Companies running workloads across multiple cloud providers face a harder security challenge than those using a single platform. The complexity of managing multi-cloud network security across AWS, Azure, Google Cloud, and others creates blind spots that attackers exploit.
At Clouddle, we’ve seen firsthand how configuration errors and inconsistent policies across clouds lead to breaches. This guide walks you through the risks, best practices, and tools needed to protect your multi-cloud infrastructure.
What Makes Multi-Cloud Environments Such a Breach Magnets
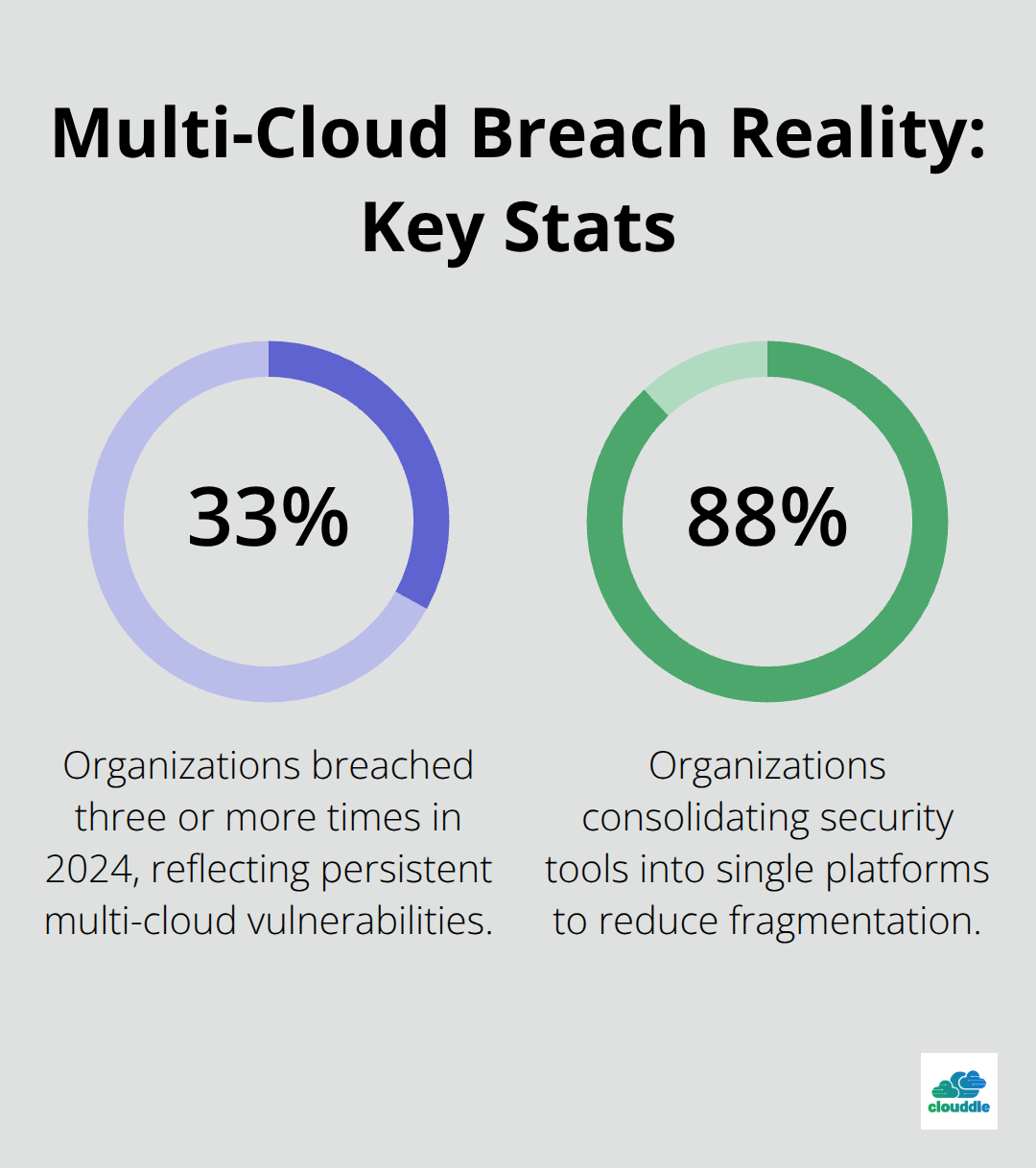
Every additional cloud provider your organization uses multiplies your security complexity exponentially. When workloads spread across AWS, Azure, and Google Cloud, attackers don’t need to breach one fortress-they hunt for the weakest gate. Forrester reports the average cost of a data breach reached about $2.7 million in 2024, with 33% of organizations breached three or more times in a year. The global cost of cybercrime will exceed $23 trillion by 2027 according to Anne Neuberger, U.S. deputy national security advisor for cyber and emerging technologies. These numbers reflect a harsh reality: most organizations lack visibility across their cloud environments.
