When you think about business security, what comes to mind? For many, it’s still about stopping a burglar. But that’s an outdated picture. Today, investing in a proper security system is one of the smartest things you can do to protect your entire business—your people, your property, your data, and even your reputation. It’s less about a simple alarm and more about creating a smart, layered defense against a whole new world of threats.
Why Modern Security Is a Business Superpower
Not too long ago, “security” meant a heavy-duty lock and maybe a night watchman. That’s just not enough anymore. The threats we face today are woven together, mixing old-school physical break-ins with sophisticated cyberattacks that can bring a company to its knees. A truly modern security system isn’t just another expense on the balance sheet; it’s a vital part of your daily operations.
This shift from reactive to proactive protection isn’t just about preventing bad things from happening. It brings a sense of calm and actually makes your business run better. Integrated systems, for example, do more than just hit record; they can give you real insights into how your facility is used, help keep your team safe, and make sure you’re ticking all the right boxes for industry compliance.
Bridging the Gap Between Physical and Digital Security
The best security setups don’t treat the physical and digital worlds as separate. They bring them together. Think of it this way: a flimsy digital password can be just as dangerous as a propped-open door. When your physical security (like cameras and keycard access) talks to your digital defenses, you create a much stronger front. This holistic strategy is a huge advantage, and building proactive cybersecurity for business resilience is a cornerstone of that approach.
Here’s what a unified system really gives you:
- A Clearer Picture: You can see everything from one place—whether it’s a delivery truck pulling up to the loading dock or a suspicious login attempt on your network.
- Faster Reactions: Automated alerts mean you’re not wasting time on false alarms. When a real threat is verified, you can act instantly, which dramatically reduces the potential for damage.
- Simpler Management: Handling everything from one central hub—like who has access to which doors—saves a ton of administrative headaches and cuts down on simple human error.
A truly secure business doesn’t see a line between a locked door and a strong password. It understands they are two sides of the same coin, working in concert to protect the entire operation from every possible angle.
Investing in a Stable Future
This move toward smarter, all-in-one security isn’t just a niche trend; it’s a massive market shift. Fueled by new technology and growing concerns over safety, the global market for these systems is exploding. Valued at roughly USD 292 billion recently, it’s on track to hit nearly USD 534.9 billion by 2030. This isn’t just a fad; it’s a clear signal that business leaders see robust security as a fundamental investment.
By getting ahead of the curve with a forward-looking security plan, you’re not just playing defense. You’re laying the groundwork for real, sustainable growth. A secure workplace builds trust with your customers, protects your most valuable assets, and gives your employees the confidence to do their best work. You can dive deeper into designing and implementing these solutions in our complete guide to commercial security systems. It’s an upfront investment that pays for itself over and over in stability, continuity, and peace of mind.
2. The Three Pillars of Business Security
To build a truly effective security plan, you first need to know what you’re working with. Think of it like assembling a team for a critical project—each member needs a specific skill set. In the world of business security, that team is made up of three core components, and each one plays a vital, distinct role.
When you understand how video surveillance, access control, and intrusion alarms work together, you move beyond just having “security” and start building a comprehensive shield around your people, property, and assets.
This diagram shows how these pillars support a complete security strategy.
