Protecting your wireless network isn't a single action; it's about building layers of defense. Think of it like securing a building. You need strong locks on the doors (WPA3 encryption), a unique key (not the default password), and restricted access to sensitive areas (network segmentation). This layered strategy is your best defense against unauthorized access and the ever-present risk of data theft.
Why Wireless Network Security Matters More Than Ever
Let's be blunt: an unsecured Wi-Fi network is a glaring business liability. It’s no longer just a minor IT oversight. With so many teams working remotely and a flood of Internet of Things (IoT) devices connecting to our networks—from smart TVs in the conference room to security cameras—the attack surface has exploded. The old-school security methods that worked five years ago are now hopelessly outdated, leaving a wide-open door for attackers to walk right through.
The consequences of a breach are steep. We're talking about more than just a little downtime; a single incident can lead to catastrophic data loss, cripple your operations, and completely shatter the trust you've built with your customers.
The market is reacting to this reality. The global wireless network security market is already valued at around $29.6 billion and is expected to skyrocket past $97 billion by 2034. That's not just a statistic; it’s a clear signal of how seriously businesses are taking these escalating threats.
Core Pillars of Wireless Network Security at a Glance
Before we jump into the nitty-gritty of router settings and firewalls, it’s crucial to establish a solid security foundation. This table breaks down the essential layers that form the backbone of any secure wireless network.
| Security Layer | Primary Goal | Key Action |
|---|---|---|
| Access Control | Ensure only authorized users and devices can connect. | Implement strong WPA3 encryption and unique, complex passwords. |
| Network Segmentation | Isolate critical systems from general traffic. | Create separate networks for guests, IoT devices, and internal staff. |
| Continuous Monitoring | Detect and respond to threats in real-time. | Use network monitoring tools to spot unusual activity or anomalies. |
| Zero Trust | Verify every connection, every time. | Never inherently trust any device or user, even if they're inside the network. |
These principles work together to create a formidable defense, making your network a much harder target for opportunistic attackers.
The Security-First Mindset
A "set it and forget it" approach to Wi-Fi is a recipe for disaster. Security has to be an ongoing process, not a one-time setup. Every single device connecting to your network, whether it's a company-issued laptop or a smart thermostat in the breakroom, is a potential entry point for a hacker.
A modern security strategy must be built on a few key ideas:
- Zero Trust Architecture: The core principle here is simple: trust no one. Assume no user or device is safe by default, and require verification for every single access request.
- Layered Defense: Don't rely on a single point of failure. By implementing multiple security controls, you ensure that if one layer is breached, others are still standing to protect your critical assets.
- Proactive Monitoring: Don't wait for something to break. You should be actively hunting for threats and scanning for unusual activity before it turns into a full-blown incident.
The ultimate goal is to make your network an unattractive target. By layering strong security measures, you raise the bar for attackers. You make it so difficult and time-consuming to breach your defenses that they’ll likely give up and look for an easier victim.
For businesses without a dedicated in-house security team, juggling all these layers can feel overwhelming. This is where outside expertise can be a game-changer. Understanding how to choose managed IT security services can help you find the right partner to build and maintain a truly secure wireless environment, ensuring your defenses are always a step ahead of the threats.
Building Your Security Foundation with Hardware and Encryption

Real wireless network security starts at the source: your physical hardware and the encryption protocols you set. Think of these as the concrete and steel of your network’s defense. Before you even touch a software setting, the first priority is locking down the very devices that broadcast your signal.
The most basic—and most critical—first step is to change the default admin credentials on every single router and access point. It sounds obvious, but you’d be surprised how often it's overlooked. Attackers have massive, easily accessible databases of default logins for every hardware model imaginable. Leaving the default "admin/password" is like handing them the key to your front door.
Hardening Your Hardware Configuration
Once you've swapped out those factory-default credentials for something strong and unique, it's time to start disabling features. A lot of routers and access points come with settings enabled for convenience, but that convenience often comes at the cost of security, creating backdoors you don't even know exist.
Here's what to shut down immediately:
- Disable WPS (Wi-Fi Protected Setup): That little button on the router is tempting, but WPS has well-documented vulnerabilities that make it a prime target for brute-force attacks. The tiny bit of convenience isn't worth the risk. Turn it off.
