Network security is a critical skill in today’s digital landscape. At Clouddle, we understand the importance of mastering this field to protect organizations from ever-evolving cyber threats.
In this guide, we’ll explore effective strategies to learn network security, from foundational concepts to advanced techniques. Whether you’re a beginner or looking to enhance your existing skills, our practical approach will help you navigate the complex world of network defense.
Network Security Essentials
The Foundation of Digital Defense
Network security forms the backbone of modern digital defense strategies. It protects data, systems, and networks from unauthorized access and malicious activities. Let’s explore the key components that make up effective network security.
Understanding the OSI Model and Network Protocols
The Open Systems Interconnection (OSI) model describes seven layers that computer systems use to communicate over a network. This model has unique security considerations at each level. For example, IP spoofing threatens the network layer, while SQL injection attacks target the application layer.
Network protocols like TCP/IP, HTTP, and HTTPS act as the internet’s languages. Knowledge of these protocols helps identify potential vulnerabilities. For instance, unencrypted HTTP traffic can be intercepted easily, which has led to HTTPS becoming the standard for secure web communication.
Identifying Common Network Vulnerabilities
Network vulnerabilities are weaknesses that attackers exploit to gain unauthorized access or disrupt services. Some prevalent vulnerabilities include:
- Outdated software and firmware
- Weak passwords and poor authentication practices
- Misconfigured firewalls and routers
- Unpatched systems susceptible to known exploits
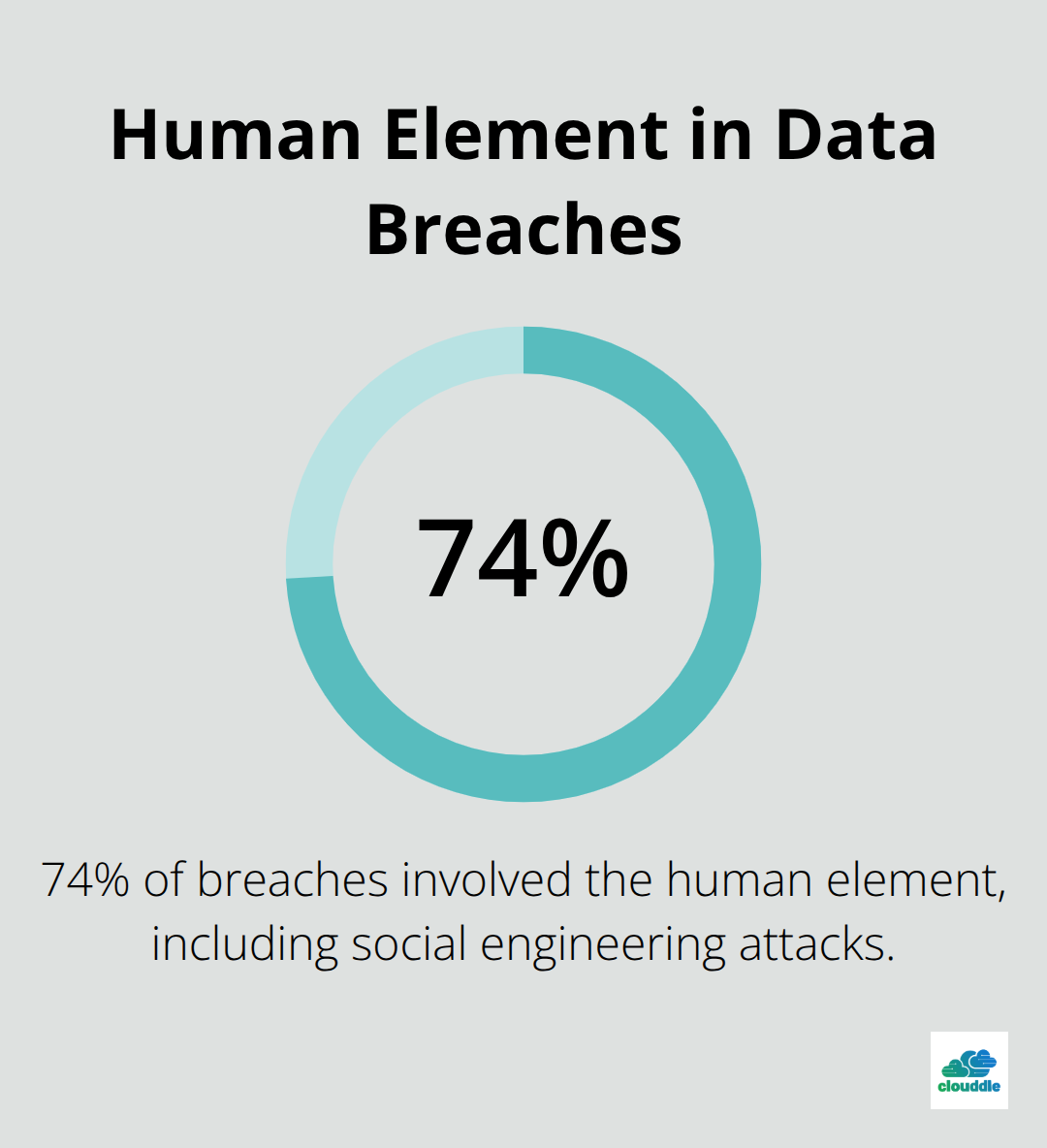
The 2023 Verizon Data Breach Investigations Report revealed that 74% of breaches involved the human element (including social engineering attacks). This statistic highlights the importance of both technical measures and user education in network security.
