In today’s digital landscape, a solid network and security foundation is essential for every business. At Clouddle, we’ve seen firsthand how proper network infrastructure and robust security measures can protect organizations from cyber threats.
This blog post will guide you through the fundamentals of networking and security, providing practical insights to safeguard your digital assets. We’ll cover everything from basic network components to advanced security protocols, helping you build a resilient IT environment.
Network Basics Every Business Should Know
Types of Networks: Beyond Size
Networks vary in structure and scope. Local Area Networks (LANs) link devices within confined spaces, such as office buildings. Wide Area Networks (WANs) connect multiple LANs across larger geographical areas.
The network type you select significantly impacts your business operations. A well-configured LAN can increase internal communication speed. This boost in efficiency can translate to improved productivity and faster decision-making processes.
Network Components: Essential Building Blocks
Every network relies on key components. Routers direct data traffic between networks, while switches connect devices within a single network. Network Interface Cards (NICs) enable devices to communicate on the network.
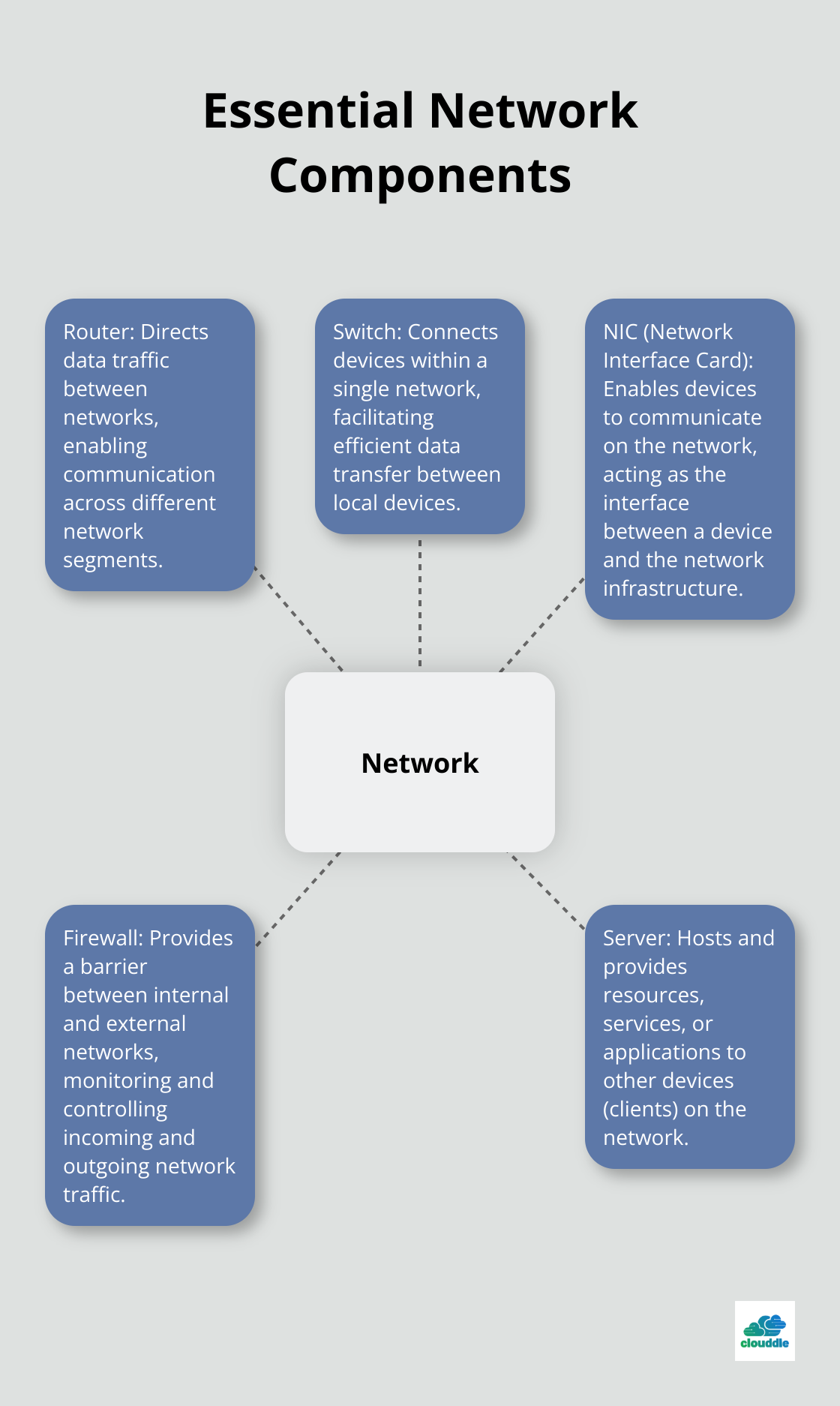
A practical tip: invest in high-quality components. This initial investment pays off through reduced maintenance needs and improved performance over time.