Configuration Errors Create Silent Vulnerabilities
Configuration drift happens silently across your infrastructure. A developer provisions an S3 bucket with public access in AWS while your Azure security team enforces strict controls. A forgotten API key sits exposed in a GitHub repository. These aren’t theoretical problems-they’re the daily reality in multi-cloud deployments. Each cloud provider uses different default settings and security frameworks, making consistency nearly impossible without automated enforcement. Teams struggle to maintain uniform policies when AWS security groups, Azure network security groups, and Google Cloud firewall rules operate independently. One misconfiguration in any cloud can expose your entire infrastructure to attackers.
Fragmented Monitoring Creates Blind Spots
Most organizations running multi-cloud infrastructure operate with fragmented monitoring tools. Your AWS CloudTrail logs live separately from Azure Activity Logs, which never communicate with Google Cloud’s audit logs. This separation creates blind spots where breaches hide for months. A misconfigured security group in AWS might grant database access to the entire internet, but your central security team never sees it because they’re watching Azure dashboards. The 9 out of 10 organizations reporting challenges related to tools and APIs for consistent security shows this fragmentation problem pervades the industry.
Lateral Movement Becomes Invisible
Without unified visibility, lateral movement detection across cloud providers becomes invisible across your clouds. An attacker compromises one cloud account and pivots silently to another provider’s environment. Network traffic analysis across clouds rarely happens because teams lack tools that aggregate this data. Your security operations team cannot detect when an attacker moves from AWS to Azure because each platform generates separate logs in separate locations. This visibility gap (combined with inconsistent access controls) transforms multi-cloud environments into highways for attackers rather than fortified networks. Organizations need to move beyond provider-specific dashboards to a centralized monitoring layer that normalizes logs and alerts across all clouds simultaneously. This unified approach reveals threats that fragmented systems miss entirely.
How to Build Unified Security Across Your Cloud Providers
The fragmentation problem we covered earlier demands a structural fix, not a band-aid approach. Organizations cannot patch their way to security when each cloud operates as an isolated kingdom with its own rules, tools, and audit trails. The answer lies in enforcing unified security architecture from the ground up, which means standardizing policies, implementing segmentation that works across providers, and creating monitoring that actually connects the dots between clouds. F5 research shows 88% of organizations are consolidating from multiple point solutions into single platforms, a clear signal that teams recognize fragmented security creates more problems than it solves. This shift reflects a hard truth: consistency across clouds isn’t optional anymore.
Standardize Access Controls Before Everything Else
Identity and access management remains the foundation that most organizations get wrong in multi-cloud setups. AWS uses Identity and Access Management, Azure relies on Azure AD, and Google Cloud implements its own IAM system, yet teams often treat these as separate worlds rather than components of one security model. Start by mapping every user, service account, and application across all three clouds to identify privilege creep. Industry standards for cloud security demand that least-privilege access govern every role, with regular automated reviews catching entitlements that expanded beyond their original scope. Implement single sign-on across all cloud providers so credentials stay consistent and revocation happens in one place rather than three. Multi-factor authentication must apply universally, not selectively. A developer with MFA in Azure but not AWS creates a security gap that attackers will find.