Implementing Security Best Practices
To strengthen your network against threats, consider these actionable best practices:
- Implement strong access controls: Use multi-factor authentication and the principle of least privilege to limit unauthorized access.
- Update and patch regularly: Keep all systems and software up-to-date to protect against known vulnerabilities.
- Segment your network: Divide your network into smaller, isolated segments to contain potential breaches and limit lateral movement.
- Encrypt sensitive data: Use strong encryption protocols for data in transit and at rest.
- Conduct regular security audits: Perform penetration testing and vulnerability assessments to identify and address weaknesses proactively.
These fundamentals create a solid foundation for more advanced network security concepts. As we move forward, we’ll explore practical learning approaches that will help you apply these principles in real-world scenarios.
Hands-On Learning for Network Security Mastery
Virtual Labs and Simulations
Virtual labs offer a safe environment to practice network security techniques without risking real systems. Platforms like TryHackMe and Hack The Box present a wide range of challenges, from beginner to advanced levels. These platforms simulate real-world scenarios, allowing you to identify vulnerabilities, exploit weaknesses, and implement security measures.
TryHackMe’s “Complete Beginner” path guides users through basic Linux commands, web application security, and network exploitation. As skills improve, users can tackle more complex rooms that mimic enterprise environments.
Capture The Flag (CTF) Competitions
CTF competitions test your skills against other security enthusiasts. These events come in a number of formats, with the most popular being jeopardy, attack-defense, or a mix of the two styles.
PicoCTF, organized by Carnegie Mellon University, serves as an excellent starting point for beginners. It offers year-round access to challenges covering various security topics. For more advanced practitioners, DEF CON CTF stands as one of the most prestigious competitions in the cybersecurity world.
Participation in CTFs sharpens technical skills, improves problem-solving abilities, and teaches you to work under pressure – essential skills for any network security analyst.
Building Your Own Security Lab
Creating a home lab is an invaluable step in your learning journey. It allows you to experiment with different network configurations, security tools, and attack scenarios in a controlled environment.
