Network security standards are the backbone of a robust cybersecurity strategy. They provide a framework for organizations to protect their digital assets from ever-evolving threats.
At Clouddle, we understand the critical role these standards play in safeguarding sensitive information and maintaining business continuity. This guide will walk you through the essential steps to implement network security standards effectively, ensuring your organization stays ahead of potential cyber risks.
What Are Network Security Standards?
Definition and Importance
Network security standards are comprehensive guidelines that organizations use to protect their digital infrastructure from cyber threats. These standards serve as essential tools for maintaining a robust security posture in today’s interconnected world.
Key Network Security Standards
Three widely recognized standards form the foundation of many network security strategies:
- ISO 27001: This standard provides a systematic approach to managing sensitive company information.
- NIST Cybersecurity Framework: The CSF is a flexible framework that is intended to be tailored for use by all organizations regardless of size.
- CIS Controls: These controls present a prioritized set of actions to mitigate the most prevalent cyber-attacks.
Tangible Benefits of Implementation
Organizations that implement these standards often see significant improvements in their security posture. For example:
- Implementing ISO 27001 has shown to reduce security incidents by up to 70% in public sector organisations, underscoring its effectiveness in enhancing cybersecurity measures.

Customizing Standards for Your Organization
While these standards provide excellent guidelines, it’s important to adapt them to your specific business needs. A thorough risk assessment (which identifies your most critical assets and vulnerabilities) allows you to prioritize your security efforts and allocate resources effectively.
The Ongoing Nature of Security Standards
Implementing network security standards is not a one-time task. Regular audits, updates, and employee training are key components of maintaining a strong security posture. This continuous process helps organizations build a culture of security that can provide a competitive edge in today’s digital landscape.
As we move forward, let’s explore the key components necessary for successful implementation of these network security standards.
How to Build a Robust Network Security Framework
Conduct Thorough Risk Assessments
The foundation of any effective network security implementation is a thorough risk assessment. This process involves the identification and evaluation of potential threats to your network. Only 30 percent of respondents rate their organization’s IT security posture in terms of its effectiveness at mitigating risks, vulnerabilities and attacks.

To conduct a risk assessment:
- Identify your critical assets and data
- Evaluate potential threats and vulnerabilities
- Assess the potential impact of each risk
- Prioritize risks based on likelihood and impact
Implement Strong Access Controls
Access control is a critical component of network security. Multi-factor authentication (MFA) has proven to be particularly effective. When you implement access controls:
- Use role-based access control (RBAC) to limit user permissions
- Apply the principle of least privilege
- Review and update user access rights regularly
- Consider biometric authentication for highly sensitive areas
Configure Advanced Firewall and IDS Systems
Modern firewalls and intrusion detection systems (IDS) are essential for protection against network intrusions. Next-generation firewalls (NGFW) offer advanced features like application awareness and integrated intrusion prevention. When you configure these systems:
- Update firewall rules and IDS signatures regularly
- Use deep packet inspection to analyze network traffic
- Implement network segmentation to isolate sensitive data
- Consider a web application firewall (WAF) for web-facing applications
Encrypt Data and Communications
Encryption is a powerful tool for protecting data both at rest and in transit. The use of strong encryption algorithms (like AES-256) can make data unreadable to unauthorized parties. When you implement encryption:
- Use HTTPS for all web traffic
- Implement end-to-end encryption for sensitive communications
- Use full-disk encryption for all devices, especially mobile ones
- Rotate encryption keys regularly
Establish Continuous Monitoring Practices
Continuous monitoring is vital for maintaining a strong security posture. It allows organizations to detect and respond to threats in real-time. Try to:
- Implement a Security Information and Event Management (SIEM) system
- Set up alerts for unusual network activity
- Conduct regular vulnerability scans
- Use automated tools to monitor for compliance with security policies
The implementation of these key components will significantly enhance your network security framework. As threats continue to evolve, the next chapter will explore best practices for maintaining and updating your security measures to stay ahead of potential risks.
How to Put Network Security Standards into Action
Create a Comprehensive Security Policy
The first step in implementing network security standards is to develop a robust security policy. This document should outline your organization’s approach to protecting digital assets, data, and infrastructure. A well-crafted policy typically includes:
- Clear definitions of roles and responsibilities
- Guidelines for acceptable use of company resources
- Procedures for handling sensitive information
- Protocols for incident reporting and response
Ponemon Institute, headquartered in Michigan, is considered the pre-eminent research center dedicated to privacy, data protection and information security policy. Your policy should be a living document, reviewed and updated regularly to address new threats and technologies.