- Turn Off Remote Administration: Unless you have a specific, documented operational need for it, there's no reason to allow your router to be managed from outside your local network. This feature is a massive attack vector that malicious actors are constantly scanning the internet for.
- Schedule Regular Firmware Updates: Manufacturers don't release firmware updates for fun; they're plugging security holes. Treat these updates with the same urgency as your server or OS patches. If your hardware offers automatic updates, enable them. If not, set a recurring monthly reminder to check manually.
A router running outdated firmware is a ticking time bomb. Every patch you miss is a known vulnerability an attacker can look up and exploit to take over your entire network.
Choosing the Right Encryption Standard
Encryption is what turns your data into unreadable gibberish as it flies through the air, preventing anyone from snooping on your traffic. Picking the strongest encryption standard available is one of the most important calls you'll make when securing a wireless network.
Most modern routers support both WPA2 and WPA3. For a long time, WPA2 (Wi-Fi Protected Access 2) was the industry standard, and it was good for its time. But its time has passed. Today, the only real choice is WPA3. It was designed specifically to fix the known weaknesses of WPA2, and you can learn more about its adoption from recent industry analysis.
WPA3 brings two game-changing improvements to the table:
- Superior Brute-Force Protection: It uses a much more secure authentication handshake, which makes it incredibly difficult for an attacker to guess your password by just trying millions of combinations.
- Individualized Data Encryption: This is huge. Even on a guest or open network, WPA3 encrypts the connection between each device and the access point separately. This stops users on the same network from being able to spy on each other's traffic.
Bottom line: If your hardware supports WPA3, use it. It should be the first thing you enable. For any new equipment you purchase, WPA3 support should be a non-negotiable requirement. This sets a baseline of strong, protocol-level protection that everything else you do will build upon.
Implementing Network Segmentation And Smart Access Control
A flat network, where every device can talk to every other device, is an open invitation for trouble. I've seen it happen: a single compromised device, maybe an employee's personal phone or even a smart thermostat, gives an attacker a free pass to move laterally and hit your critical servers. You have to build digital walls.
This is exactly what network segmentation does. It’s the practice of carving your network into smaller, isolated zones. Think of it like a submarine—if one compartment floods, the sealed bulkheads keep the rest of the ship from sinking. By creating separate SSIDs and VLANs for different types of users and devices, you contain any potential breach.
Carving Out Your Network Zones
In my experience, almost every business can benefit from at least three core segments:
- Corporate Network: This is your inner sanctum, reserved exclusively for company-owned devices used by your team. It’s the only network that should have access to sensitive internal resources.
- Guest Network: A must-have for visitors, clients, and any personal devices. This segment should do one thing and one thing only: provide internet access. It needs to be completely walled off from your corporate network.
- IoT/Operations Network: This is where you stick all those "smart" devices—security cameras, printers, smart locks, even the HVAC system. These gadgets are notoriously insecure, so they need their own isolated playground, well away from your core data.
To make this clearer, let's break down how this works in practice.
Wireless Network Segmentation Strategy
| Network Segment (SSID) | Purpose | Access Level | Key Security Policy |
|---|---|---|---|
| Corporate_WIFI | Company-owned devices for employees. | Full access to internal servers, printers. | Enforce WPA3-Enterprise, 802.1X authentication. |
| Guest_WIFI | Visitors, clients, and personal employee devices. | Internet access only. | Use a captive portal, client isolation, and throttling. |
| IoT_Devices | Smart devices like cameras, thermostats, printers. | Internet access for updates; highly limited. | Block all peer-to-peer traffic; allow-list specific IPs. |
| Secure_Operations | Point-of-sale systems, warehouse scanners. | Access to specific internal servers only. | Deny all internet access; strict firewall rules. |
This table isn't just a template; it's a strategic blueprint. By clearly defining who gets access to what, you're building a network that’s secure by design, not by chance. Each policy adds another layer of defense, making it incredibly difficult for an intruder to cross from a low-security zone into a high-value one.
Defining The Rules Of Engagement With Your Firewall
Once you have your segments, your firewall becomes the gatekeeper. The job here is to control the flow of traffic between these zones. Your starting point should always be a default rule of deny all traffic between segments. From there, you poke very specific, intentional holes only for what is absolutely necessary.