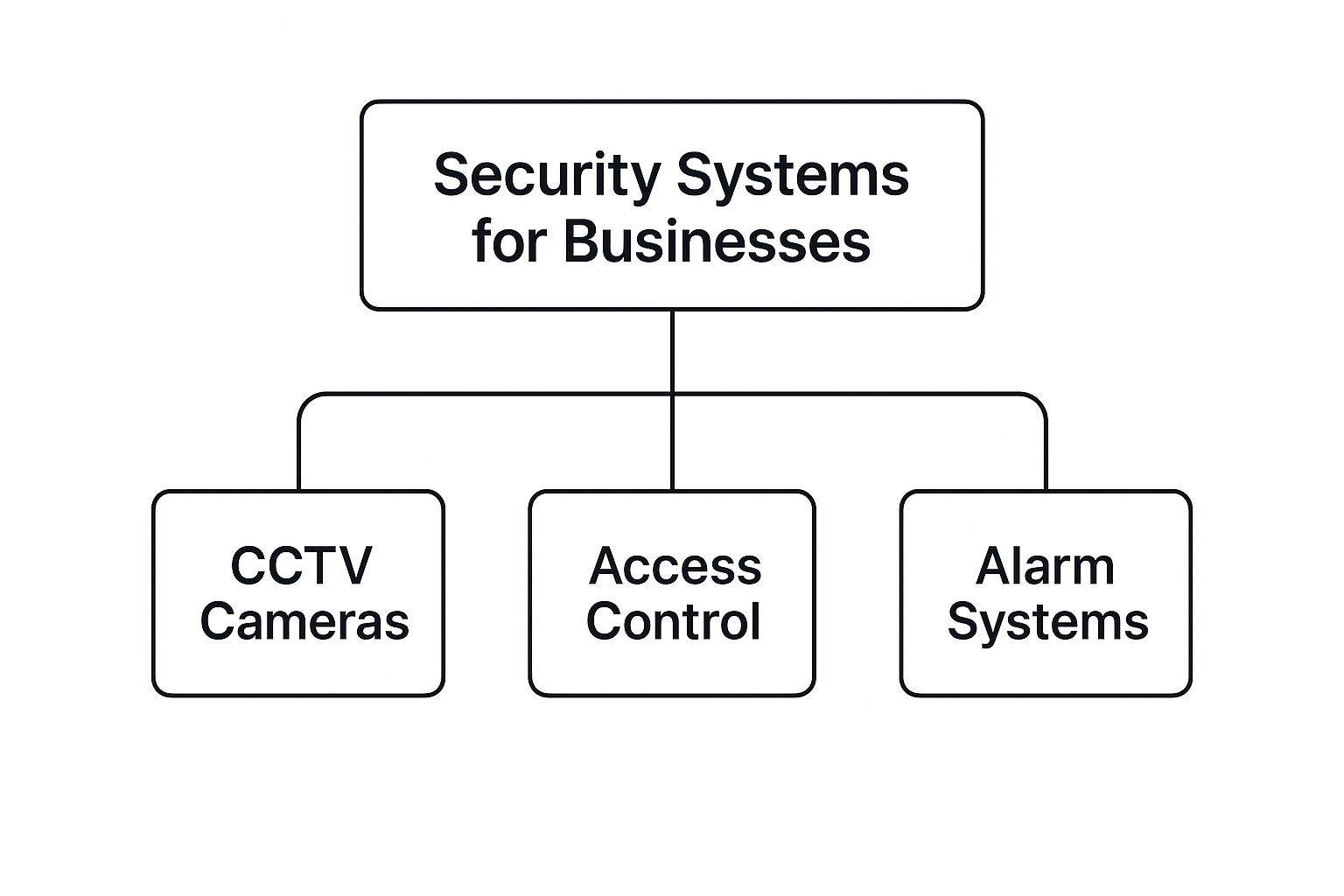
As you can see, each element—CCTV, access control, and alarms—forms a foundational layer. Let’s dive into what each of these building blocks actually does for your business.
Video Surveillance: Your Eyes on the Ground
When people think of security, cameras are usually the first thing that comes to mind. Video surveillance, or CCTV, is the most visible part of a system, acting as your eyes and ears, recording everything that happens on your property, 24/7. But today’s cameras are much more than simple recording devices.
For a retail shop, cameras are an obvious deterrent to shoplifters, but they can also reveal which aisles get the most foot traffic, helping you optimize your store layout. In a warehouse, they do more than just catch theft; they can help you verify shipments and ensure your team is following critical safety protocols on the loading dock.
Modern video surveillance delivers three key benefits:
- Deterrence: The simple sight of a camera is often enough to make a potential thief think twice, protecting you from both internal and external threats.
- Evidence: When an incident does happen, clear, high-resolution footage is undeniable proof for law enforcement or internal investigations. It’s no longer a “he said, she said” situation.