Protocols: The Network’s Language
Protocols set the rules for data transmission across networks. TCP/IP forms the foundation of internet communication. HTTP manages web traffic, while SMTP handles email.
Protocol knowledge is vital for effective troubleshooting. For instance, understanding that most web traffic uses port 80 (HTTP) or 443 (HTTPS) can help you quickly identify and resolve connectivity issues.
Optimizing protocol configurations can lead to significant improvements. This reduction translates to increased uptime and improved overall business continuity.
Network Security: A Fundamental Concern
As we transition to the next section on essential network security concepts, it’s important to note that a solid understanding of network basics forms the foundation for effective security measures. The knowledge of network types, components, and protocols enables businesses to implement targeted security strategies, protecting their digital assets from evolving cyber threats.
How to Protect Your Network
Understanding the Current Threat Landscape
The cybersecurity landscape has transformed dramatically in recent years. This surge highlights the urgent need for robust network security measures.
Ransomware attacks have become more sophisticated. AI-driven malware now alters malicious code in real-time to evade detection. Supply chain attacks exploit vulnerabilities in third-party software, compromising multiple organizations simultaneously.
Implementing Effective Security Policies
Organizations must adopt a proactive approach to combat these threats. A zero-trust architecture is now essential. This approach enhances security by verifying every user and device, ensuring trusted access in today’s evolving IT environments.
Regular risk assessments (including vulnerability scans and penetration testing) play a vital role in network security.
Leveraging Encryption and Authentication
Strong encryption and authentication methods form the backbone of network security. Multi-factor authentication (MFA) enhances security significantly by adding an extra layer of protection. We recommend the implementation of MFA across all critical systems and applications.
