Network and endpoint security is the backbone of modern cybersecurity. As cyber threats evolve, organizations must fortify their defenses to protect sensitive data and critical systems.
At Clouddle, we understand the importance of a comprehensive approach to safeguarding your digital assets. This blog post will explore practical strategies to strengthen your network and endpoint security, helping you stay one step ahead of potential attackers.
How to Fortify Your Network Defenses
Network security forms the first line of defense against cyber threats. A comprehensive approach to safeguarding digital assets can significantly reduce an organization’s vulnerability to attacks. Let’s explore some practical steps to strengthen your network defenses.
Firewall and Intrusion Detection: Your Digital Sentinels
Strong firewalls and intrusion detection systems (IDS) are essential. Modern next-generation firewalls (NGFW) offer advanced features like application awareness and integrated intrusion prevention. When selecting a firewall, look for ones that provide deep packet inspection and can handle encrypted traffic without significant performance degradation.
For intrusion detection, consider both network-based (NIDS) and host-based (HIDS) systems. NIDS monitor network traffic for suspicious activities, while HIDS focus on individual devices.
Secure Remote Access with VPNs
The rise of remote work necessitates securing off-site connections. Virtual Private Networks (VPNs) encrypt data in transit, making it significantly harder for attackers to intercept sensitive information. When implementing a VPN solution, opt for protocols like OpenVPN or WireGuard, which offer strong security and good performance.
Keep Your Network Up-to-Date
Regular updates and patches are vital for maintaining network security. Unpatched vulnerabilities are directly responsible for 60% of all data breaches. Despite this statistic and the risks that unpatched software presents, many organizations still struggle with timely updates.
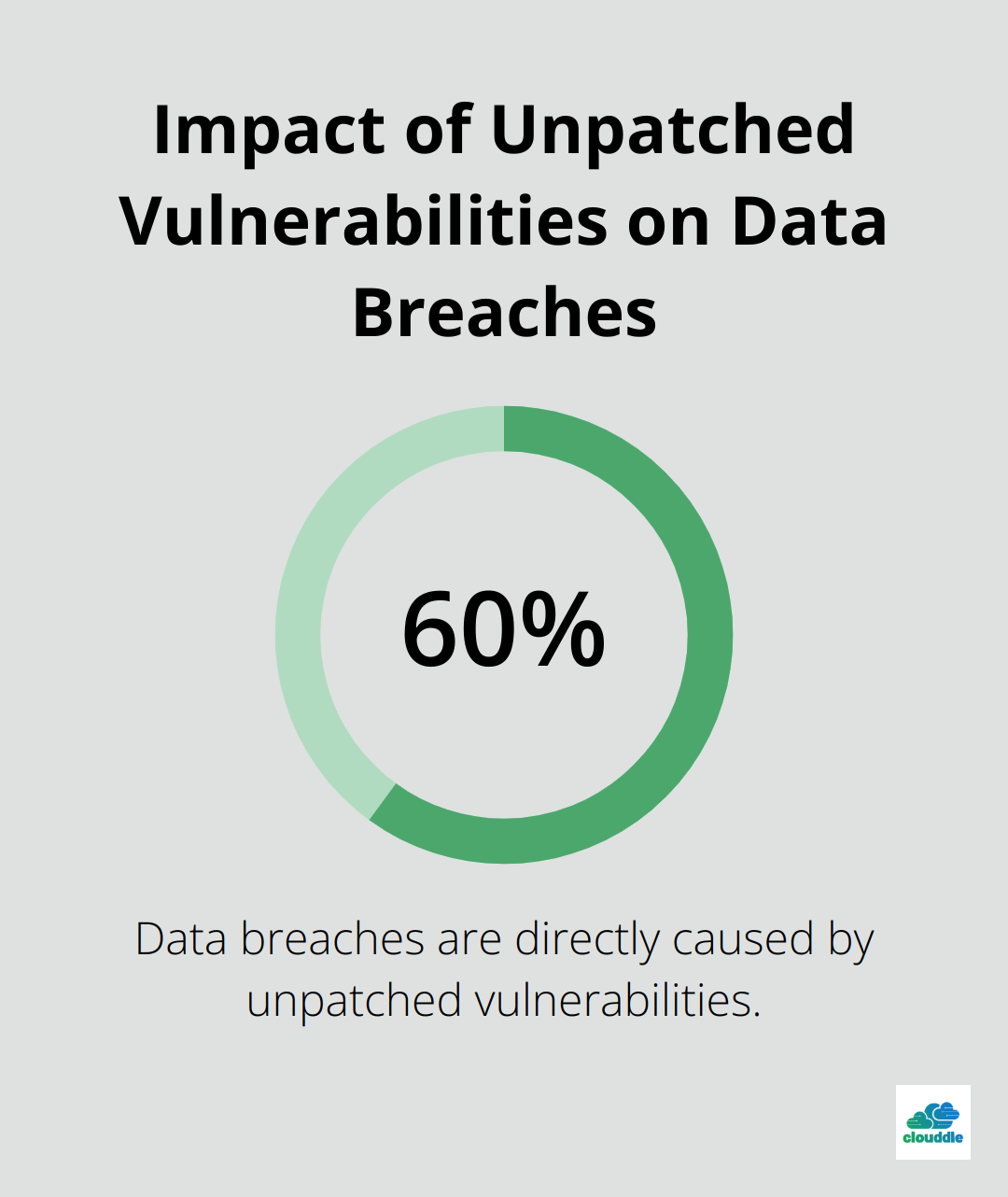