Prioritize Employee Training
Even the most sophisticated security measures can fail due to human error. That’s why employee training is essential. A comprehensive training program should cover:
- Basic cybersecurity principles
- How to identify and report potential threats
- Proper handling of sensitive data
- Best practices for password management and multi-factor authentication
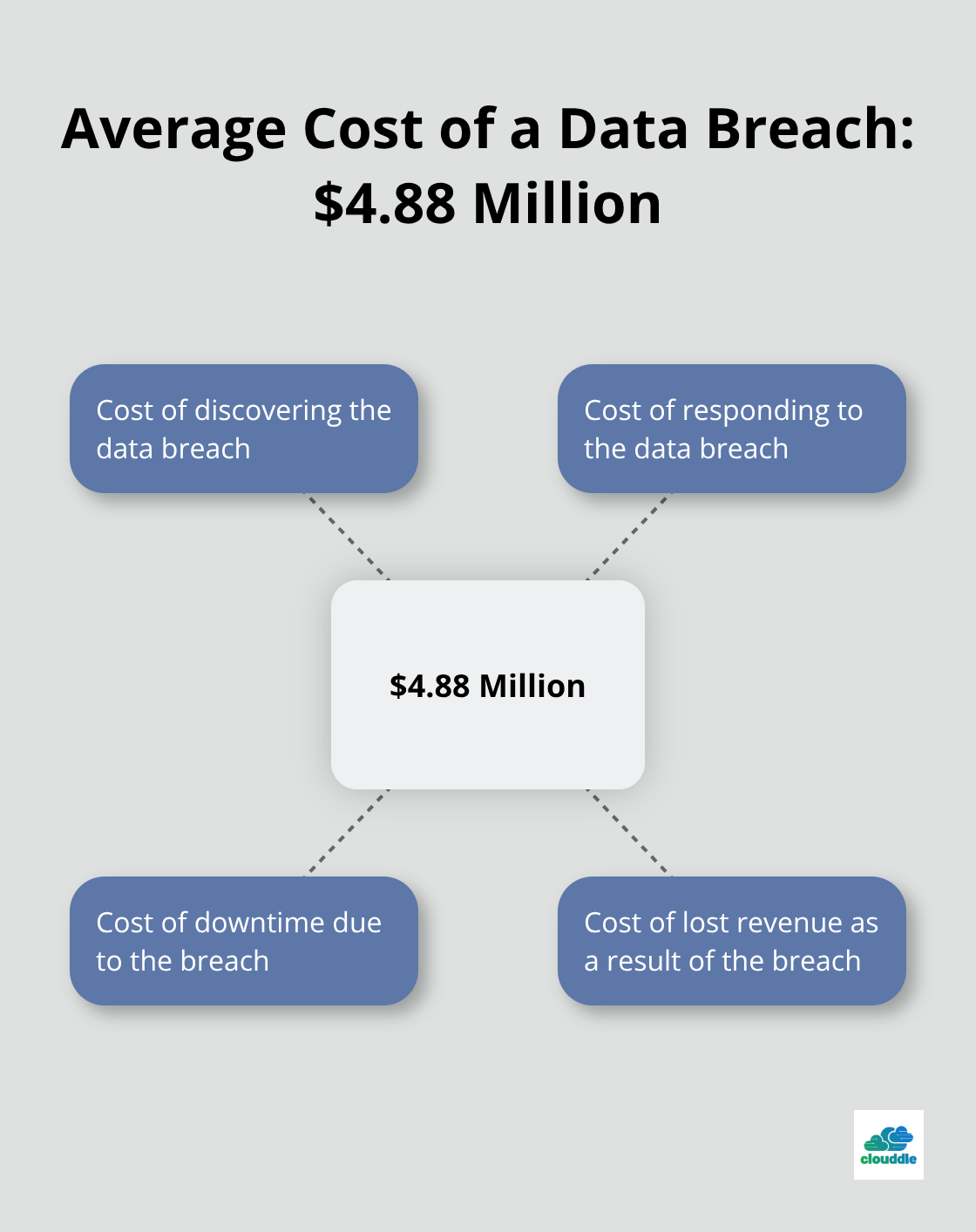
IBM’s research shows that the average cost of a data breach is USD 4.88 million. This price tag includes the costs of discovering and responding to the violation, downtime and lost revenue.
Develop a Robust Incident Response Plan
No security system is impenetrable, so it’s essential to have a plan for when breaches occur. An effective incident response plan should include:
- Clear definitions of what constitutes an incident
- Step-by-step procedures for containment and eradication
- Guidelines for communicating with stakeholders and the public
- Processes for post-incident analysis and improvement
The SANS Institute recommends testing your incident response plan at least twice a year through tabletop exercises or simulated attacks.
Implement Continuous Monitoring
Continuous monitoring is vital for maintaining a strong security posture. It allows organizations to detect and respond to threats in real-time. To implement continuous monitoring:
- Set up a Security Information and Event Management (SIEM) system
- Configure alerts for unusual network activity
- Conduct regular vulnerability scans (at least quarterly)
- Use automated tools to monitor compliance with security policies
Ensure Regulatory Compliance
Many industries have specific regulations governing data protection and privacy (e.g., GDPR, HIPAA). To ensure compliance:
- Identify which regulations apply to your organization
- Map your security controls to regulatory requirements
- Conduct regular audits to verify compliance
- Keep detailed records of your compliance efforts
Implementing these practices will significantly enhance your organization’s security posture and help protect valuable digital assets.
Final Thoughts
Network security standards form the foundation of a robust cybersecurity strategy in today’s digital landscape. Organizations must adopt comprehensive standards like ISO 27001, NIST Cybersecurity Framework, and CIS Controls to reduce risk exposure and protect valuable digital assets. These standards require thorough risk assessments, strong access controls, advanced firewall configurations, and encryption measures to maintain an effective security posture.
Regular security audits, updates, and employee training programs play a vital role in creating a security-conscious culture within organizations. As cyber threats evolve, companies must continuously monitor, improve, and adapt their security policies and practices to stay ahead of potential risks. This ongoing process ensures that organizations can effectively defend against new and emerging threats in an ever-changing technological landscape.
We at Clouddle understand the complexities of implementing and maintaining network security standards. Our managed IT and security services help businesses navigate the cybersecurity landscape while focusing on their core operations. We provide comprehensive solutions that combine networking, security, and support (allowing organizations to build a resilient defense against cyber threats).