For data in transit, robust encryption protocols like TLS 1.3 offer superior protection. For data at rest, full-disk encryption and database-level encryption ensure that intercepted or stolen data remains unreadable to unauthorized parties.
Addressing Emerging Threats
The cybersecurity landscape evolves constantly. Quantum computing poses a future threat to contemporary encryption methods. Organizations should start discussions about the adoption of quantum-resistant algorithms for long-term data protection.
Insider threats, amplified by the hybrid workforce, require the use of behavioral analysis tools and data loss prevention strategies. Continuous employee training in cybersecurity awareness (including phishing detection and secure password practices) significantly strengthens human defenses against cyber threats.
As we move forward, the implementation of these security measures becomes increasingly important. The next section will explore specific tools and technologies that organizations can use to fortify their network defenses and stay ahead of evolving cyber threats.
How to Implement Robust Network Security Measures
At Clouddle, we understand the importance of strong network security measures to protect businesses from evolving cyber threats. This chapter explores practical steps to fortify your network defenses.
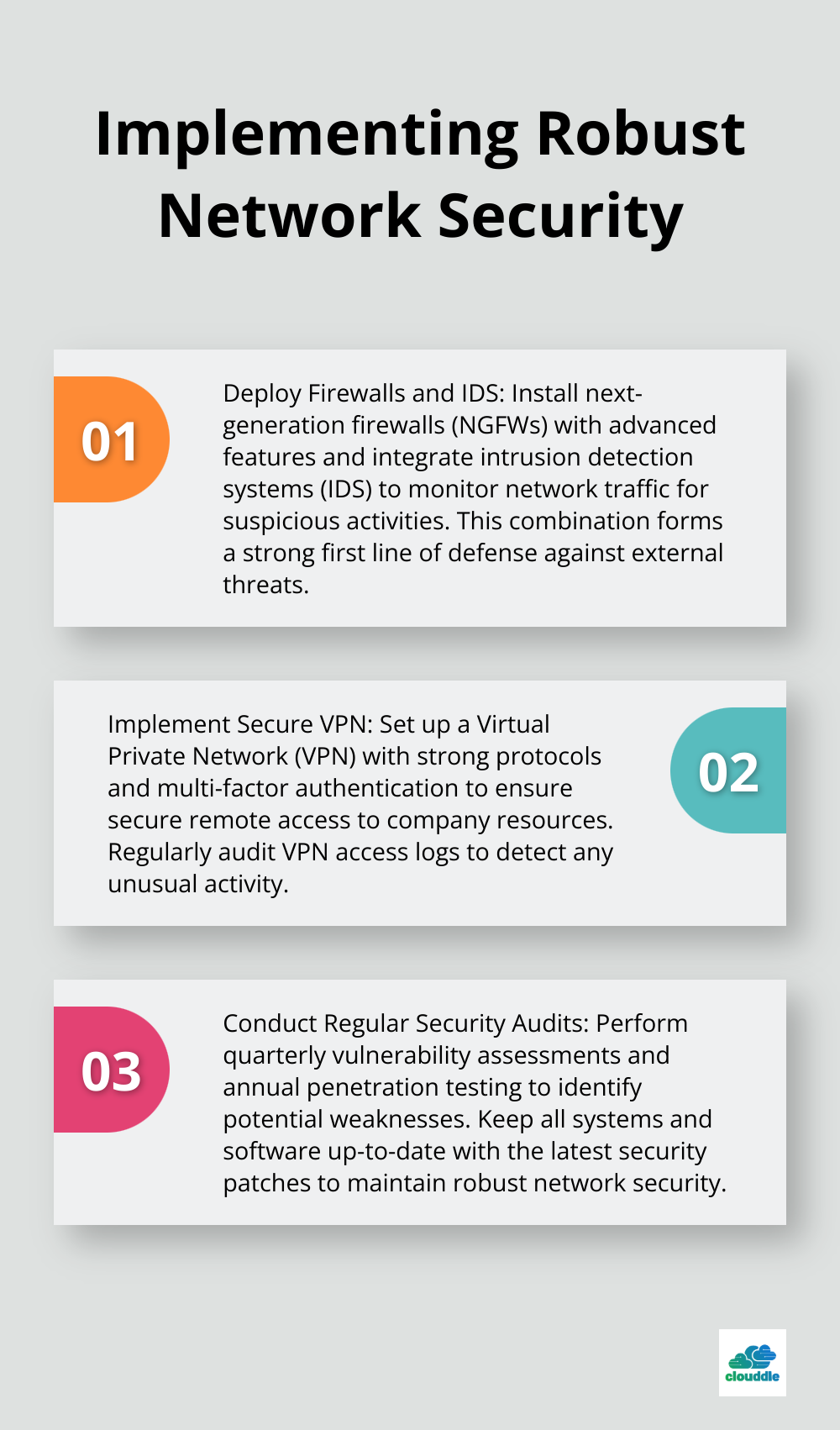
Firewalls and Intrusion Detection Systems: Your First Line of Defense
Firewalls create a barrier between your internal network and external threats. We recommend next-generation firewalls (NGFWs) with advanced features like application awareness and integrated intrusion prevention systems (IPS).
To optimize your firewall protection:
- Block all incoming traffic by default
- Allow only necessary outbound traffic
- Update firewall rules regularly to address new threats
Intrusion Detection Systems (IDS) complement firewalls by monitoring network traffic for suspicious activities. A Network Intrusion Detection System (NIDS) analyzes traffic across your entire network. Cybersecurity statistics show that organizations using both firewalls and IDS can significantly reduce their risk of successful cyberattacks.