Implement an automated patch management system to ensure timely updates across all network devices (including computers, servers, routers, switches, and IoT devices). Set up a schedule for regular vulnerability scans to identify any missed patches or misconfigurations.
Conduct Regular Security Audits
Network security requires ongoing vigilance. Regular audits and penetration testing help identify weaknesses in your defenses before attackers do. Try to schedule these assessments at least quarterly, adjusting the frequency based on your organization’s risk profile and compliance requirements.
These practices will significantly enhance your network‘s resilience against cyber threats. However, network security is just one piece of the puzzle. The next crucial step is to fortify your endpoints, which we’ll explore in the following section.
Securing Your Endpoints: The Last Line of Defense
Robust Antivirus: Beyond Basic Malware Protection
Modern endpoint security demands more than traditional antivirus software. Comprehensive endpoint protection platforms (EPP) integrate advanced technologies including next-generation antivirus, behavioral analysis, machine learning, threat intelligence, and automated response capabilities.
Solutions such as CrowdStrike Falcon or Symantec Endpoint Protection use AI-driven threat intelligence to detect and prevent both known and unknown threats. These tools identify suspicious behaviors, even when they don’t match known malware signatures.
Keeping antivirus software updated is paramount. A Ponemon Institute study revealed that 57% of data breaches could have been prevented by installing an available patch. Automatic updates ensure your protection remains current against evolving threats.
Multi-Factor Authentication: A Powerful Defense Mechanism
Multi-factor authentication (MFA) significantly reduces the risk of unauthorized access, even when passwords are compromised. Microsoft reports that more than 99.9% of compromised accounts don’t have MFA, which leaves them vulnerable to password spray, phishing, and password reuse.
