Cyberattacks cost businesses an average of $4.45 million per incident, according to IBM’s 2024 data breach report. Your company’s IT security management isn’t just about preventing attacks-it’s about protecting your revenue, reputation, and customer trust.
We at Clouddle have seen firsthand how businesses struggle to balance security with operations. The good news is that with the right strategies and tools, you can build a defense system that actually works.
What Threats Are Targeting Your Business Right Now
Ransomware attacks hit 2,777 organizations in the U.S. during 2023 according to CISA data, and the average ransom payment climbed to $812,360 that year. These aren’t theoretical risks anymore-they’re happening to real companies in your industry right now.

Ransomware operators have shifted tactics from simply encrypting files to stealing data first, then threatening to publish it unless you pay. This double-extortion approach means even with backups, you face reputational damage and operational downtime. The median time to recover from a ransomware attack stretches to 21 days, which directly impacts revenue for most businesses.
How Phishing Opens the Door
Phishing attempts have increased significantly, and your employees are the first line of defense whether they know it or not. Microsoft reports that phishing remains the entry point for most ransomware attacks. Social engineering attacks don’t require sophisticated hacking skills; attackers simply manipulate people into revealing credentials or access. A single compromised employee account opens your entire network to attackers who move laterally through your systems before anyone notices something’s wrong.
Where Attackers Actually Get In
Your data breaches typically don’t start with a zero-day exploit-they start with weak passwords and missing multi-factor authentication. Verizon’s 2024 data breach report shows that credential theft remains the top attack vector, accounting for a significant portion of breaches. Unauthorized access happens because access controls are loose, not because your firewall is weak. Attackers don’t need to break down the front door if someone left it unlocked. Many organizations still grant employees access to systems they don’t actually need for their jobs, creating unnecessary risk.
The Cost of Slow Detection
The cost of a data breach reaches $4.95 million on average, but this varies dramatically based on how quickly you detect and respond. Organizations that detected breaches in less than 30 days saved an average of $1 million compared to those taking over 200 days. Detection speed matters more than perfection-you need visibility into what’s happening on your network right now, not a perfect security system that nobody monitors. This visibility gap is where most organizations fail, and it’s exactly why the next section covers the practices that actually stop these threats before they cause damage.
Best Practices for IT Security Management
Multi-Factor Authentication Stops Most Attacks
Security controls fail when organizations implement them halfway. You install multi-factor authentication, then let employees bypass it for convenience. You conduct a security audit, file the report, and ignore the findings for another year. You run one phishing simulation, declare victory, and move on. This approach wastes money and leaves you exposed. Real security management means treating these practices as ongoing operations, not one-time projects.
Start with multi-factor authentication on every system that matters. Microsoft reports that more than 99.9% of compromised accounts lack MFA enabled, which tells you exactly how much protection this single layer provides. Enforce it on email, remote access, administrative accounts, and any system holding sensitive data. Your employees will complain about the extra step for about two weeks, then adapt. The friction is intentional and necessary.
Vulnerability Assessments Require Quarterly Cadence
Conduct vulnerability assessments quarterly, not annually. Verizon’s research shows that attackers exploit known vulnerabilities within days of disclosure, so waiting twelve months between assessments means you sit on exploitable gaps for months at a time. Use automated scanning tools to identify missing patches, weak configurations, and credential exposure, then create a remediation timeline with actual deadlines and ownership. Assign someone specific to each vulnerability and track closure rates as a metric. When your team knows someone is watching, closure rates improve dramatically.
Employee Training Works When You Track Results
Employee training should happen continuously, not as an annual compliance checkbox. Phishing simulations work best when you run them monthly and track which employees fail repeatedly, then provide targeted coaching. The employees who click malicious links in your simulations are your actual risk, and they need different training than those who never fall for it. Track metrics that matter: what percentage of employees report suspicious emails, how many fail simulations, and whether failure rates improve over time.