Try to start with a basic setup using virtualization software like VirtualBox or VMware. Create a small network with different operating systems (Windows, Linux, and maybe a server OS). Then, introduce security tools like Wireshark for packet analysis, Nmap for network scanning, and Metasploit for penetration testing.
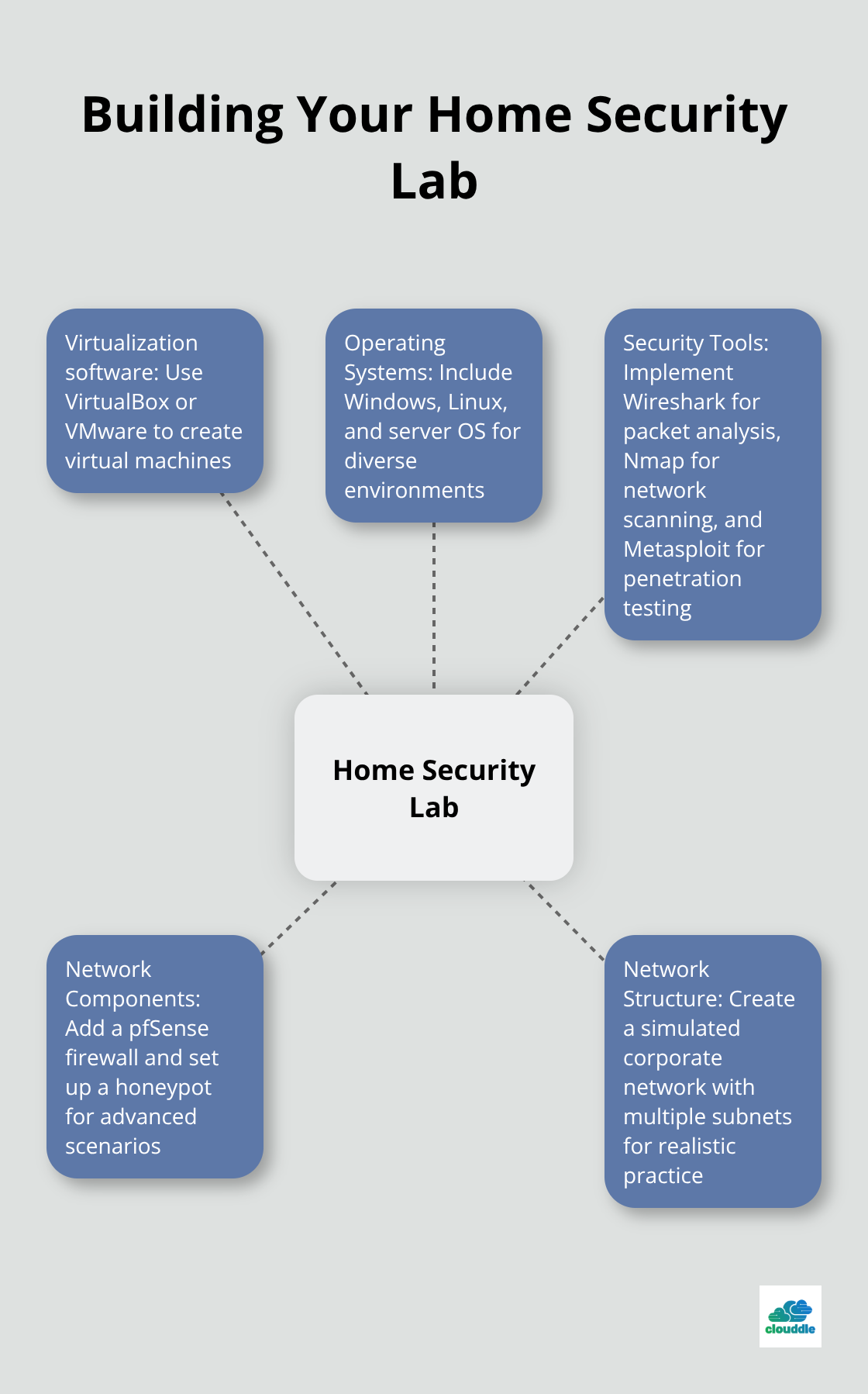
As your comfort level grows, expand your lab to include more complex setups. Add a pfSense firewall, set up a honeypot, or create a simulated corporate network with multiple subnets. This hands-on experience will give you a deeper understanding of how different security measures work together in a real-world environment.
The goal is to break things and learn from the process. Mistakes in your lab become valuable learning opportunities rather than security incidents.
These practical approaches will help you gain a robust, hands-on understanding of network security. This experience will complement your theoretical knowledge and prepare you for the challenges you’ll face in real-world scenarios. As we move forward, we’ll explore advanced network security concepts that build upon these foundational skills and practices.
Mastering Advanced Network Security Techniques
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS and IPS form critical components of a robust network security strategy. IDS monitors network traffic for suspicious activity and alerts administrators, while IPS automatically blocks potential threats.
Key considerations for IDS/IPS implementation include:
- Placement: Deploy sensors at critical network points (e.g., network perimeter, between security zones).
- Tuning: Adjust rules regularly to minimize false positives and negatives.
- Integration: Connect IDS/IPS with other security tools like SIEM systems for comprehensive security monitoring.
Studies by Ponemon Institute demonstrate a 50% reduction in mean time to respond (MTTR) using automation and orchestration tools.
Encryption and Virtual Private Networks (VPNs)
Encryption protects data both in transit and at rest. VPNs use encryption to create secure tunnels for data transmission across public networks.
For effective encryption and VPN implementation:
- Use strong protocols: Choose modern encryption standards (e.g., AES-256) and VPN protocols (such as OpenVPN or WireGuard).
- Manage keys effectively: Implement a robust key management system.
- Conduct regular audits: Perform periodic reviews of encryption practices to identify vulnerabilities.
Network Segmentation and Access Control
Network segmentation divides a network into smaller, isolated segments to contain potential breaches and limit lateral movement. Access control ensures users have only the necessary permissions for their roles.