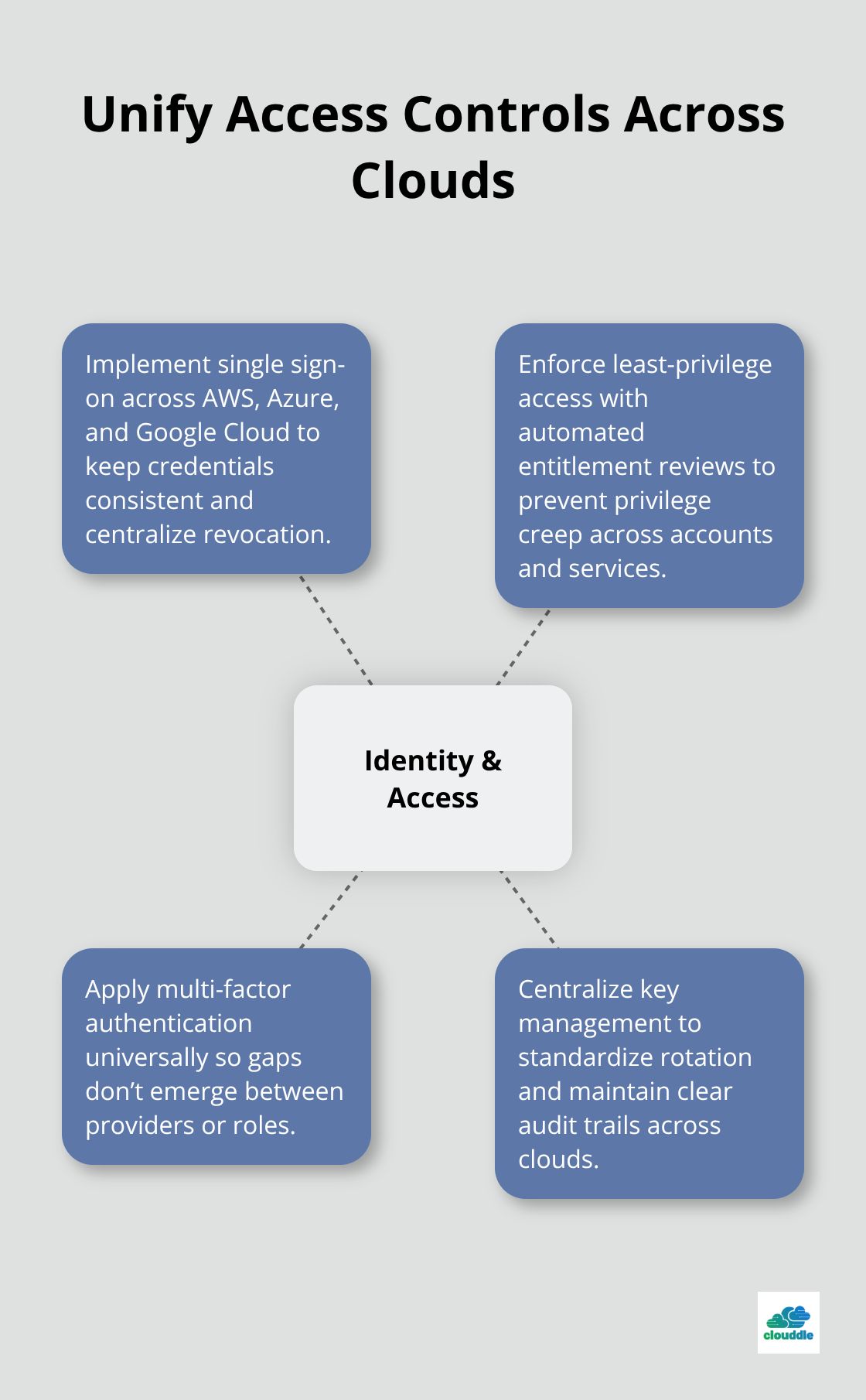
Set up centralized key management so encryption keys never live scattered across provider-specific vaults. When one team manages all keys from a single interface, key rotation happens predictably and audit trails remain intact.
Enforce Network Segmentation That Transcends Cloud Boundaries
Network segmentation within a single cloud is manageable; segmentation across AWS, Azure, and Google Cloud requires deliberate architecture. Zero-trust principles apply here with brutal effectiveness: never trust traffic between clouds automatically, even if it originates from your own infrastructure. Configure virtual private clouds across all providers with consistent CIDR blocks and naming conventions so engineers understand the topology without mental translation. Use virtual firewalls and software-defined networking instead of relying on provider-specific security groups, which don’t communicate across platforms. Micro-segmentation limits lateral movement when an attacker compromises one workload, preventing them from pivoting freely to other environments. Test this segmentation regularly through breach simulations where an attacker gains access to one cloud account and attempts to reach resources in another. Most organizations discover their segmentation fails only after an incident, which defeats the purpose entirely.
Centralize Logging and Alerting Into One Operational View
Separate logs from AWS CloudTrail, Azure Activity Logs, and Google Cloud Audit Logs must flow into a single aggregation point where security teams correlate events across providers. This centralization is non-negotiable for detecting attacks that span multiple clouds. Configure each cloud provider to forward logs to a unified security information and event management system or cloud-native alternative that normalizes the data into a common format. Set alert thresholds that trigger on suspicious patterns across providers rather than within individual clouds. An attacker moving from AWS to Azure generates specific behavioral signals that only become visible when you correlate logs from both platforms. Automate the investigation process so security teams spend less time collecting logs from three different dashboards and more time responding to actual threats. Organizations that maintain unified monitoring detect breaches faster than those stuck with fragmented approaches.
