Network security is a top priority for businesses in today’s digital landscape. At Clouddle, we understand the critical importance of protecting your digital assets from ever-evolving threats.
Modeling network security is a powerful approach to identify vulnerabilities and create robust defense strategies. In this post, we’ll explore how to effectively model network security for optimal protection, providing you with practical tools and techniques to safeguard your organization’s valuable data and systems.
What Is Network Security Modeling?
Definition and Significance
Network security is important because it keeps sensitive data safe from cyber attacks and ensures the network is usable and trustworthy. It creates a comprehensive representation of an organization’s network infrastructure, including components, connections, and potential vulnerabilities. This model acts as a blueprint for implementing effective security measures and predicting possible threats.
In today’s digital landscape, cyber threats continue to evolve in sophistication. Cybersecurity Ventures expects global cybercrime costs to grow by 15 percent per year over the next five years, reaching $10.5 trillion USD annually by 2025. This staggering figure underscores the critical need for robust network security measures.

Network security modeling allows organizations to take a proactive stance against these threats. It simulates various attack scenarios, helping businesses identify weak points in their infrastructure before malicious actors exploit them. This approach significantly reduces the risk of data breaches, financial losses, and reputational damage.
Essential Components
An effective network security model comprises several key elements:
- Network Topology: A detailed map of all devices, connections, and data flows within the organization’s network.
- Asset Inventory: A comprehensive list of all hardware and software assets (including their configurations and vulnerabilities).
- Threat Landscape: An analysis of potential internal and external threats specific to the organization’s industry and infrastructure.
- Security Controls: A catalog of existing security measures and their effectiveness in mitigating identified risks.
- Risk Assessment: A systematic evaluation of potential vulnerabilities and their impact on the organization’s operations.
Benefits of a Robust Security Model
A robust security model offers numerous advantages. It provides a clear picture of the organization’s security posture, enabling informed decision-making about resource allocation and security investments.