For example, a security camera on the IoT network has zero business communicating with the payroll server on your corporate network. Your firewall rules must explicitly block that connection. This kind of granular control is your best weapon against lateral movement. For a more detailed walkthrough, our guide on how to implement network segmentation for security lays out the entire process.
Layering Your Access Control Methods
Segmentation is the foundation, but you still need to verify who and what is connecting to each network. This starts with strong authentication—and that means getting serious about passwords.
This chart drives the point home better than I ever could.
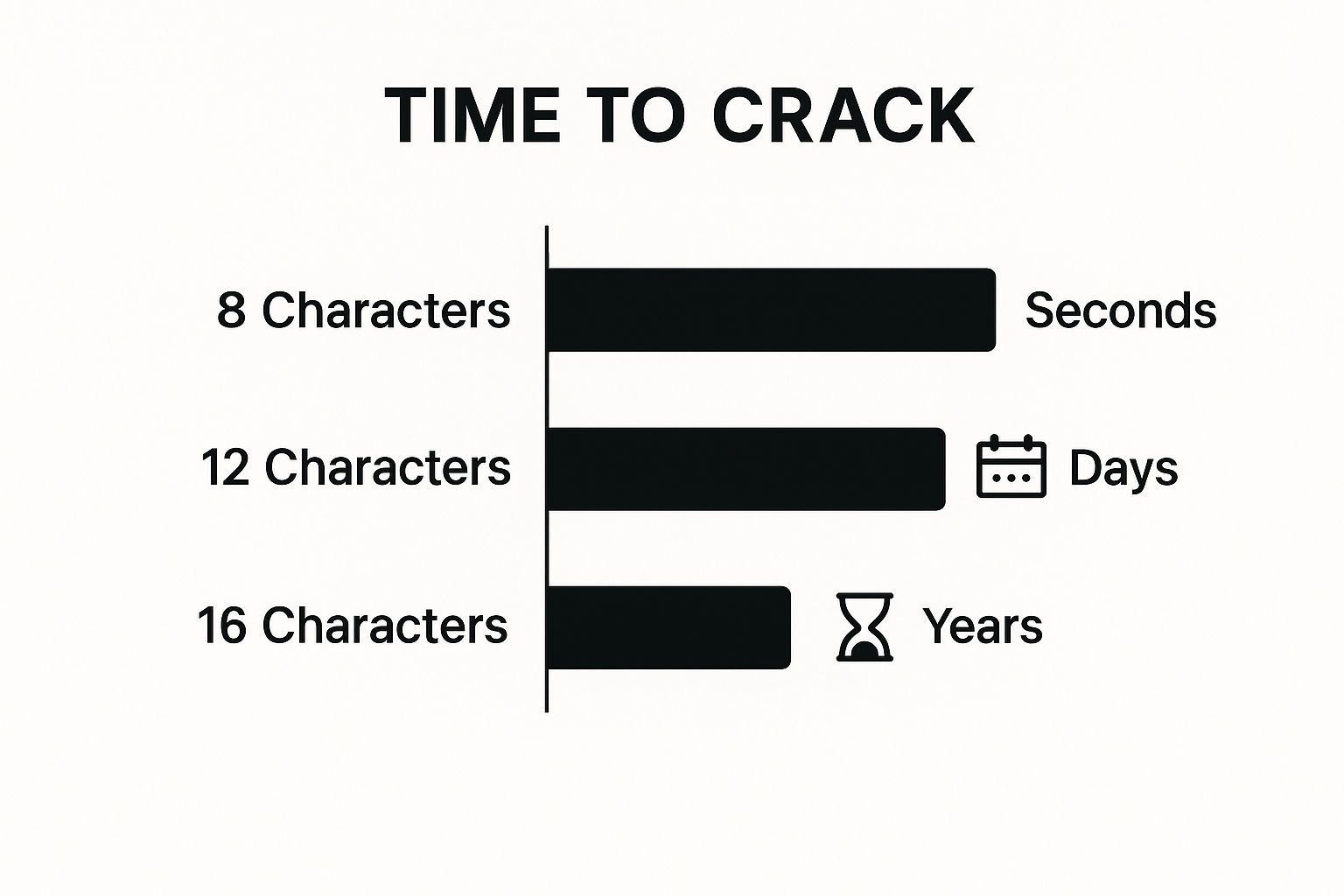
Look at that jump. A simple 8-character password can be cracked in seconds, but increasing the length to 16 characters pushes that time into centuries. This isn't a small improvement; it's a game-changer.