Virtual Private Networks: Secure Remote Access
Virtual Private Networks (VPNs) provide secure access to company resources, especially for remote workers. When implementing a VPN solution:
- Select a protocol that balances security and performance (e.g., OpenVPN or WireGuard)
- Enforce strong authentication methods, including multi-factor authentication
- Audit VPN access logs regularly to detect unusual activity
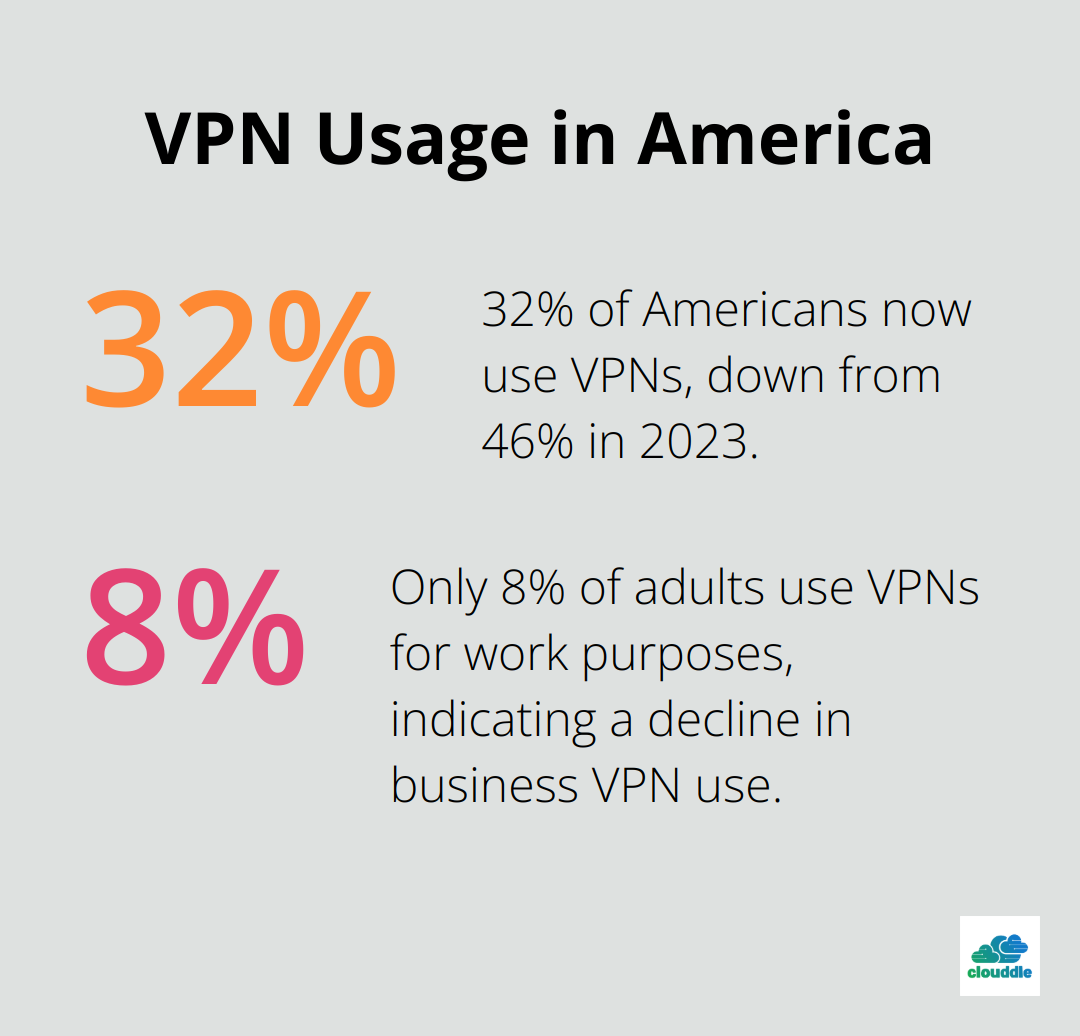
Recent reports indicate that VPN usage has declined since 2023, with only 32% of Americans now using VPNs, down from 46%. Business VPN use continues to shrink, with only 8% of adults using VPNs for work purposes.
Regular Security Audits and Updates: Stay Ahead of Threats
Continuous improvement maintains robust network security. Implement a regular schedule of security audits and updates:
- Conduct quarterly vulnerability assessments to identify potential weaknesses
- Perform annual penetration testing to simulate real-world attacks
- Keep all systems and software up-to-date with the latest security patches
Organizations that regularly conduct security audits and updates can significantly reduce the potential cost of a data breach.
Employee Training and Security Awareness
Create a culture of security awareness within your organization. Implement regular training programs that cover:
- Phishing awareness and email security
- Safe browsing practices
- Password management and multi-factor authentication
- Data handling and privacy policies
Educated employees serve as an additional layer of defense against cyber threats. Organizations with comprehensive security awareness programs can significantly reduce their risk of successful attacks.
Final Thoughts
A strong network and security foundation protects businesses from evolving cyber threats. Organizations must prioritize robust security measures to safeguard digital assets and maintain operational continuity. Regular security audits, updates, and employee training strengthen an organization’s defense against cyber threats.
The future of network security will see AI-driven solutions enhance threat detection and response capabilities. Zero-trust architectures will become more widespread as organizations recognize the need for continuous verification. Cloud security innovations will protect data and applications across diverse environments.
We at Clouddle offer Network as a Service (NaaS) solutions that combine networking, entertainment, and security. Our managed IT, networking, Wi-Fi, and security services empower businesses to focus on growth and efficiency in an increasingly connected world. A solid network and security foundation positions businesses to adapt to future challenges in the digital landscape.