- Remote Monitoring: IP-based cameras let you check in on your business from anywhere. Whether you’re at home or on vacation, you can pull up a live feed on your phone and have instant peace of mind.
Access Control: The Digital Gatekeeper
If cameras are your eyes, access control is the gatekeeper. This technology manages who can go where and when, replacing old-school metal keys that are all too easy to lose, copy, or steal.
Imagine you have a server room with thousands of dollars of equipment and sensitive data. With an access control system, you can program it so only the IT manager’s keycard works on that door, and only during specific hours. Try doing that with a standard lock and key—it’s impossible.
Access control isn’t just about locking doors; it’s about creating an intelligent, dynamic environment. You’re not just keeping the wrong people out, you’re making sure the right people have seamless access, all while generating a perfect audit trail of every entry.
These systems use everything from key fobs and mobile phone credentials to biometrics like fingerprints. The technology that powers this often runs on the same IP-based networks as modern VoIP communication systems, sending data securely for real-time control and monitoring.
Intrusion Detection: Your Digital Nervous System
Finally, we have intrusion detection, which acts as the nervous system for your entire security setup. Its one job is to sense trouble—like a break-in or unauthorized movement—and trigger an immediate, decisive response.
The system relies on a web of sensors. When a motion detector picks up movement in a closed office after hours, or a door contact senses a forced entry, it doesn’t just sit there. It instantly sends a signal that can set off a deafening siren, push an alert directly to your smartphone, and, most importantly, notify a professional monitoring station to dispatch help. This is what keeps your business safe when no one is around, making it a non-negotiable for after-hours protection.
To help you visualize how these pieces fit together, here’s a quick breakdown of their core functions and ideal applications.
At-a-Glance Comparison of Core Security Components
| Security Component | Primary Function | Best For |
|---|---|---|
| Video Surveillance | To deter, record, and provide visual evidence of activity on your property. | Businesses needing visual oversight, evidence for incidents, and remote monitoring of operations. |
| Access Control | To control and track who can enter specific areas and at what times. | Offices with sensitive areas, multi-tenant buildings, and any business wanting to ditch traditional keys. |
| Intrusion Detection | To detect unauthorized entry and trigger an immediate alarm response. | Protecting a property after hours, securing high-value assets, and ensuring a rapid response to break-ins. |
In short, these three components are the essential tools in your security arsenal. Each one tackles a different problem, but when combined, they create a powerful, layered defense that is far stronger than any single element on its own.
Choosing Your System Architecture: On-Premise vs. Cloud
Okay, you’ve got a handle on the essential parts of a business security system. Now comes the big decision: where does all that data live and how do you manage it? This choice between an on-premise or a cloud-based architecture will shape everything—from what you pay upfront to how you check your cameras on the go.
Let’s use an analogy. Think of it like your personal movie collection.
An on-premise system is like having a massive shelf of Blu-rays. You own everything. The discs, the player, the entertainment center—it’s all yours. You have complete control, but you’re also the one who has to buy it all, find space for it, and fix the player when it breaks.
A cloud-based system is like having a Netflix subscription. You don’t own any physical discs. Instead, you get instant access to a huge library from anywhere, on any device. The streaming service takes care of all the storage, updates, and maintenance behind the scenes. You just log in and press play.

The On-Premise Model: Traditional Control
With an on-premise setup, all your security gear—servers, Network Video Recorders (NVRs), and other storage devices—is physically located at your business. Every piece of video and every access log is recorded and kept right there on-site.
This model gives you absolute control over your data, which is non-negotiable for some industries with strict data location rules. The system keeps recording even if the internet goes down, though you’ll need a connection to view anything remotely. But this level of control comes with a lot of responsibility.
The biggest hurdle is the hefty upfront investment in hardware. You’re buying everything yourself. On top of that, you’re on the hook for all maintenance, software updates, and repairs. If a hard drive fails, it’s your problem to solve. This approach also has a major weak spot: if a fire, flood, or break-in destroys your recorder, your security footage is gone forever.