Of course, passwords shouldn't be your only defense. Another practical layer is MAC address filtering. Every device has a unique Media Access Control (MAC) address burned into its network card. By creating an "allow list" of known MAC addresses for your company-owned devices, you can add another barrier to entry on your corporate network.
A quick reality check: A skilled attacker can spoof a MAC address, so don't ever rely on this as your primary security measure. Instead, think of it as a helpful hurdle. It complements strong WPA3 encryption and robust passwords, making an attacker's job just a little bit harder.
Shifting from Reactive to Proactive Network Monitoring
Let's be real: setting up a secure network is a huge win, but your job isn't done. A perfectly configured network is only truly secure at that single moment in time. The real work begins now, shifting your security posture from a static defense to a dynamic, active hunt for threats. The goal here is constant vigilance.
This all starts with getting intimately familiar with the logs from your wireless access points, routers, and firewalls. These aren't just boring text files; they're the real-time story of everything happening on your network. Once you establish a baseline for what "normal" looks like, you can spot the weird stuff instantly—like a sudden spike in failed login attempts or a strange burst of data traffic at 3 a.m.
Putting Active Threat Detection in Place
Watching logs is a good start, but you can't just be a spectator. You need a system that actively finds and shuts down malicious activity. This is where a Wireless Intrusion Prevention System (WIPS) becomes your best friend. Think of a WIPS as a dedicated security guard for your airspace, built specifically to sniff out and neutralize common wireless attacks.
It’s essentially your network’s immune system. A solid WIPS will automatically detect and stop threats like:
- Rogue Access Points: Those unauthorized APs someone plugs into a network jack, creating a massive security hole.
- Evil Twin Attacks: Malicious hotspots that clone your legitimate network's name, tricking users into connecting and handing over their credentials.
- Deauthentication Floods: A nasty denial-of-service attack that boots all your legitimate users off the Wi-Fi.
Without a WIPS, these kinds of attacks can fly completely under the radar until the damage is done. It's the difference between having a smoke detector and having a full sprinkler system that also calls the fire department for you.
Your security configuration sets the rules, but proactive monitoring is what ensures those rules are being followed. It’s the crucial feedback loop that alerts you the moment someone even tries to break them.
Using Intelligent Tools for Smarter Monitoring
As threats get more sophisticated, manually sifting through logs and relying on basic alerts just doesn't cut it anymore. Modern cybersecurity demands a much smarter approach, and that’s where AI-powered monitoring tools are changing the game for IT teams.
These advanced platforms do more than just match known attack signatures. They actually learn your network's unique personality and day-to-day rhythm. This allows them to identify subtle deviations that could signal a sophisticated, zero-day attack. For example, an AI tool might flag a user account that suddenly starts accessing files it has never touched before, even with valid credentials, pointing to a potential account takeover.
This ability to adapt your defenses in real-time is what truly defines proactive security. It moves your team from constantly putting out fires to spotting and stamping out the embers before they can ever ignite. By combining diligent log analysis, a robust WIPS, and intelligent monitoring, you build a network that doesn't just withstand attacks—it actively hunts for them.
Securing Endpoints and Empowering Your Users

You can have the best hardware and the most complex encryption keys, but your network's security still comes down to its weakest link. Nine times out of ten, that weak link is either an unsecured device or a user who doesn't know any better. Technology is only half the equation; the other half is human.
This is where your technical controls meet the real world. Think about it: an employee connects their personal laptop, riddled with malware, to the corporate Wi-Fi. Just like that, they’ve sidestepped your shiny new firewall. The human element isn't an afterthought—it's the final, critical layer in your wireless security strategy.
Establishing Strong Endpoint Security Policies
Every single device that touches your network—laptops, tablets, smartphones—is a potential doorway for an attacker. They all need to meet a consistent security standard before getting a green light. This isn't about micromanaging; it’s about creating a predictable, secure ecosystem.
