Network security is the backbone of modern digital infrastructure. At Clouddle, we’ve seen firsthand how crucial it is for businesses to protect their data and systems from ever-evolving threats.
In this post, we’ll explore real-world network security examples and provide practical strategies for implementing robust protection. From financial institutions to healthcare providers, we’ll examine how different industries tackle their unique security challenges.
What Are Network Security Essentials?
The Foundation of Digital Defense
Network security refers to the technologies, policies, people, and procedures that defend any communication infrastructure from cyberattacks, unauthorized access, and other threats. It protects an organization’s data, systems, and reputation from cyber threats. However, effective network security extends beyond installing a firewall; it requires a multi-faceted approach that adapts to the ever-changing threat landscape.
Building Blocks of a Secure Network
A solid network security strategy begins with a thorough understanding of assets and potential vulnerabilities. Regular network audits can help organizations identify critical gaps in data security and reduce the threat of security compromises.
Organizations must implement a layered defense, which includes:
- Firewalls: Hardware and software firewalls serve as the first line of defense.
- Intrusion Detection Systems (IDS): These tools monitor network traffic for suspicious activity.
- Virtual Private Networks (VPNs): VPNs provide secure remote access, especially important with the rise of remote work.
- Encryption: This technology protects data both in transit and at rest.
- Access Control: The principle of least privilege limits potential damage from compromised accounts.
Countering Emerging Threats
The threat landscape continues to evolve rapidly. In 2025, we observe a surge in AI-powered attacks. These sophisticated threats adapt to traditional security measures, making them particularly dangerous. To combat this, organizations need to invest in AI-driven security solutions that detect and respond to threats in real-time.
The Internet of Things (IoT) presents another growing concern. With billions of connected devices, each one becomes a potential entry point for attackers. Network segmentation to isolate IoT devices can significantly reduce this risk.
The Human Element in Network Security
While technology plays a critical role, the human factor remains a significant vulnerability. Social engineering attacks, such as phishing, continue to be a primary vector for breaches.
To address this, organizations must prioritize ongoing security awareness training. This training should go beyond annual presentations and focus on creating a culture of security where every employee understands their role in protecting the network.
The Role of Resilience
Implementing these network security essentials focuses not just on prevention, but on resilience. When (not if) an attack occurs, a well-prepared organization can detect, respond, and recover quickly, minimizing damage and maintaining business continuity.
As we move forward, let’s examine how these principles translate into real-world implementations across various industries.
How to Implement Effective Network Security
Fortify Your Perimeter and Internal Defenses
Start with the implementation of next-generation firewalls (NGFWs). These advanced systems inspect traffic at the application layer, providing deeper insights into potential threats. Organizations using DPI report a 50% reduction in security incidents over traditional filtering methods.

Combine your firewall with an intrusion detection and prevention system (IDPS) to actively monitor and block suspicious activities.
Strengthen Access Control Measures
Implement multi-factor authentication (MFA) across all access points. Take it a step further and adopt a zero-trust architecture that verifies every user and device, regardless of location. This approach can reduce the risk of data breaches, save on cybersecurity costs, support regulatory compliance, manage third-party risks, secure remote work, and enhance overall security.
Use role-based access control (RBAC) to ensure users only have access to the resources they need. This principle of least privilege can limit the potential damage from compromised accounts.
Conduct Regular Security Assessments
Schedule quarterly vulnerability assessments and annual penetration tests to identify weaknesses before attackers do.
Use automated scanning tools, but don’t rely on them exclusively. Manual testing by skilled professionals can uncover complex vulnerabilities that automated tools might miss.
Invest in Continuous Employee Training
Your employees are both your greatest asset and your biggest potential vulnerability. Implement a comprehensive security awareness program that goes beyond annual compliance training. Use simulated phishing attacks to test and educate employees.
Make security part of your company culture. Encourage reporting of suspicious activities and reward security-conscious behavior.
Network security requires an ongoing process, not a one-time implementation. Stay informed about emerging threats and continuously adapt your strategies. These best practices will significantly enhance your organization’s security posture and resilience against cyber threats. In the next section, we’ll explore real-world examples of successful network security implementations across various industries.
Real-World Network Security Success Stories
Financial Giant Fortifies Defenses
A major financial institution faced increasing cyber threats targeting sensitive customer data. They implemented a multi-layered security approach that dramatically reduced their risk exposure.
The bank deployed next-generation firewalls with deep packet inspection, which provide capabilities beyond a traditional, stateful firewall. They also implemented a zero-trust architecture, which allows users to have access to resources they need to complete their job, in order to have protection.
The institution invested heavily in employee training. They launched a gamified security awareness program that increased phishing detection rates from 62% to 94% within six months.
Healthcare Provider Achieves HIPAA Compliance
A regional healthcare network struggled with HIPAA compliance and protecting patient data. They overhauled their network security strategy with impressive results.
The provider implemented network segmentation, which isolated systems containing patient health information (PHI) from the rest of the network. This reduced the attack surface for sensitive data by 70%.
They also deployed an AI-powered intrusion detection system that identified and responded to threats in real-time. This system thwarted a ransomware attack within minutes of its initiation, potentially saving millions in damages and HIPAA violation fines.
E-commerce Platform Repels DDoS Attacks
An up-and-coming e-commerce company faced repeated Distributed Denial of Service (DDoS) attacks that threatened to cripple their business. They implemented a robust DDoS protection strategy that ensured business continuity.
The company partnered with a cloud-based DDoS mitigation service that absorbed and filtered malicious traffic before it reached their servers. This solution successfully mitigated a 1.2 Tbps attack (the largest the company had ever faced).
They also implemented rate limiting and traffic analysis tools to distinguish between legitimate spikes in traffic and potential DDoS attempts. This reduced false positives by 95%, ensuring a smooth customer experience during peak shopping periods.