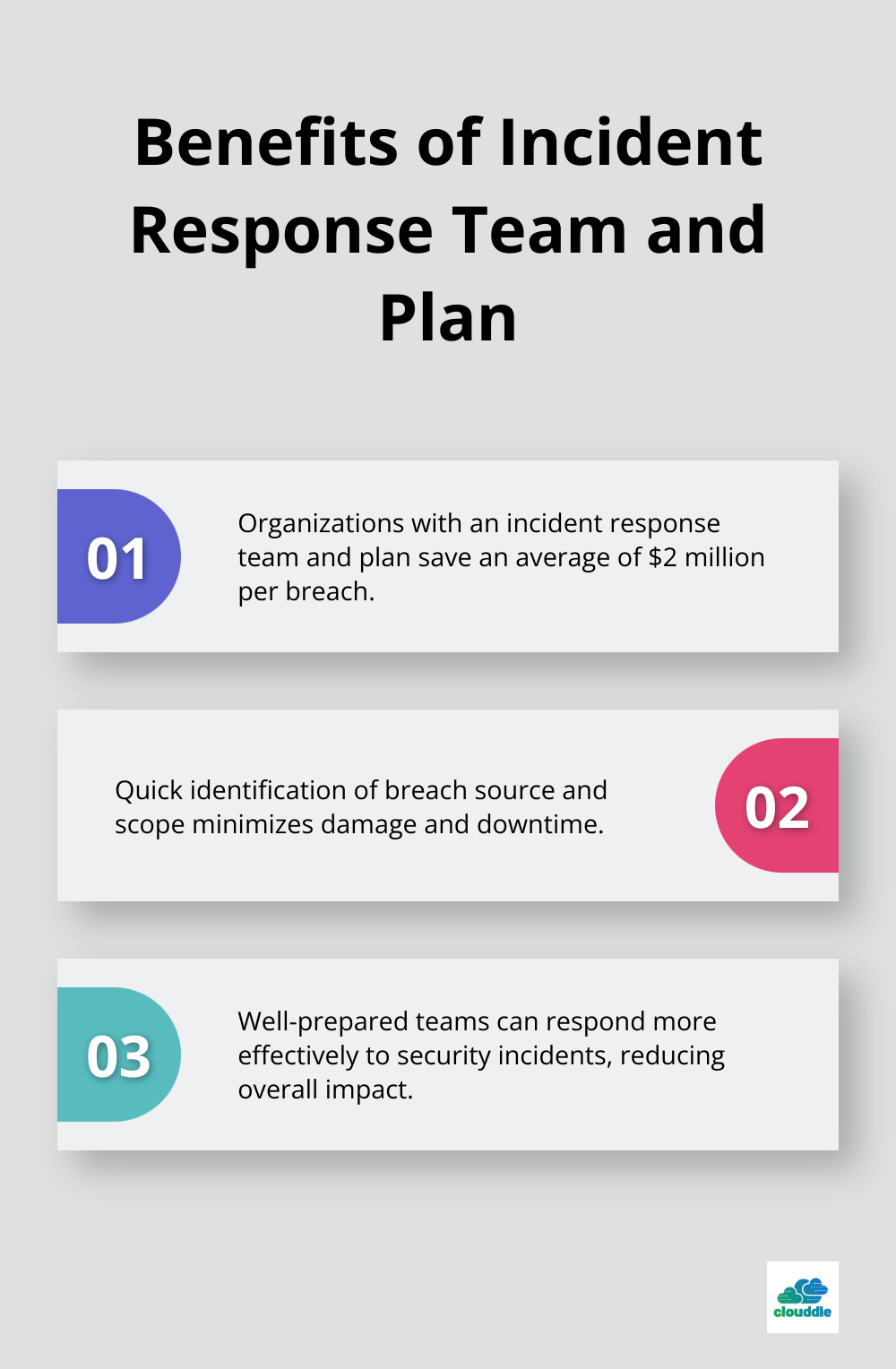
It also enhances incident response capabilities. With a well-defined model, security teams can quickly identify the source and scope of a breach, minimizing damage and downtime. IBM’s Cost of a Data Breach Report 2021 revealed that organizations with an incident response team and plan in place saved an average of $2 million per breach compared to those without.
Moreover, a robust security model facilitates compliance with industry regulations. Many standards (such as GDPR and HIPAA) require organizations to demonstrate due diligence in protecting sensitive data. A comprehensive security model provides evidence of this diligence, simplifying audits and reducing the risk of non-compliance penalties.
Technological Advancements in Modeling
Advanced technologies revolutionize network security modeling. Artificial Intelligence (AI) and Machine Learning (ML) algorithms analyze vast amounts of network data in real-time, detecting anomalies and predicting potential threats with unprecedented accuracy.
For example, Darktrace, a leading AI cybersecurity company, reported that their AI-powered system detected and neutralized a sophisticated cyber-attack on a major European bank in just two seconds, preventing any data loss or operational disruption.
As we move forward, it’s important to understand the best practices for implementing network security monitoring effectively. The next section will explore these practices in detail, providing you with actionable insights to enhance your organization’s security posture.
How to Implement Network Security Modeling
Network security modeling requires constant attention and refinement. Here’s how you can implement it for optimal protection:
Create a Comprehensive Asset Inventory
The foundation of any effective security model is a thorough understanding of what you’re protecting. Create a detailed inventory of all your network assets, including hardware, software, data, and human resources. This inventory should list devices, their configurations, operating systems, and installed applications.
A study by Ponemon Institute found that organizations with an accurate IT asset inventory can reduce the cost of data breaches by an average of $250,000. This saving underscores the importance of knowing exactly what’s on your network.
Perform Regular Threat Assessments
After you have a clear picture of your assets, identify potential threats. Analyze both internal and external risks specific to your organization and industry. Use threat intelligence feeds and industry reports to stay informed about emerging threats.
