods that form the backbone of a robust defense strategy. These methods work together to create multiple layers of protection, which significantly reduce the risk of successful cyber attacks.
Firewalls and Intrusion Detection Systems: Your First Line of Defense
Firewalls act as a barrier between your internal network and external threats. They monitor incoming and outgoing traffic, allowing or blocking data packets based on predefined security rules. Modern Next-Generation Firewalls (NGFWs) have more layers of security built into them, to protect against more sophisticated threats. Crucially, they go beyond the static security measures of traditional firewalls.
Intrusion Detection Systems (IDS) complement firewalls by monitoring network traffic for suspicious activities. They alert security teams to potential threats, which allows for rapid response.
Secure Remote Access with VPNs
Virtual Private Networks (VPNs) create encrypted tunnels for secure communication over public networks. They protect data in transit, especially for remote workers.
When you select a VPN, consider factors like encryption strength, server locations, and connection speeds. Some VPNs offer additional features like split tunneling, which allows you to route only specific traffic through the VPN while other traffic uses the regular internet connection.
Strengthening Access Controls
Multi-factor authentication (MFA) adds an extra layer of security beyond passwords. It requires users to provide two or more verification factors to gain access to a resource.
Implement MFA across all critical systems and applications. Try to use a combination of something the user knows (password), something they have (security token), and something they are (biometric verification) for the strongest protection.
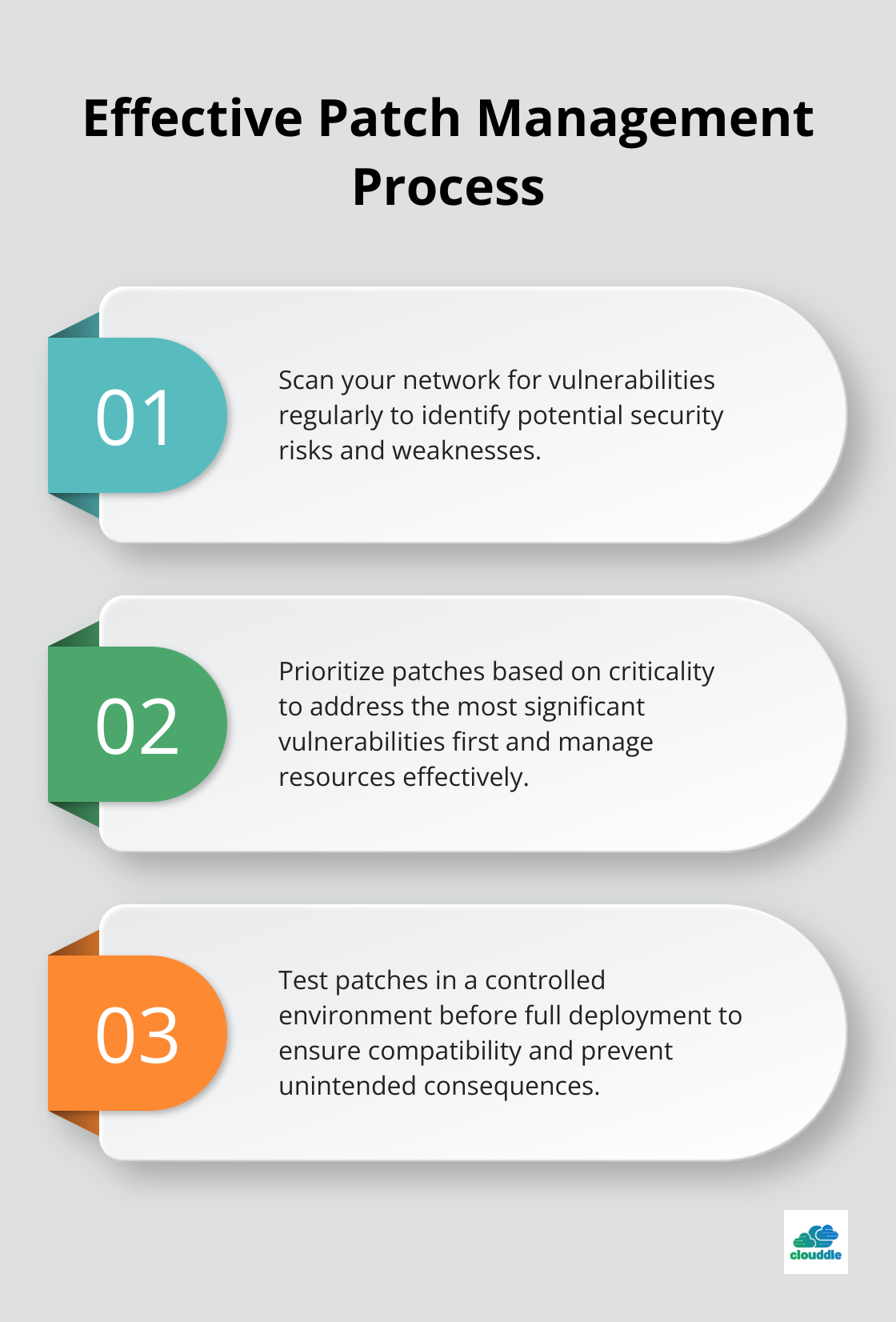
Keeping Systems Up-to-Date
Regular software updates and patch management close security vulnerabilities. The WannaCry ransomware attack in 2017 exploited a vulnerability for which a patch had been available for months.