Automate Policy Enforcement Across All Environments
Manual policy enforcement across three cloud providers guarantees inconsistency and human error. Automation transforms security from a reactive scramble into a proactive system that catches violations before they become breaches. Use infrastructure-as-code tools to define security policies once and apply them uniformly across AWS, Azure, and Google Cloud. Automated configuration scanning identifies misconfigurations and drift the moment they occur, not weeks later during an audit. Patch management automation ensures all cloud environments receive security updates on the same schedule, eliminating the weak spots that attackers exploit. Policy-as-code frameworks allow teams to version control security rules just like application code, creating audit trails that satisfy compliance requirements. When automation handles routine enforcement tasks, your security team focuses on threat response and strategic improvements rather than manual compliance checks.
The unified approach we’ve outlined here creates the operational foundation for multi-cloud security, but it only works when you pair it with the right tools and solutions that actually connect these pieces together.
The Right Tools Make Multi-Cloud Security Operational
Organizations cannot standardize policies, centralize monitoring, or automate enforcement without platforms specifically built for multi-cloud environments. The unified approach we outlined requires actual tools that connect your clouds together, not theoretical frameworks sitting in a document. F5 research shows 88% of organizations adopt consolidated security platforms instead of multiple point solutions, a clear signal that teams recognize fragmented tools create more problems than they solve. Your first critical decision involves choosing between building your own integration layer (which consumes months of engineering effort and fails to keep pace with cloud updates) or selecting a platform that handles cross-cloud connectivity natively.
Cloud Access Security Brokers and API Gateways Enforce Consistency
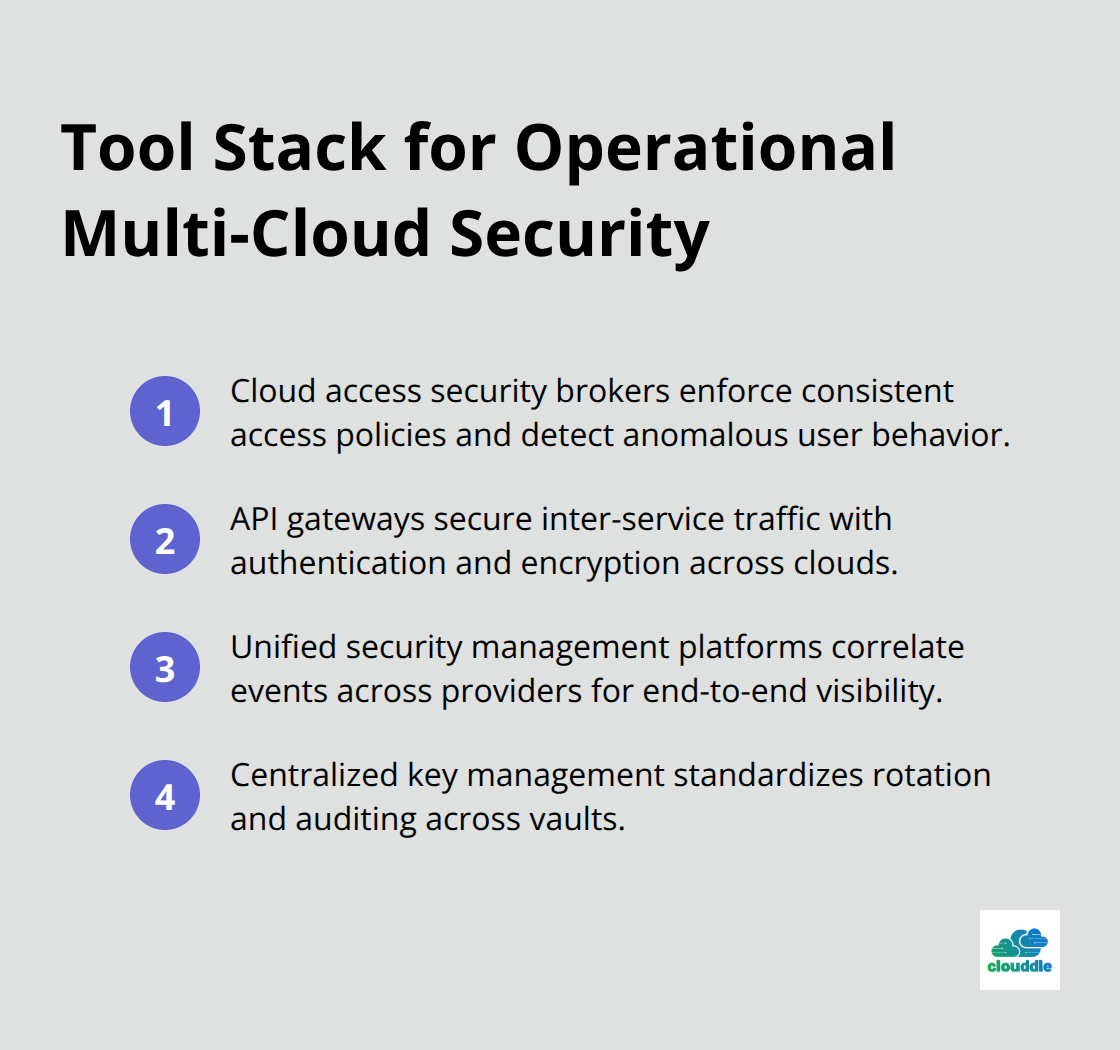
Cloud access security brokers sit at the network edge and inspect traffic flowing between your users and cloud applications, catching anomalous behavior that signals compromised credentials or insider threats. These brokers normalize policies across AWS, Azure, and Google Cloud so that a user blocked from accessing sensitive data in one cloud faces the same restrictions everywhere. API gateways serve a parallel function for service-to-service communication, enforcing authentication and encryption on every request moving between your clouds. Without API gateways, attackers exploit unencrypted inter-cloud traffic or forge credentials to access services across your infrastructure.
Unified Security Management Platforms Aggregate Your Visibility
Unified security management platforms aggregate data from all three cloud providers into single dashboards where your team actually sees what’s happening. These platforms scan configurations automatically, identifying misconfigurations and excessive permissions within hours rather than waiting for audits months later. Your security operations team gains visibility into attacks that span multiple clouds because the platform correlates events across providers simultaneously. Organizations that implement these platforms see dramatic reductions in breach detection time because fragmented investigations across three separate cloud dashboards no longer consume weeks of effort.