The SANS Institute recommends threat assessments at least quarterly (or more frequently for high-risk industries). These assessments should consider various attack vectors, including malware, phishing, insider threats, and advanced persistent threats (APTs).
Deploy Defense in Depth
No single security measure is foolproof, which is why a layered approach to security is essential. This strategy, known as defense in depth, involves deploying multiple security controls throughout your network. Each layer acts as a safety net for the others, increasing the difficulty for attackers to breach your defenses.
A typical defense in depth strategy might include:
- Perimeter defenses (firewalls, intrusion detection systems)
- Network segmentation
- Access controls and authentication mechanisms
- Endpoint protection
- Data encryption
- Regular security awareness training for employees
Use AI and Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) are transforming network security modeling. These technologies can analyze vast amounts of data in real-time, detect anomalies, and predict potential threats with unprecedented accuracy.
AI improves application security by analyzing code, user interactions, and runtime behavior to detect vulnerabilities and threats. Machine learning algorithms can identify patterns and anomalies in network traffic, enhancing threat detection capabilities.
Monitor and Update Continuously
Your network security model should evolve constantly to reflect changes in your network infrastructure and the threat landscape. Implement continuous monitoring tools to track network activity and detect potential security incidents in real-time.
The Ponemon Institute found that organizations with security automation tools save an average of .58 million per breach compared to those without such tools. This statistic highlights the importance of leveraging technology for ongoing security monitoring and management.
Update your security controls regularly based on the insights gained from monitoring. This might involve patching vulnerabilities, adjusting firewall rules, or implementing new security technologies as they become available.
As we move forward, it’s important to consider the tools and techniques that can enhance your network security modeling efforts. The next section will explore these in detail, providing you with practical solutions to strengthen your organization’s security posture.
Essential Tools for Network Security Modeling
Network Mapping and Visualization
Network mapping tools create visual representations of network infrastructure. These tools identify connected devices, their relationships, and potential vulnerabilities. Nmap, an open-source tool, scans large networks and creates detailed maps of their structure.
Vulnerability Assessment and Management
Vulnerability assessment tools identify weaknesses in networks before attackers exploit them. These tools scan networks for known vulnerabilities and provide detailed reports on potential risks.
According to a newly released report from Swimlane, a concerning 68% of organizations say remediating a critical vulnerability takes more than 24 hours. This statistic highlights the importance of regular vulnerability assessments in maintaining a robust security posture.

Penetration Testing and Ethical Hacking
Penetration testing (ethical hacking) simulates real-world attacks on networks to identify vulnerabilities that automated tools might miss.
Metasploit provides a framework for conducting penetration tests. It allows security professionals to simulate various attack scenarios and assess the effectiveness of existing security measures.
Security Information and Event Management (SIEM)
SIEM systems collect and analyze log data from various sources across networks. They provide real-time monitoring and alerting capabilities. These tools are essential for quick detection and response to security incidents.
Integration and Management
The true potential of these tools is realized when they’re integrated into a comprehensive security strategy. Effective implementation and management of these tools ensure organizations get the most out of their security investments.
The effectiveness of these tools depends on regular updates, proper configuration, and skilled personnel. These factors are key to maximizing the benefits of security modeling tools.
Final Thoughts
Network security modeling protects digital assets against evolving cyber threats. Organizations identify vulnerabilities, simulate attacks, and implement defense strategies through comprehensive infrastructure representation. Key strategies include asset inventory creation, threat assessments, defense-in-depth implementation, AI utilization, and continuous monitoring.
Essential tools enhance an organization’s ability to model network security effectively. Network mapping software, vulnerability assessment systems, penetration testing frameworks, and SIEM solutions (Security Information and Event Management) significantly improve security posture. These tools provide valuable insights and automate critical security processes.
Clouddle offers comprehensive solutions to help businesses navigate modern network security challenges. Our Network as a Service combines networking, entertainment, and security services, providing a secure operational environment. Consistent refinement and updates to your security model will ensure long-term protection of your digital assets.