Establish a systematic approach to patch management:
The Human Factor: Employee Training and Awareness
Even the most sophisticated technical defenses can be undermined by human error. Regular security awareness training creates a security-conscious culture within your organization.
Develop a comprehensive training program that covers topics like:
- Recognizing phishing attempts
- Safe browsing practices
- Proper handling of sensitive data
- Password hygiene
- Social engineering tactics
Make training engaging and relevant. Use real-world examples and simulations to help employees understand the potential consequences of security lapses. Regular phishing simulations help gauge the effectiveness of your training and identify areas for improvement.
While these essential methods form a solid foundation for network security, advanced techniques can further enhance your defenses. In the next section, we’ll explore cutting-edge strategies that take your security posture to new heights.
How Advanced Techniques Enhance Your Network Security
At Clouddle, we observe that advanced techniques significantly elevate defense strategies beyond essential network security methods. These cutting-edge approaches address the evolving threat landscape and provide robust protection against sophisticated attacks.
Network Segmentation: Divide and Conquer
Network segmentation involves dividing a computer network into smaller parts in order to improve security and reduce your attack surface. This strategy limits the potential damage of a breach by containing it within a single segment.
To implement effective network segmentation:
- Identify and classify your assets based on sensitivity and criticality.
- Create separate network segments for different asset classes.
- Implement strict access controls between segments.
- Monitor traffic between segments to detect unusual patterns.
Microsegmentation takes this concept further by creating even smaller network segments, sometimes down to individual workloads. While more complex to implement, microsegmentation offers granular control over network traffic, significantly reducing the attack surface.
Zero Trust: Never Trust, Always Verify
The Zero Trust model assumes that no user, device, or network should be trusted by default, even if they’re inside the network perimeter. This approach gains traction as organizations seek to improve their security posture.
Key steps to implement Zero Trust include:

AI and ML: Intelligent Threat Detection
Artificial Intelligence (AI) and Machine Learning (ML) revolutionize threat detection. These technologies analyze vast amounts of data in real-time, identifying patterns and anomalies that might indicate a security threat.
Some practical applications include:
- Behavioral analysis to detect insider threats.
- Automated threat hunting to proactively identify potential risks.
- Predictive analytics to anticipate future attack vectors.
Cloud Security: Protecting Your Digital Assets
As more businesses move to the cloud, securing cloud environments becomes essential.
To enhance cloud security:
- Use cloud-native security tools provided by your cloud service provider.
- Implement strong identity and access management (IAM) policies.
- Encrypt data both in transit and at rest.
- Regularly audit your cloud environment for misconfigurations.
Encryption: The Last Line of Defense
Encryption remains a critical component of data protection. It ensures that even if data is intercepted, it remains unreadable without the decryption key.
To maximize the effectiveness of encryption:
- Use strong encryption algorithms (e.g., AES-256 for symmetric encryption).
- Implement end-to-end encryption for sensitive communications.
- Secure encryption keys with robust key management practices.
- Encrypt data both in transit and at rest.
These advanced techniques, when combined with essential security methods, create a formidable defense against cyber threats. Regular assessments and updates to your security strategy help stay ahead of evolving threats.
Final Thoughts
Network security methods form the foundation of a robust defense strategy in today’s digital landscape. From firewalls to AI-driven threat detection, each layer contributes to a comprehensive security posture. The importance of a multi-layered approach provides defense in depth against an ever-evolving array of cyber threats.
We anticipate several trends to shape the future of network security. Zero Trust architectures will likely accelerate, while AI and machine learning will play a more significant role in threat detection and response. Cloud-native security solutions will become increasingly sophisticated and integrated as cloud adoption continues to grow.
At Clouddle, we understand the critical importance of network security in today’s business environment. Our Network as a Service (NaaS) solution combines networking, entertainment, and security features to provide seamless operations and enhanced protection for businesses. We encourage all organizations to regularly assess their network security methods and proactively implement stronger security measures.


