Network security methods are the backbone of protecting your digital assets in an increasingly connected world. With cyber threats evolving rapidly, it’s crucial to stay ahead of potential vulnerabilities.
At Clouddle, we’ve seen firsthand how implementing effective security measures can make or break an organization’s defenses. This guide will walk you through essential techniques, best practices, and emerging trends to fortify your network against modern threats.
Essential Network Security Methods
At Clouddle, we have identified four key methods that form the foundation of robust network security. These techniques, when implemented correctly, significantly reduce the risk of cyber attacks and data breaches.
Firewalls and Intrusion Detection Systems
Firewalls act as the first line of defense against unauthorized access. They filter incoming and outgoing network traffic based on predetermined security rules. Modern Next-Generation Firewalls (NGFWs) offer advanced features like deep packet inspection and application-level filtering.
Intrusion Detection Systems (IDS) complement firewalls by monitoring network traffic for suspicious activities. They alert security teams to potential threats, allowing for quick response.
Virtual Private Networks (VPNs)
VPNs encrypt data transmitted over public networks, creating a secure tunnel for remote access to corporate resources. This is particularly important in today’s hybrid work environment.
When you select a VPN solution, prioritize those with strong encryption protocols like OpenVPN or WireGuard. Also, ensure the VPN supports split-tunneling to optimize performance for non-sensitive traffic.
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide two or more verification factors to gain access. This significantly reduces the risk of unauthorized access, even if passwords are compromised. MFA prevented 100% of automated attacks, 96% of bulk phishing attacks, and 76% of targeted attacks.
Implement MFA across all critical systems and applications. Try using adaptive MFA, which adjusts authentication requirements based on user behavior and risk factors.

Regular Software Updates and Patch Management
Unpatched vulnerabilities are a common entry point for cybercriminals. Establish a rigorous patch management process to ensure all systems and software are up-to-date. Implementing patches promptly can significantly reduce the likelihood of data breaches.
Automate patch management where possible and prioritize critical security updates. Conduct regular vulnerability assessments to identify and address potential weaknesses proactively.
These essential methods create a strong foundation for your network security strategy. However, security is an ongoing process that requires constant vigilance and adaptation. In the next section, we’ll explore best practices for implementing these methods effectively and maintaining a robust security posture.
How to Implement Network Security Best Practices
Network security implementation requires more than just the right tools; it demands a comprehensive strategy that addresses all aspects of your organization’s digital landscape. Let’s explore key practices that will elevate your network security implementation.
Conduct Regular Security Audits
Security audits form the cornerstone of a robust network defense strategy. They help identify vulnerabilities before malicious actors can exploit them. We recommend comprehensive audits at least quarterly, with more frequent checks for critical systems.
Use a combination of automated scanning tools and manual penetration testing during these audits. Automated tools quickly identify common vulnerabilities, while manual testing uncovers more complex issues that automated systems might miss. A recent study has shown the effectiveness of cybersecurity audits in improving cyber risk management.
Prioritize Employee Training
Employees often serve as the first line of defense against cyber threats. A well-informed workforce can significantly reduce the risk of successful attacks. Implement a comprehensive security awareness program that covers topics like phishing recognition, password hygiene, and safe browsing practices.
Make training engaging and relevant. Use real-world examples and interactive simulations to emphasize the importance of security practices. Consider gamification elements to increase participation and retention.
Segment Your Network
Network segmentation limits the spread of potential breaches. Dividing your network into smaller, isolated segments contains threats and minimizes damage. This approach proves particularly important for organizations dealing with sensitive data or those subject to regulatory compliance.
Start by mapping your network and identifying critical assets. Create separate segments for different departments or data types, and implement strict access controls between segments. Use next-generation firewalls to monitor and control traffic between segments.
Develop a Robust Incident Response Plan
Security incidents can still occur despite your best efforts. A well-defined incident response plan can significantly reduce the impact of a breach. Your plan should outline clear procedures for detecting, containing, and mitigating security incidents.
