In today’s digital landscape, businesses face an ever-growing array of cyber threats. At Clouddle, we understand the critical importance of robust network security in safeguarding your organization’s assets and reputation.
Managed network security services offer a comprehensive solution to protect your business from evolving cyber risks. This blog post explores the key components of these services and how they can fortify your company’s defenses against potential attacks.
What is Managed Network Security?
A Comprehensive Approach to Digital Protection
Network Security protects your network using different types of technology and processes with a defined set of rules and configurations. It involves the outsourcing of network infrastructure protection to specialized service providers. These experts use a variety of tools and strategies to defend against cyber threats, monitor network activity, and respond quickly to potential breaches.
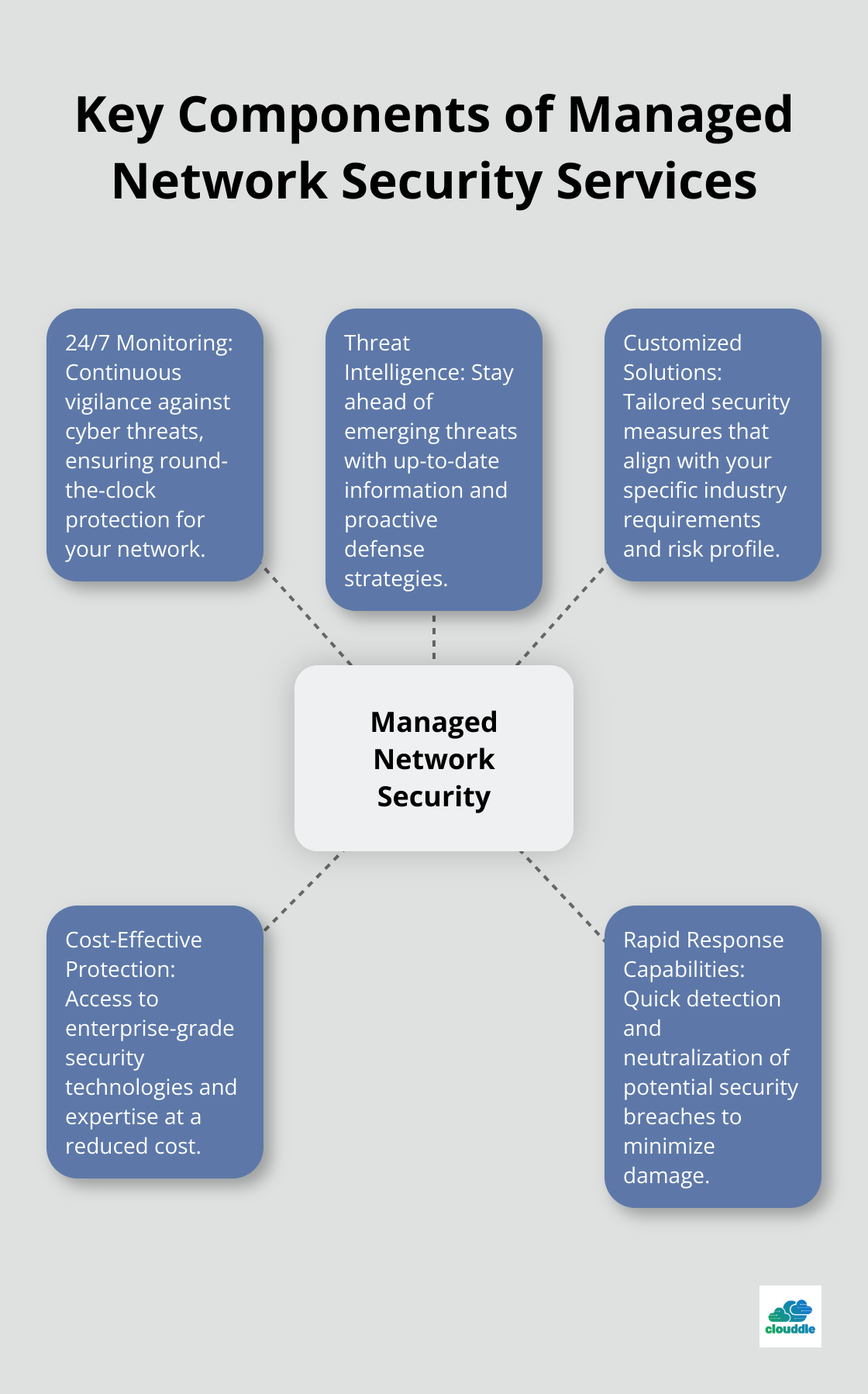
The Advantages of Outsourcing
Outsourcing network security management offers numerous benefits for businesses of all sizes. This approach allows companies to access specialized expertise without maintaining an in-house security team.
Cost-Effective Solutions
One of the most significant advantages of managed network security is its cost-effectiveness. Small and medium-sized businesses often find it challenging to afford the latest security technologies and skilled personnel. Managed services level the playing field, providing enterprise-grade security at a reduced cost.
Round-the-Clock Protection
Effective managed security services operate 24/7, providing continuous monitoring and rapid response capabilities. This constant vigilance is essential in today’s threat landscape, where cyber attacks can occur at any time.
Customized Solutions for Your Business
Every business has unique security needs. Top-tier managed security providers offer tailored solutions that align with specific industry requirements and risk profiles. This customized approach ensures that you don’t pay for unnecessary services while still receiving comprehensive protection against relevant threats.
