At Clouddle, we’ve seen firsthand how honeypots in network security can be a game-changer for organizations looking to bolster their defenses.
These clever decoys serve as an early warning system, luring in potential attackers and providing valuable insights into their tactics.
In this post, we’ll explore how to effectively implement and leverage honeypots to enhance your network security strategy.
What Are Honeypots and How Do They Work?
The Essence of Honeypots
Honeypots are cybersecurity mechanisms that use manufactured attack targets to lure cybercriminals away from legitimate targets. These tools provide valuable insights into the tactics and methods of cybercriminals. They mimic vulnerable systems or services, enticing attackers to interact with them. When an attacker engages with a honeypot, their actions are logged and analyzed, offering a wealth of information about their techniques, tools, and intentions.
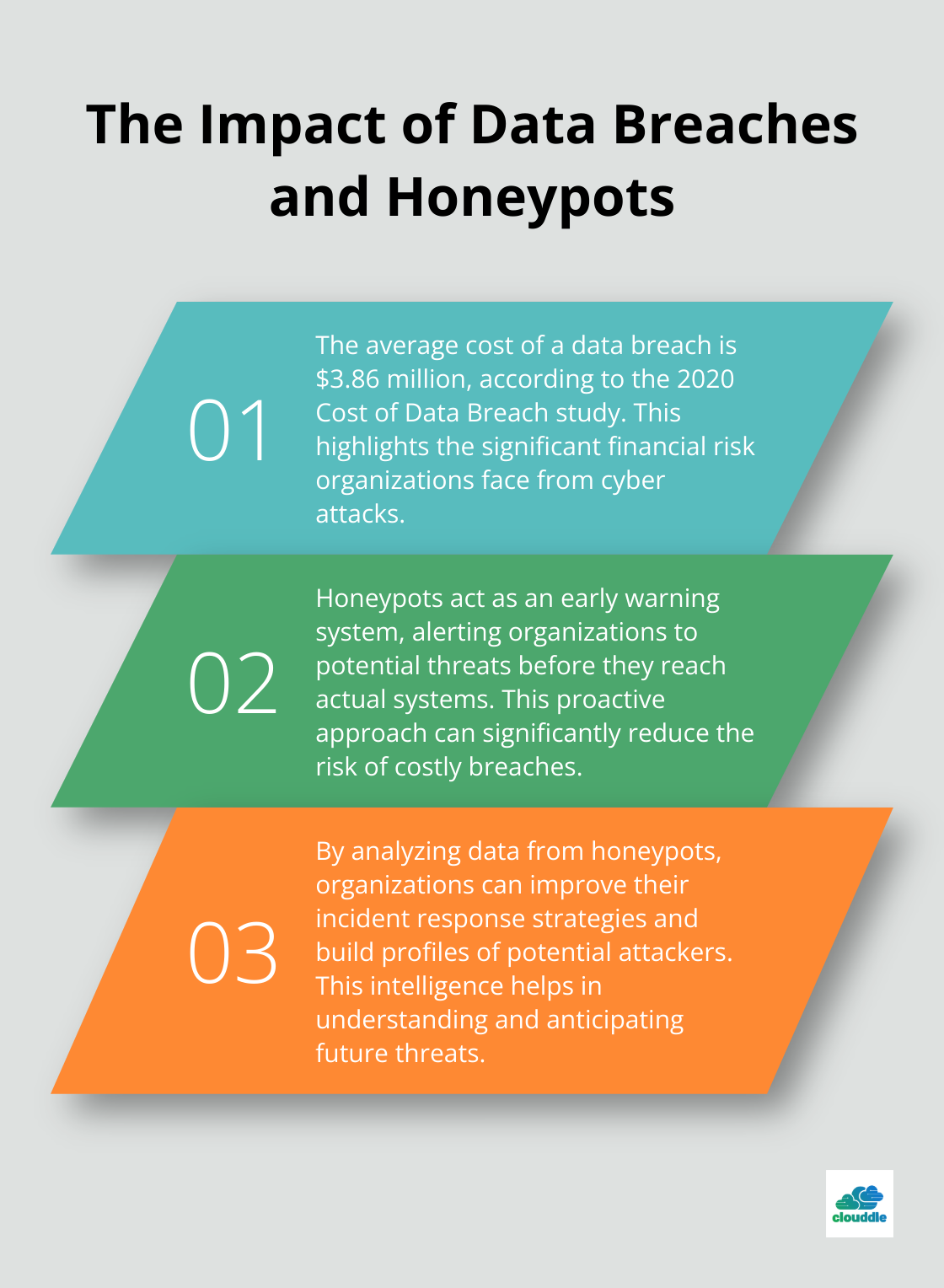
According to the 2020 Cost of Data Breach study, the average cost of a breach is now $3.86 million. This statistic underscores the potential impact of implementing honeypots in security infrastructure.