Assign specific roles and responsibilities to team members, and conduct regular drills to ensure everyone knows their part. Include procedures for communication (both internal and external) to manage the incident effectively.
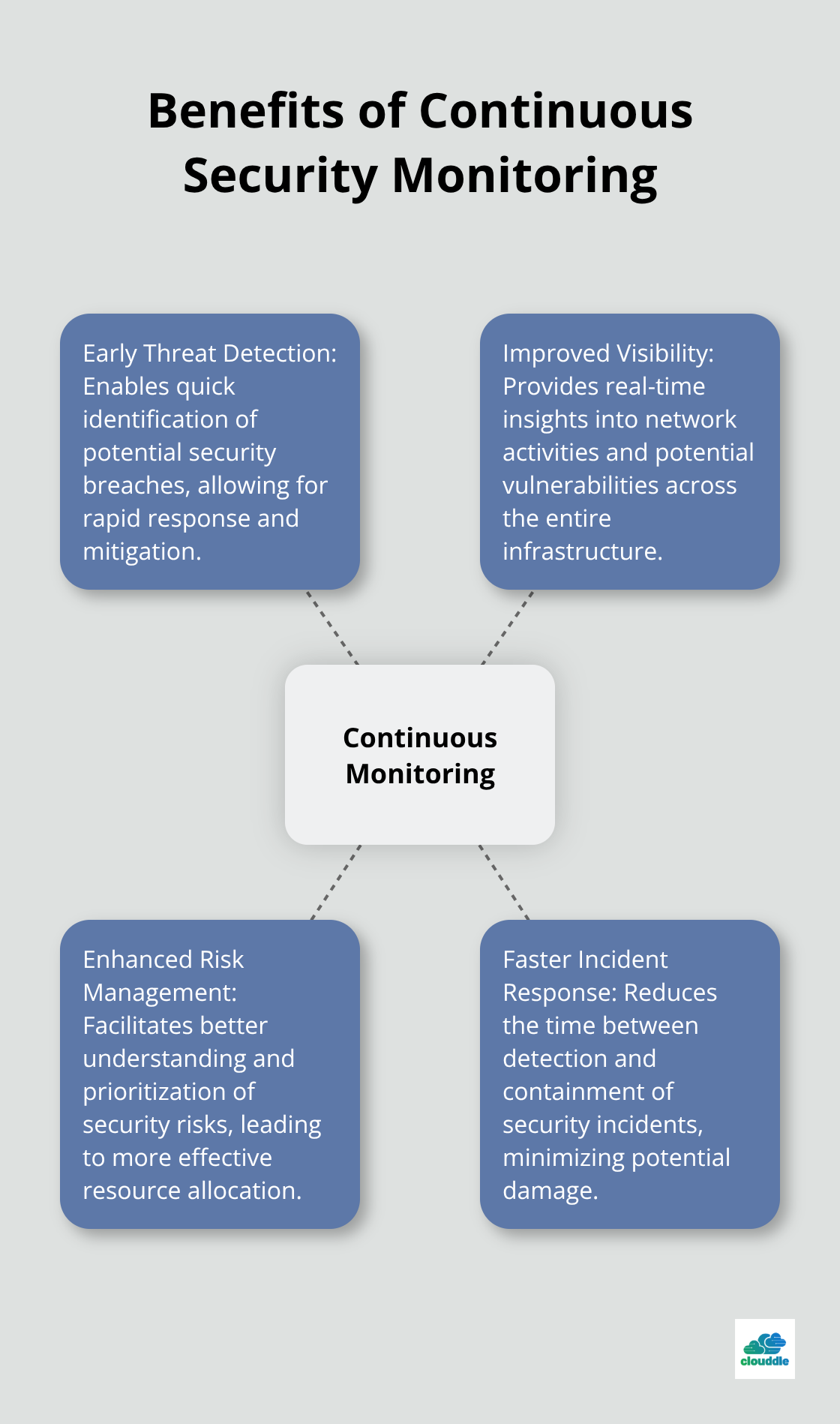
Implement Continuous Monitoring
Continuous security monitoring provides earlier threat detection and response, and improves visibility into current posture and risk management. Implement a Security Information and Event Management (SIEM) system to collect and analyze log data from across your network. This approach enables you to identify and respond to potential threats quickly.