Effective implementation includes:
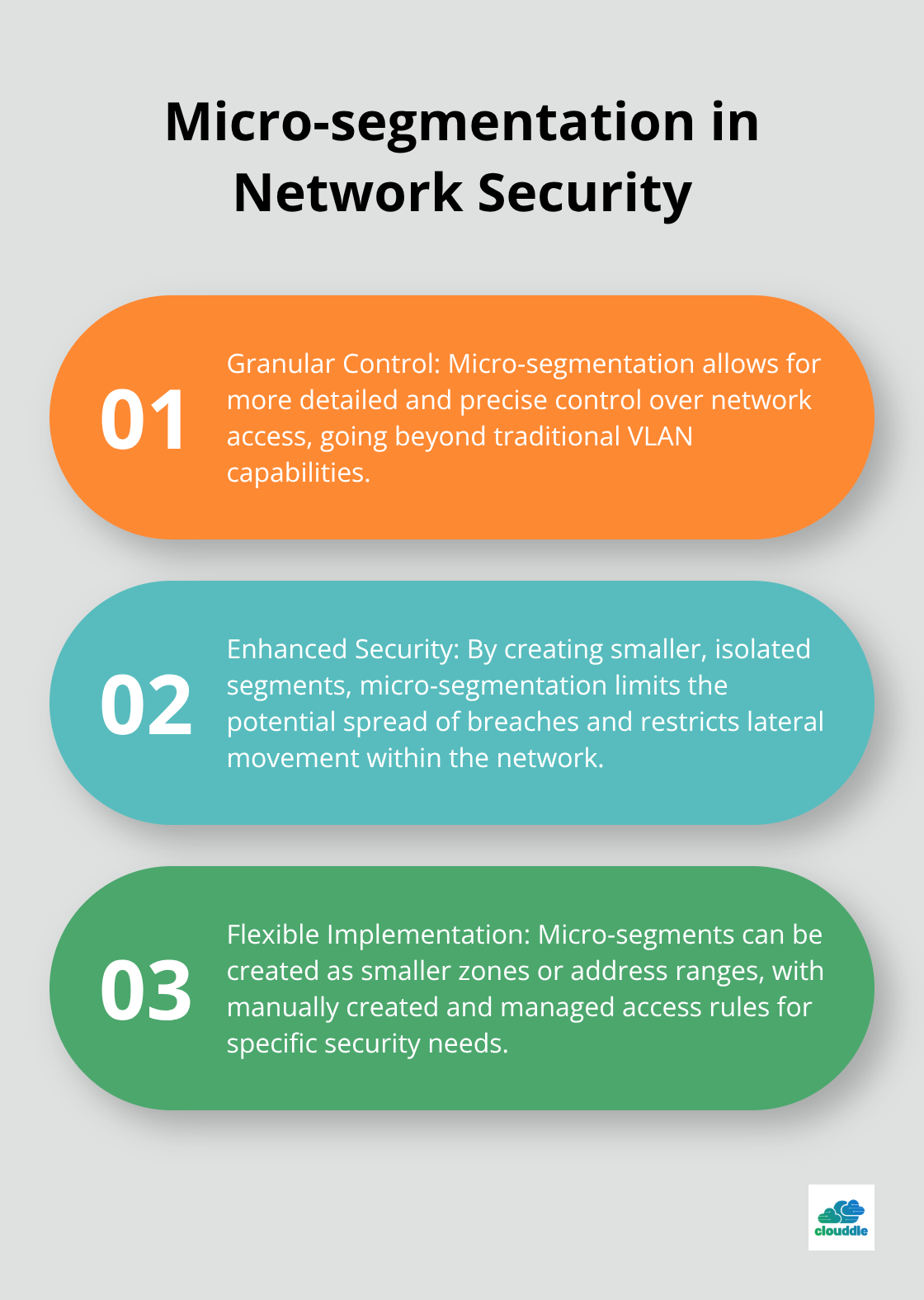
- Micro-segmentation: Implement software-defined micro-segmentation for granular control beyond traditional VLANs.
- Zero Trust model: Adopt a “never trust, always verify” approach, requiring authentication and authorization for every access attempt.
- Regular access reviews: Conduct periodic reviews of user access rights to align with current roles and responsibilities.
Microsegments are simply smaller zones or address ranges possessing more granular, manually created and managed access rules.
Continuous Monitoring and Threat Intelligence
Implement continuous monitoring to detect and respond to security incidents in real-time. Leverage threat intelligence feeds to stay informed about emerging threats and vulnerabilities.
Try to:
- Establish a Security Operations Center (SOC): Create a dedicated team for 24/7 monitoring and incident response.
- Utilize machine learning: Implement AI-powered tools to analyze large volumes of security data and identify anomalies.
- Share threat intelligence: Participate in industry-specific information sharing groups to enhance collective defense capabilities.
Final Thoughts
Learning network security requires a multifaceted approach. Start with a solid foundation in networking principles, then practice through virtual labs and CTF competitions. Advanced concepts like intrusion detection systems and encryption will enhance your skills further. The field evolves rapidly, so continuous learning is essential to stay effective in protecting digital assets.
Online platforms offer specialized courses and certifications to further develop your skills. Industry conferences provide opportunities to learn from experts and network with peers. Professional communities can offer valuable insights and support as you progress in your network security journey.
At Clouddle, we understand the importance of robust network security in today’s digital landscape. Our Network as a Service (NaaS) solutions combine networking, entertainment, and security features to help businesses operate securely. We handle the complexities of network security so organizations can focus on growth and success.