A Mobile Device Management (MDM) solution is your best friend here. It’s no longer a "nice-to-have." MDM platforms automate policy enforcement, giving you the power to verify that every device meets your baseline security requirements before it connects.
Your MDM should enforce a few non-negotiables:
- Mandatory Antivirus and Anti-Malware: Every device must have approved security software installed and running the latest definitions. No exceptions.
- Full Disk Encryption: If a device is lost or stolen, this is what keeps your company data from being compromised. It’s a simple feature to enable and a massive risk to ignore.
- Required VPN for Remote Access: Any employee working from a coffee shop or their home office must route their traffic through the company's secure VPN. This protects data in transit on untrusted networks.
These policies create a protective shield around each endpoint, drastically cutting the risk of one compromised device taking down the entire network.
Building a Security-First Culture
Beyond the tech, your most powerful security asset is a team that is well-informed and actively vigilant. The goal is to shift the mindset from "security is IT's problem" to "security is everyone's responsibility." This transformation starts with clear, ongoing training and open communication.
Forget the boring, once-a-year security seminar that everyone sleeps through. Instead, run regular, bite-sized training sessions on specific, relevant threats. Phishing simulations, for example, are fantastic because they provide a safe way for employees to see firsthand what a malicious email actually looks like.
A security-aware employee is your best human firewall. When your team can confidently spot a suspicious email or a fake login page, they become your first line of defense, not your biggest liability.
Finally, make it painless for people to report something suspicious. Employees need a simple, no-blame process to flag a weird email or link. The faster your IT team knows about a potential threat, the faster you can shut it down. This combination of hardened devices and empowered users turns your whole organization into a formidable security force.
Your Wireless Network Security Questions Answered
Even with the best-laid plans, tricky questions and unique scenarios always pop up. When you're in the trenches managing a wireless network, you need straight answers to the real-world challenges you face. Let's tackle some of the most common ones I hear from IT pros.
What Is The Single Biggest Mistake To Avoid?
Hands down, the most dangerous mistake is leaving the default admin username and password on your routers and access points. It’s like leaving the keys to your building on the front door with the factory tag still attached.
Hackers run automated scripts 24/7 that do nothing but scan for devices using those default credentials. Think "admin" and "password." Changing these credentials to something long, random, and unique is your first line of defense. It's a simple fix that instantly shuts down one of the most common attack vectors.
If you forget to change the default admin credentials, almost every other security measure you put in place is worthless. An attacker with admin access owns your network, period. Don't skip this foundational step.
Should I Hide My Network Name (SSID)?
Hiding your SSID by disabling the broadcast is a common piece of advice, but honestly, it's pretty outdated. The thinking is "if they can't see it, they can't attack it," but that's just not how it works in practice. This is a classic case of security through obscurity, and it barely slows down a determined attacker.
Here’s why it’s not a defense I’d rely on:
- Easy to Find: Anyone with a basic network scanner can sniff out a "hidden" network in minutes.
- A Pain for Users: Hiding the SSID can cause headaches for your users and devices trying to connect, which means more helpdesk tickets for your team.
Think of it like putting a sheer curtain over your front window. It might stop a casual passerby from peering in, but it does nothing to stop someone who is actually trying to look inside. Your time is much better spent implementing strong WPA3 encryption and enforcing complex passphrases.
How Often Should Wi-Fi Passwords Be Changed?
There’s no one-size-fits-all answer here; it really depends on the network's purpose. For your main corporate network that employees use, changing the password every 90 days is a solid industry standard. It limits the exposure time if a password ever gets compromised.
Guest networks are a completely different beast. Access is temporary, so the password should be, too.
- High-Traffic Areas: If you're managing Wi-Fi in a lobby, retail space, or conference center, change that password daily or at least weekly.
- After Events: Hosted a big client meeting or a public event? Change the password the minute it's over.
This regular rotation makes sure old visitors can't just hop back on your network weeks later. It also prevents your guest password from becoming common knowledge, which is a surprisingly common and easily avoidable risk.
At Clouddle Inc, we build and manage secure, high-performance wireless networks that remove the guesswork for your IT team. Discover our managed Wi-Fi and integrated security solutions at https://www.clouddle.com.