Small Business Secures Remote Work
A small marketing agency transitioned to remote work and needed to secure their operations. They implemented a comprehensive security solution that protected their distributed workforce.
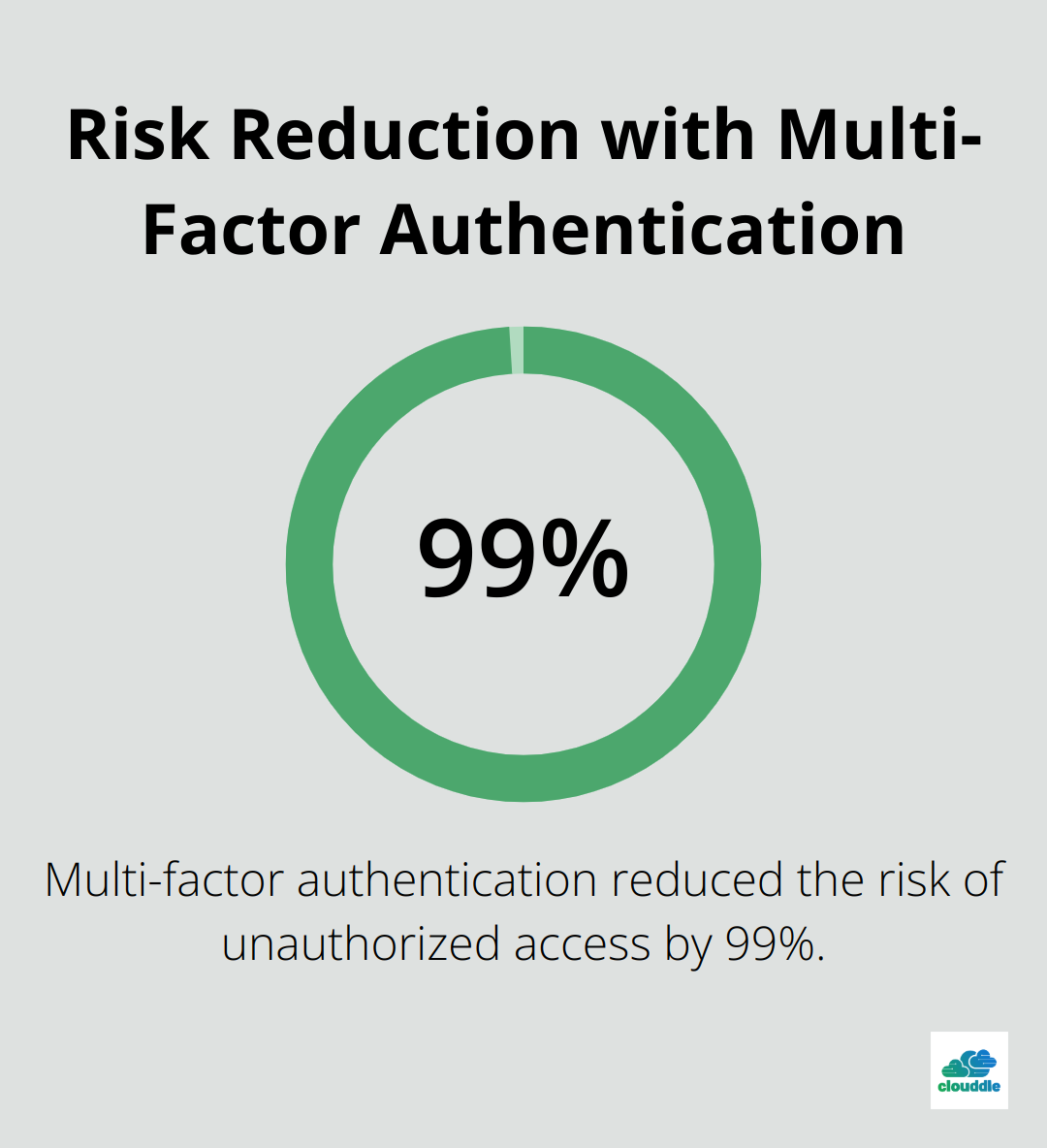
The agency set up a Virtual Private Network (VPN) for secure remote access. They also enforced multi-factor authentication for all employee accounts, reducing the risk of unauthorized access by 99%.
To protect against phishing attacks, the company implemented advanced email filtering and conducted regular phishing simulations. These measures improved their employees’ ability to identify and report suspicious emails by 80%.
Manufacturing Firm Protects Industrial Control Systems
A mid-sized manufacturing firm needed to secure their industrial control systems (ICS) from cyber threats. They implemented a tailored security strategy that safeguarded their operations.
The firm segmented their network to isolate ICS from the corporate network. They also implemented strict access controls and continuous monitoring for these critical systems.
The company deployed specialized ICS security tools that could detect anomalies in industrial processes. This proactive approach helped them identify and mitigate a potential breach attempt before it could impact production.
Final Thoughts
Network security examples demonstrate the importance of tailored strategies across diverse industries. Organizations must implement robust firewalls, adopt zero-trust architectures, and conduct regular security assessments to protect their digital assets effectively. Continuous employee training remains a cornerstone of any comprehensive security approach, as human factors often present significant vulnerabilities.
Emerging trends will shape the future of network security. AI and machine learning will play an increasingly vital role in threat detection and response, while edge computing and 5G networks will create new security challenges. Quantum computing holds the potential to revolutionize encryption methods, though its full impact remains to be seen.
At Clouddle, we recognize the critical role of robust network security in today’s digital landscape. Our managed IT and security services help businesses stay ahead of evolving threats, ensuring networks remain protected against the latest cyber risks. We empower organizations to focus on their core business while we handle the complexities of network security.