Set up alerts for suspicious activities and automate responses where possible. Try to correlate events across different systems to identify complex attack patterns. Continuous monitoring can help in reducing the time to detect and contain potential security breaches.
These best practices form a solid foundation for your network security strategy. However, the landscape of cyber threats continues to evolve. In the next section, we’ll explore emerging trends in network security that will shape the future of digital defense.
What Are the Latest Network Security Trends?
The landscape of network security constantly evolves, and staying ahead of the curve is essential for robust protection. We monitor the latest developments to ensure our clients have access to cutting-edge security solutions. Let’s explore some of the most impactful trends shaping the future of network security.
Zero Trust Architecture: Trust Nothing, Verify Everything
Zero Trust represents a fundamental shift in how we approach security. This model assumes no user or device is trustworthy by default, even if they’re already inside the network perimeter. A recent study by Microsoft found that organizations which implemented a Zero Trust strategy were 50% more likely to successfully mitigate a breach.
To implement Zero Trust effectively:
- Start with identity: Implement strong authentication methods across all users and devices.
- Segment access: Use micro-segmentation to limit lateral movement within your network.
- Continuously monitor: Implement real-time monitoring and analytics to detect anomalies quickly.
AI-Powered Threat Detection: Staying One Step Ahead
Artificial Intelligence (AI) and Machine Learning (ML) revolutionize threat detection and response. These technologies analyze vast amounts of data in real-time, identifying patterns and anomalies that human analysts might miss.
Nearly two-thirds of organizations think that AI will help identify critical threats. To leverage AI in your security strategy:

Cloud-Native Security: Protecting Your Digital Transformation
As more organizations move their operations to the cloud, traditional security measures no longer suffice. Cloud-native security solutions protect cloud-based assets and workloads effectively.
Gartner predicts that by 2025, 99% of cloud security failures will be the customer’s fault. To avoid becoming part of this statistic:
- Implement Cloud Security Posture Management (CSPM) tools to continuously monitor your cloud environment.
- Use Cloud Access Security Brokers (CASBs) to enforce security policies across multiple cloud services.
- Adopt a DevSecOps approach to integrate security into your cloud development pipeline.
Securing the Internet of Things: Protecting the Expanding Attack Surface
The proliferation of IoT devices creates new challenges for network security. These devices often lack built-in security features and can serve as entry points for attackers. A study by Unit 42 found that 98% of all IoT device traffic is unencrypted (exposing personal and confidential data).
To secure your IoT ecosystem:
- Implement network segmentation to isolate IoT devices from critical systems.
- Use IoT-specific security solutions that monitor and protect these devices.
- Regularly update and patch IoT devices to address known vulnerabilities.
These trends continue to shape the network security landscape. It’s important to stay informed and adapt your strategies accordingly. Try to implement robust security solutions that address these emerging challenges to stay ahead of potential threats.
Final Thoughts
Network security methods form the foundation of a robust digital defense strategy. Organizations must implement a multi-faceted approach that includes firewalls, VPNs, multi-factor authentication, and regular software updates. These techniques, combined with best practices like security audits and employee training, create a strong security posture against evolving cyber threats.
The future of network security will involve emerging trends such as Zero Trust architecture, AI-powered threat detection, and cloud-native security solutions. Organizations need to stay informed about these advancements and adapt their strategies to address new vulnerabilities and attack vectors. This proactive approach will help safeguard valuable assets against potential threats in tomorrow’s digital landscape.
We at Clouddle offer managed IT and security services that leverage cutting-edge technologies to protect businesses across various industries. Our solutions combine networking, entertainment, and security to enable organizations to focus on growth while we handle the complexities of maintaining a secure digital infrastructure. The key to success lies in adopting new technologies and fostering a culture of security awareness throughout your organization.