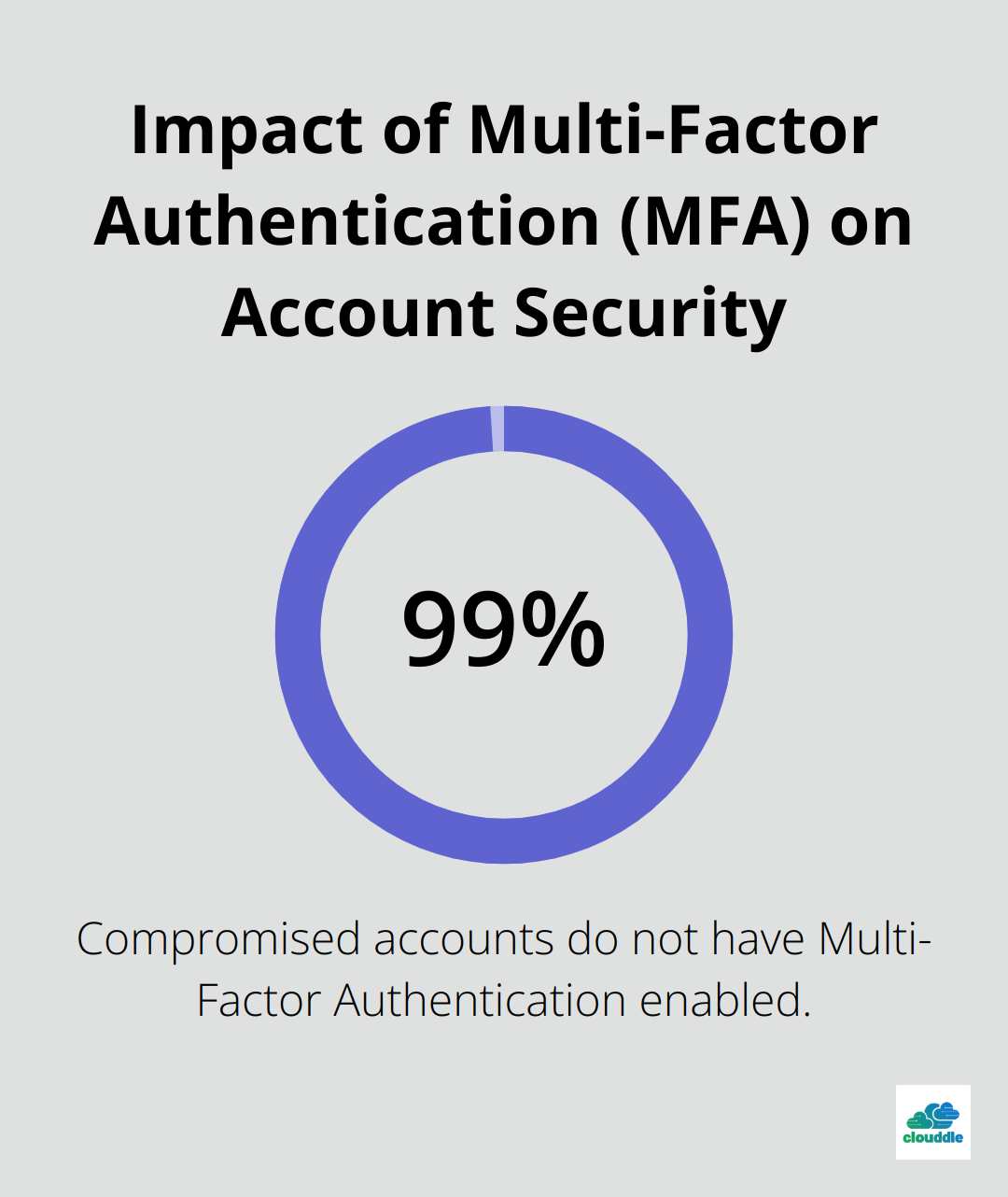
When selecting an MFA solution, consider user experience, integration with existing systems, and support for various authentication methods (SMS, authenticator apps, biometrics). Solutions like Duo Security or Okta offer flexible MFA options tailored to organizational needs.
Advanced Threat Detection with EDR
Endpoint Detection and Response (EDR) solutions provide real-time monitoring and analysis of endpoint activity. These tools quickly identify and respond to threats that may slip past other defenses.
EDR solutions (such as Carbon Black or SentinelOne) offer features including:
- Continuous monitoring and recording of endpoint activity
- Real-time threat detection using behavioral analysis and machine learning
- Automated response capabilities to contain threats quickly
- Forensic tools for in-depth incident investigation
When implementing EDR, ensure it integrates well with your existing security infrastructure. This integration allows for a more holistic view of your security posture and enables faster, more effective responses to threats.