Incident Response Plans Need Practice
Create an incident response plan that your team actually practices. CISA data shows that organizations with formal incident response plans reduce breach damage significantly, but only if they’ve tested the plan. Conduct tabletop exercises twice a year where your team walks through a ransomware scenario or data breach scenario and identifies gaps in communication, tools, and procedures. Document who calls whom, what systems you shut down first, and how you communicate with leadership. When an actual incident happens, you’ll follow the plan you’ve already practiced instead of making decisions under panic. These foundational practices form your defense, but they only work if someone monitors your systems continuously and responds when threats appear.
Why Outsourcing Security Management Makes Business Sense
The True Cost of Building Internal Security Teams
Building an internal security team sounds straightforward until you calculate what it actually costs. A mid-level security analyst earns between $75,000 and $95,000 annually, a senior security engineer runs $120,000 to $150,000, and a CISO commanding strategic oversight costs $150,000 to $250,000 or more. Add benefits, training, tools, and infrastructure, and a three-person security team easily exceeds $400,000 per year before you purchase a single monitoring platform or vulnerability scanner. Most organizations don’t have three dedicated security people anyway. Instead, security responsibilities land on overworked IT generalists who juggle server maintenance, user support, and network administration while trying to monitor for threats they lack time to understand. This fractured approach explains why detection times stretch so long and why breaches cause such extensive damage.
How Managed Providers Detect Threats Faster
Outsourcing security operations to a managed provider shifts this burden to specialists who focus exclusively on threat detection and response. These providers maintain 24/7 monitoring across your entire environment, catching intrusions during nights and weekends when your internal team sleeps. They operate Security Information and Event Management systems that correlate events across thousands of organizations, giving them threat intelligence your solo analyst simply cannot match. A managed security provider sees attack patterns industry-wide and knows which vulnerabilities attackers actively exploit this week, not last month. This real-time visibility translates directly into faster detection. Organizations using managed detection and response services detect breaches in an average of 172 days when identified by internal security teams, compared to the longer detection cycles for organizations relying solely on internal capabilities.
The Financial Case for Outsourced Security