Types of Honeypots
Low-Interaction Honeypots
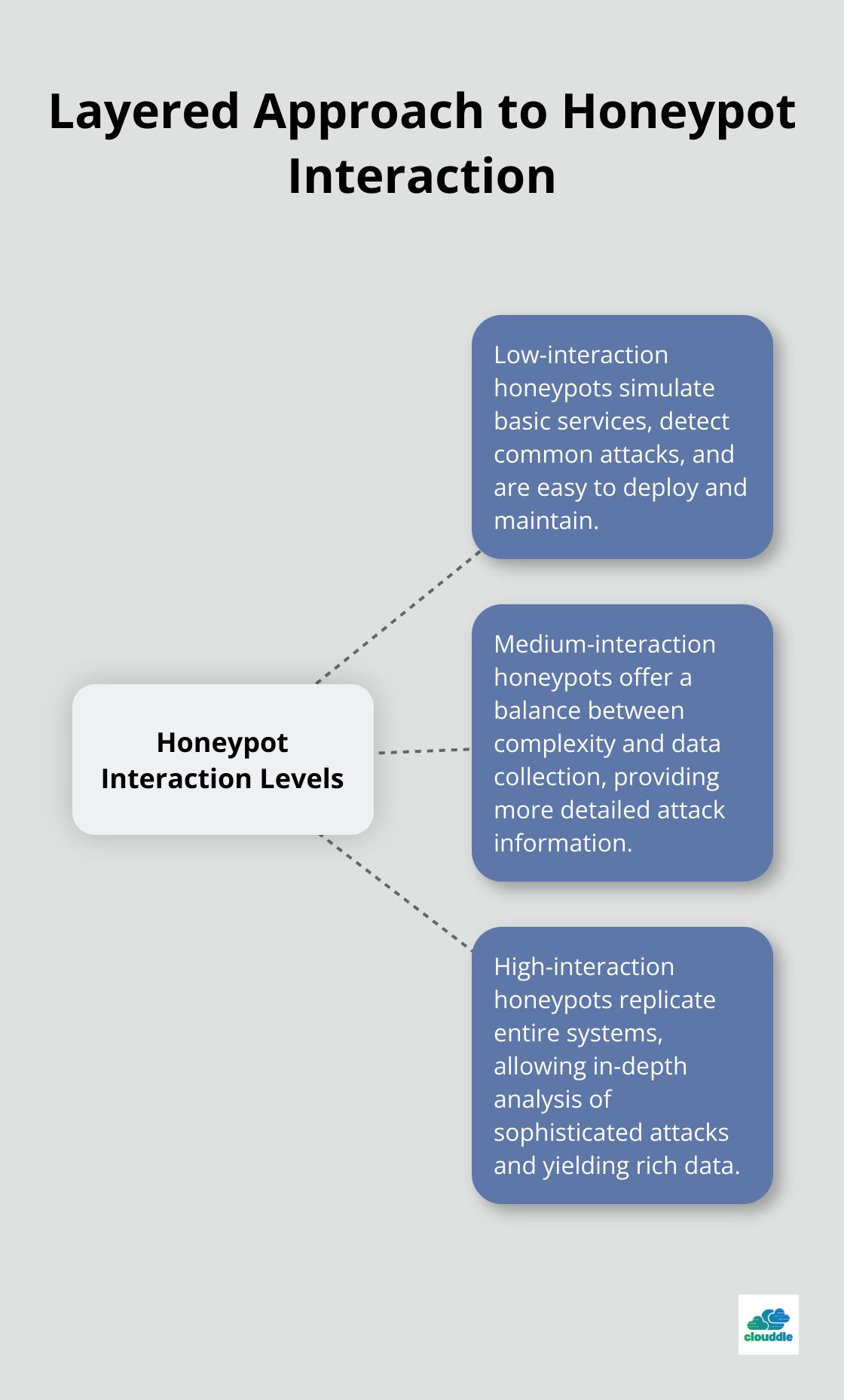
Low-interaction honeypots simulate only basic services and are easier to deploy and maintain. They excel at detecting common attacks and gathering high-level threat intelligence. These honeypots are ideal for organizations looking to start with honeypot technology or those with limited resources.
High-Interaction Honeypots
High-interaction honeypots replicate entire systems, allowing for more in-depth analysis of sophisticated attacks. They provide a more realistic environment for attackers to interact with, yielding richer data. However, they require more resources and careful management to prevent potential security risks.
A combination of both types often yields the best results. Low-interaction honeypots can handle the bulk of basic threats, while high-interaction ones can be strategically placed to capture more complex attack patterns.
Practical Benefits of Honeypot Implementation
- Early Threat Detection: Honeypots act as an early warning system, alerting you to potential threats before they reach your actual systems.
- Reduced False Positives: Unlike traditional intrusion detection systems, honeypots generate fewer false alarms (since any interaction with them is inherently suspicious).
- Improved Incident Response: The data collected from honeypots can be used to fine-tune incident response strategies, making them more effective against real threats.
- Attacker Profiling: Analysis of techniques used against honeypots helps build profiles of potential attackers, aiding in understanding and anticipating future threats.