Device Management and Control
Effective endpoint security also involves managing and controlling the devices that connect to your network. This includes implementing policies for bring-your-own-device (BYOD) scenarios and ensuring that all devices meet minimum security standards before gaining network access.
Mobile Device Management (MDM) solutions help organizations enforce security policies, remotely wipe lost or stolen devices, and ensure that all endpoints receive necessary updates and patches. This level of control is essential in today’s diverse device landscape.
As we strengthen our endpoints, we must not overlook the human element in cybersecurity. The next section will explore how employee training and awareness play a vital role in maintaining a robust security posture.
How to Transform Employees into Security Assets
Create a Culture of Security Awareness
Regular security awareness training transforms an organization’s security posture. The 2021 Verizon Data Breach Investigations Report uses pendulums to show breach patterns, classifies incidents, and defines a breach as a confirmed data disclosure to an unauthorized party. To combat this, organizations should implement monthly micro-learning sessions. These short, focused training modules keep security top-of-mind without overwhelming employees.
Use real-world examples and simulations to make training engaging and relevant. For instance, send out fake phishing emails to test employee vigilance. The SANS Institute reports that organizations using this method see a significant reduction in click-through rates on actual phishing attempts.
Implement Strong Password Policies
Strong password policies are essential, but they need to balance security with usability. The National Institute of Standards and Technology (NIST) recommends longer passphrases instead of complex password rules.
Organizations should implement a password manager across their teams. LastPass reports that 85% believe passwords are not going away completely, while 92% see passwordless authentication in their organization’s future. This tool not only generates strong, unique passwords but also eliminates the need for employees to remember multiple complex passwords.

Teach Phishing Detection Skills
Phishing remains a top threat, with Proofpoint’s 2021 State of the Phish Report revealing that 75% of organizations worldwide experienced a phishing attack. To combat this, organizations should teach employees the telltale signs of phishing attempts:
- Urgency or threats in the message
- Mismatched or suspicious URLs
- Requests for sensitive information
- Poor grammar or spelling
Companies should conduct regular phishing simulations to keep employees alert. Organizations that run frequent simulations report up to a 75% reduction in phishing susceptibility (according to Cofense).
Promote Responsible Device Usage
In today’s mobile-first world, employees often use personal devices for work purposes. This practice (known as BYOD, or Bring Your Own Device) can introduce security risks if not managed properly. Organizations should establish clear policies for device usage, including:
- Required security software installations
- Regular device updates and patches
- Guidelines for accessing company data on personal devices
- Procedures for reporting lost or stolen devices
Foster a Security-First Mindset
Security should be integrated into every aspect of an employee’s work routine. Try to encourage employees to think about security in their daily tasks. This approach includes:
- Reporting suspicious activities or potential security breaches
- Properly handling and disposing of sensitive information (both digital and physical)
- Understanding the importance of data privacy and confidentiality
- Actively participating in security initiatives and providing feedback on security measures
Security awareness is an ongoing process. Organizations must regularly update their training content to reflect the latest threats and tactics. This investment in employee training builds a human firewall that complements technical defenses.
Final Thoughts
Network and endpoint security requires a comprehensive approach that integrates various protective measures. Organizations must implement robust firewalls, intrusion detection systems, and advanced endpoint protection platforms to fortify their defenses. Regular updates, patch management, and secure remote access through VPNs play a vital role in maintaining a strong security posture.
Employee training and awareness form a critical component of effective cybersecurity strategies. Organizations should foster a culture of security consciousness, implement strong password policies, and provide ongoing education to transform their workforce into valuable assets against cyber threats. Regular security audits and penetration testing help identify vulnerabilities and ensure the effectiveness of implemented security measures.
Clouddle offers managed IT and security services designed to provide comprehensive protection for businesses across various industries. We combine cutting-edge technology with expert support to help organizations stay ahead of cyber threats and focus on their core business objectives. The cybersecurity landscape constantly evolves, necessitating continuous monitoring and improvement of security measures to maintain robust defenses against emerging threats.