Centralized Key Management Prevents Encryption Chaos
Encryption and data protection services must work across all your clouds simultaneously, with centralized key management that prevents encryption keys from scattering across provider-specific vaults. When one team manages all keys from a single interface, key rotation happens predictably and audit trails remain intact. This centralized approach eliminates the scenario where AWS encryption keys live in AWS Key Management Service while Azure keys sit in Azure Key Vault, creating operational nightmares during incident response.
Cloud-Agnostic Solutions Preserve Your Flexibility
Selecting tools that operate cloud-agnostically rather than favoring one provider creates flexibility to shift workloads and negotiate better pricing as your needs evolve. Your security team should demand native integration with all three major cloud providers from any vendor you evaluate, rejecting solutions that require custom middleware or weekly manual synchronization. The cost of implementing unified tools appears high until you calculate the alternative: another data breach costing $2.7 million according to Forrester’s 2024 findings, plus months of incident response consumed by fragmented investigations. Organizations that consolidate their security tooling reduce complexity, lower total cost of ownership, and finally possess the visibility required to detect attacks that span multiple clouds.
Final Thoughts
Multi-cloud network security stops being optional the moment your organization spreads workloads across multiple providers. The risks we covered-configuration errors, fragmented monitoring, and invisible lateral movement-aren’t theoretical concerns but the exact vulnerabilities that led to 33% of organizations experiencing three or more breaches in 2024 alone. Each breach costs an average of $2.7 million, a price tag that makes proactive security investment look cheap by comparison.
The best practices we outlined create a foundation that actually works: standardized access controls, network segmentation across clouds, centralized logging, and automated policy enforcement. Organizations that implement unified security platforms see dramatic improvements in breach detection speed and operational efficiency because fragmented investigations no longer consume weeks of effort. Your security strategy must shift from reactive patching to proactive architecture, which means selecting tools that work across AWS, Azure, and Google Cloud simultaneously rather than forcing your team to jump between three separate dashboards.
At Clouddle, we understand that managing multi-cloud network security requires more than good intentions-it demands partners who deliver unified visibility and control across your entire infrastructure. Our managed security services combine networking and security into seamless operations, helping organizations implement the architecture outlined in this guide without months of engineering effort. Explore how Clouddle strengthens your multi-cloud security posture and eliminates the blind spots that attackers exploit.