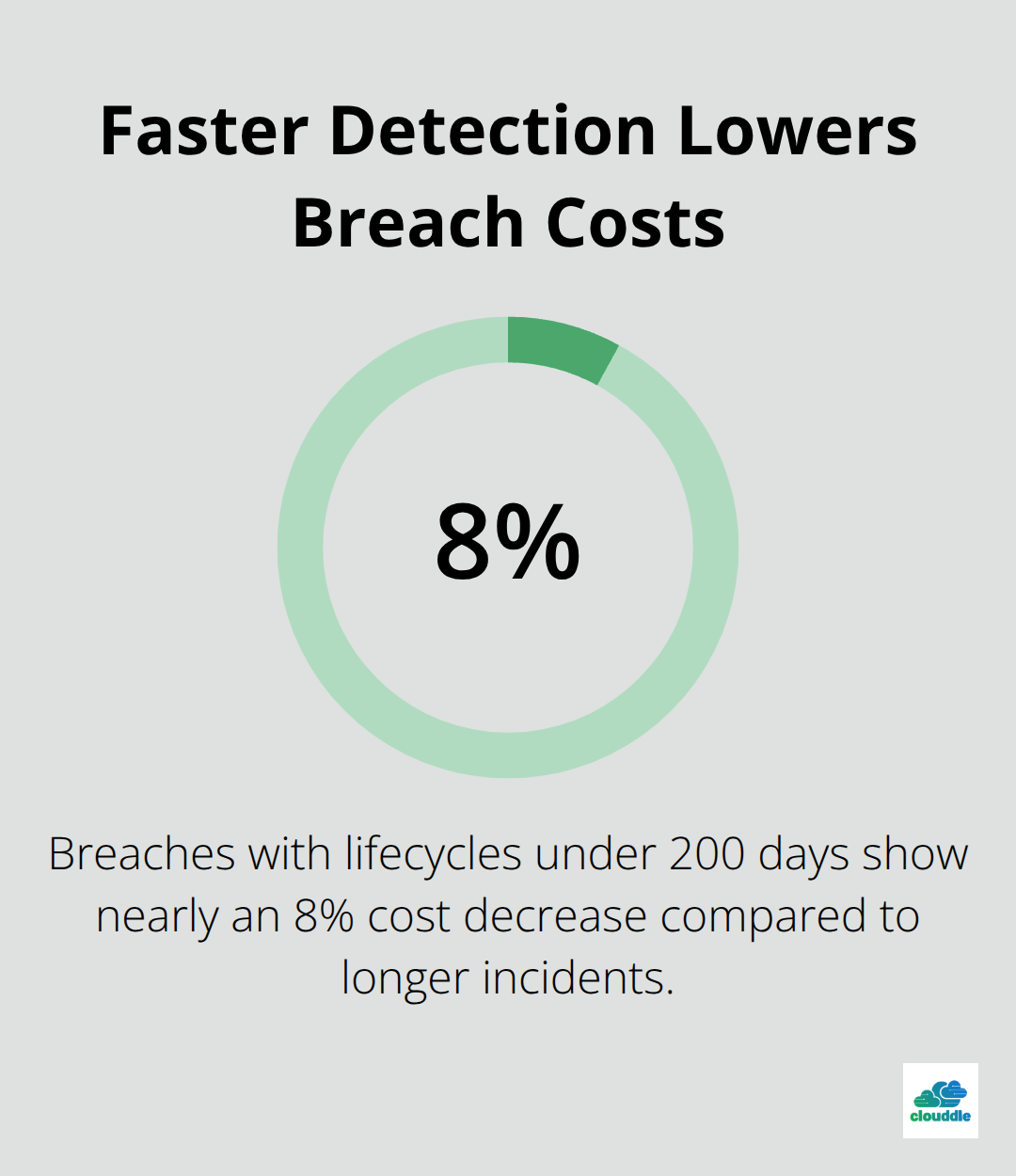
The financial comparison becomes clear when you factor in actual outcomes. Breaches with lifecycles under 200 days show nearly an 8% decrease in costs compared to those extending beyond 200 days, which reach USD 5.01 million on average. Managed security services typically cost between $3,000 and $15,000 monthly depending on your environment size and complexity, which means annual costs between $36,000 and $180,000. Even at the high end, this undercuts a single full-time security hire while delivering superior detection capabilities and eliminating the recruitment and retention headaches that plague security staffing.
What Managed Providers Actually Handle
Managed providers also handle the tedious but critical work that internal teams constantly defer: running monthly phishing simulations, conducting quarterly vulnerability assessments, managing patch deployments, and updating incident response playbooks. These activities prevent breaches, but they create no visible business value until something bad happens, so they perpetually lose budget battles against revenue-generating projects. A managed provider treats these activities as standard operations rather than optional extras. Your team can focus on business priorities while security specialists handle the continuous monitoring that catches threats before they spread.

Final Thoughts
IT security management isn’t a project you complete and forget-it’s an operational discipline that requires continuous attention and adjustment. The practices covered in this post form the foundation of a security program that actually protects your business, but foundation alone won’t stop threats from spreading across your network. You need someone monitoring your systems when attacks happen, detecting intrusions before they cause damage, and responding with the speed that prevents catastrophic losses.
A single breach costs your business millions in direct expenses, downtime, and reputation damage, yet the organizations that minimize this impact aren’t the ones with perfect security systems sitting unmonitored. They’re the ones with continuous visibility into what happens on their networks and the expertise to respond immediately when something goes wrong. This is where managed security services deliver measurable value that internal teams struggle to match, and it’s where managed IT and security services can transform your security posture.
We at Clouddle understand that IT security management consumes resources and expertise most organizations lack internally. We combine 24/7 monitoring, threat detection, and incident response with the networking and infrastructure support your business needs to operate safely. The question isn’t whether you can afford to invest in security-it’s whether you can afford not to.