- Compliance Support: Many regulatory frameworks require proactive security measures. Honeypots can help demonstrate a commitment to cybersecurity, potentially aiding in compliance efforts.
Implementing honeypots requires careful planning and ongoing management, but the insights gained can be invaluable in strengthening overall security posture. The next section will explore how to effectively implement these powerful tools in your network, ensuring you maximize their potential for enhanced security.
How to Implement Honeypots Effectively
Selecting the Right Honeypot Solution
The first step in honeypot implementation involves choosing a solution that aligns with your organization’s needs and resources. Open-source options (like Honeyd and Kippo) offer flexibility and community support. Commercial solutions (such as Attivo Networks and Cymmetria) provide robust, enterprise-grade honeypot platforms.
When selecting a solution, consider factors like deployment ease, scalability, and integration capabilities with your existing security infrastructure. Honeypot interaction can include low, medium, and high levels, allowing for a layered approach to threat detection.
Strategic Placement for Maximum Impact
The placement of honeypots within your network significantly affects their effectiveness. A common strategy involves deploying them in the demilitarized zone (DMZ) to attract external threats. However, placing honeypots in internal network segments helps detect insider threats and lateral movement attempts.
Honeypots and honeynets can prove essential to understand and defend against attacks on IoT, IIoT, and CPS environments by attracting attackers. This finding underscores the importance of a distributed honeypot strategy.
Configuration and Maintenance Best Practices
Proper configuration maintains the believability of your honeypots. Start by mimicking real systems in your network, including operating systems, services, and even fake data. Regular updates keep pace with evolving threats and maintain realism.
Implement robust logging mechanisms to capture all interactions with the honeypot. Tools like ELK Stack (Elasticsearch, Logstash, and Kibana) help centralize and analyze honeypot logs effectively.
Seamless Integration with Existing Security Infrastructure
To maximize the value of honeypots, integrate them with your existing security tools. Connect honeypot alerts to your Security Information and Event Management (SIEM) system for centralized monitoring and correlation with other security events.
Many organizations now leverage automation platforms (like Ansible or Puppet) to manage honeypot deployments at scale. This approach can help reduce honeypot management overhead.
The next chapter will explore how to effectively analyze and respond to the valuable data collected by your newly implemented honeypots, further enhancing your network security posture.
Turning Honeypot Data into Actionable Intelligence
Continuous Monitoring and Analysis
The first step to leverage honeypot data involves the establishment of a robust monitoring system. A Security Information and Event Management (SIEM) tool centralizes and correlates honeypot logs with other security events. This approach provides a holistic view of your network‘s security landscape.
The IBM QRadar SIEM platform (a popular choice in the industry) ingests honeypot data and correlates it with other security logs, which enables real-time threat detection and analysis.
Uncovering Attack Patterns and Trends
Honeypot data reveals emerging threats and attack patterns. Analysis of this data over time uncovers trends that might otherwise remain hidden.
A study by the SANS Institute detected a 300% increase in IoT-focused attacks over a six-month period using honeypots. This insight allows proactive strengthening of defenses against specific types of threats.
Data visualization tools (such as Kibana or Grafana) create dashboards that highlight attack patterns. These visual representations facilitate quick identification of trends and anomalies.
Enhancing Your Security Posture
The insights from honeypot data should directly inform your security strategy. This information helps to:
- Update firewall rules and intrusion detection signatures
- Patch vulnerabilities that attackers actively exploit
- Refine security awareness training for employees
A report by Ponemon Institute revealed that organizations which leverage threat intelligence from sources like honeypots reduced the average cost of a data breach by $2.26 million.

Rapid Incident Response and Threat Mitigation
Swift action becomes crucial when a honeypot detects an attack. An incident response playbook specifically for honeypot alerts outlines steps for:
- Alert validation
- Threat containment
- Attack method analysis
- Countermeasure implementation
Tools like TheHive automate and streamline this process, which reduces response times and minimizes potential damage.
The goal extends beyond mere reaction to threats. Proactive use of honeypot data creates a dynamic, adaptive defense system that stays ahead of attackers. This approach (continuous feedback of insights into your security strategy) forms the cornerstone of an effective cybersecurity posture.
Final Thoughts
Honeypots in network security empower organizations to gain valuable insights into attacker behavior and detect emerging threats. These decoy systems offer a proactive approach to security that can significantly reduce the risk and cost of potential breaches. Organizations should choose solutions that align with their specific needs and integrate seamlessly with existing security infrastructure.
As cyber threats evolve, we expect to see more advanced, AI-driven honeypots that adapt in real-time to changing attack patterns. These systems will likely become more automated, reducing management overhead while providing even more actionable intelligence. The future of network security lies in proactive, intelligence-driven approaches, with honeypots playing a key role in this paradigm shift.
At Clouddle, we understand the importance of robust network security in today’s digital landscape. Our managed IT and security services help businesses across various industries stay protected against evolving cyber threats. We enable our clients to focus on their core operations while we handle their network security needs (including the implementation of honeypot technologies).