Staying Ahead of Emerging Threats
The cybersecurity landscape constantly changes, with new threats emerging daily. Managed security services stay ahead of these changes through continuous updates and threat intelligence.
As we move forward, it’s important to understand the common network security threats that businesses face today. The next section will explore these threats in detail, highlighting why robust managed security solutions (like those offered by Clouddle) are more important than ever.
Network Threats: The Hidden Dangers in the Digital Landscape
The Malware and Ransomware Epidemic
Malware and ransomware attacks have become a significant threat to businesses worldwide. In 2021, the largest ransomware payout was made by an insurance company for $40 million, setting a world record. This highlights the substantial financial impact these attacks can have on organizations.
Small businesses face particular vulnerability. The Verizon Data Breach Investigations Report revealed that 46% of all cyber breaches impact businesses with fewer than 1,000 employees. This statistic highlights the necessity for robust security measures across organizations of all sizes.
Phishing: A Persistent and Evolving Threat
Phishing remains one of the most pervasive threats, accounting for 75% of all email-based attacks. These attacks have evolved to become increasingly sophisticated, often mimicking legitimate communications from trusted sources. Employee training has become essential, as 68% of data breaches stem from human error (Verizon’s 2024 Data Breach Investigations Report).

DDoS Attacks: Overwhelming Business Systems
DDoS attacks continue to grow in both scale and frequency. The latest Link11 European Cyber Report shows an alarming trend: the number of DDoS attacks has more than doubled, and they are shorter, more targeted, and increasingly sophisticated. These attacks can overwhelm networks, resulting in significant downtime and financial losses for businesses.
Insider Threats: The Enemy Within
Insider threats (whether malicious or accidental) pose a significant risk to network security. The Ponemon Institute found that the average cost of insider threats increased by 31% in two years, reaching $11.45 million. The implementation of strict access controls and monitoring systems has become essential to mitigate these risks.
As we move forward, it’s clear that businesses need comprehensive strategies to protect their networks from these evolving threats. The next section will explore how managed network security services can provide the robust protection needed in today’s digital landscape.
How to Implement Robust Managed Network Security
Comprehensive Network Assessment
The first step in implementing managed network security involves a thorough network assessment. This process scans your entire network infrastructure for vulnerabilities and potential entry points for cybercriminals. Over 75% of targeted cyberattacks start with an email in 2024, making phishing a primary vector for cybercrime.
Advanced vulnerability scanning tools identify weaknesses in your network, applications, and devices. These vulnerabilities are then prioritized based on their severity and potential impact on your business operations. This assessment forms the foundation of your customized security strategy.

Advanced Firewall Management
Effective firewall management is a cornerstone of network security. Modern firewalls provide deep packet inspection, intrusion detection, and prevention capabilities. A recent study by Gartner found that next-generation firewalls (NGFWs) can reduce the cost of security breaches by up to 90% compared to traditional firewalls.
State-of-the-art firewall solutions adapt to your network’s unique traffic patterns. Firewall rules and policies require continuous updates to defend against the latest threats. Intrusion detection and prevention systems (IDS/IPS) work in tandem with your firewall to identify and block suspicious activities in real-time.
Robust Endpoint Protection
The rise of remote work and bring-your-own-device (BYOD) policies has made endpoint protection more critical than ever. A study by the Ponemon Institute found that 68% of organizations experienced one or more endpoint attacks that successfully compromised data or IT infrastructure.
Advanced endpoint detection and response (EDR) solutions use artificial intelligence and machine learning to identify and respond to threats quickly. These tools provide real-time visibility into all endpoints, allowing for quick detection and neutralization of threats before they spread across your network.
Strict access control measures ensure that only authorized users and devices can access sensitive data and systems. Multi-factor authentication (MFA) is a key component of access control strategy, reducing the risk of unauthorized access by up to 99.9% (according to Microsoft).
24/7 Monitoring and Rapid Incident Response
Continuous monitoring is essential in today’s threat landscape, where cyber attacks can occur at any time. Security operations centers (SOCs) provide round-the-clock monitoring of your network, using advanced security information and event management (SIEM) tools to detect and analyze potential threats.
In the event of a security incident, rapid response teams spring into action. Well-defined incident response plans minimize damage and downtime. IBM’s 2024 Cost of a Data Breach report shows that organizations with an incident response team and plan in place reduced the average cost of a data breach by $2.66 million.
The incident response process includes immediate containment of the threat, thorough investigation of the breach, and implementation of measures to prevent similar incidents in the future. Detailed post-incident reports help you understand what happened and how to strengthen your defenses moving forward.
Final Thoughts
The digital landscape demands robust network security for businesses of all sizes. Managed network security services provide comprehensive protection without extensive in-house resources. These services offer cutting-edge technologies, expert knowledge, and round-the-clock monitoring to safeguard against current and emerging threats.
A thorough assessment of vulnerabilities forms the foundation for a tailored security strategy. Implementing firewalls, endpoint protection, and continuous monitoring systems creates a multi-layered defense against potential threats. These measures support business continuity and sustainable growth in an increasingly connected world.
Clouddle understands the critical role of network security in modern business operations. We offer managed IT and security services designed to provide seamless protection across various industries (including hospitality, multi-family dwelling, and senior living). Our comprehensive approach to digital infrastructure management empowers businesses to focus on their core operations and growth strategies.