The Cloud-Based Model: Modern Flexibility
Cloud security systems work differently. Your cameras and sensors connect to the internet, sending their data to highly secure data centers managed by your provider. You then tap into your system using a simple web browser or a mobile app.
For most businesses today, this model just makes more sense. Here’s why:
- Lower Upfront Costs: Instead of a huge bill for servers and recorders, you pay a predictable subscription fee. It’s an operating expense, not a capital one.
- Go-Anywhere Accessibility: Check live feeds, review footage, and get alerts from your phone, tablet, or laptop, no matter where you are.
- Effortless Updates: The provider pushes out all software updates and security patches automatically. Your system stays secure and up-to-date without you lifting a finger.
- Far Better Data Security: Your video evidence is safe from on-site disasters. Good cloud providers use powerful encryption and store your data in multiple locations, a level of protection most small businesses could never afford to build themselves.
The real game-changer with cloud architecture is its resilience. If the worst happens—a thief smashes a camera or steals the recorder—the crucial footage is already safe in the cloud, ready to be used as evidence.
The Hybrid Model: The Best of Both Worlds
You don’t always have to choose one or the other. A hybrid model cherry-picks the best features from both worlds, combining on-premise hardware with cloud services.
A common example is recording high-resolution video 24/7 to a local NVR but also sending important motion-triggered clips to the cloud for safekeeping.
This gives you a powerful, balanced solution. You get the day-to-day reliability of local recording (which isn’t dependent on your internet bandwidth) alongside the ironclad backup and remote access that the cloud provides. For organizations with complex needs, like managing a sophisticated access control for business system while ensuring video evidence is always protected, a hybrid setup is often the perfect fit. It’s all about balancing control with convenience.
Unlocking Advanced Security Features
If the basic security components are the foundation of your building, these advanced features are the intelligent, automated systems that run inside it. They elevate your security from a simple alarm into a proactive guardian that thinks, analyzes, and responds. We’re moving beyond just recording events to understanding them.
This is what turns a good security setup into a great one.

Think of it like this: a standard camera just watches passively. An advanced system, on the other hand, acts more like a seasoned security guard. It doesn’t just register “movement”—it knows the difference between a threat and a false alarm, making smart decisions in the moment. This is the heart of today’s top-tier security systems for businesses.
AI-Powered Video Analytics
The single biggest game-changer in modern surveillance is AI-powered analytics. Forget getting pinged every time a tree branch sways in the wind or a stray cat wanders through the parking lot. AI has the intelligence to tell the difference between a real event and meaningless background noise, which drastically slashes the false alarms that plague older systems.
These smart cameras can be taught to identify specific objects and behaviors, unlocking powerful new ways to protect your property and streamline operations.
- Object Recognition: The system can tell a person from a vehicle or an animal. This means you can create a rule to only get an alert when a person enters a restricted zone after hours, completely ignoring passing cars.
- Loitering Detection: Perfect for retail storefronts or sensitive entryways, the system can automatically flag someone who has been lingering in one spot for too long, giving you a chance to investigate before something happens.
- Line Crossing Alerts: You can literally draw a virtual “line” across a doorway or along your property’s edge. An alert is triggered only when that line is crossed, making it an incredibly precise tool for monitoring your perimeter.
The real goal of AI analytics isn’t just to record what happens, but to provide critical context. It transforms a flood of raw video into a short, manageable list of actionable alerts, so your team can focus on what truly matters.
The Rise of Biometric Access Control
Keycards and fobs are a decent step up from old-school metal keys, but they have a glaring weakness: they can be lost, stolen, or passed around. Biometric access control slams that door shut by using a person’s unique biological traits as their key. You can’t exactly “forget” your fingerprint, making it a far more secure method.
The most common forms you’ll see are:
- Fingerprint Scanners: A reliable and surprisingly cost-effective way to lock down doors to offices, server rooms, or any other sensitive area.
- Facial Recognition: This offers a completely frictionless experience. Employees can simply walk up to a door, and it unlocks automatically without them ever having to touch a scanner or pull out a card.
- Iris Scanners: For maximum security, iris scanners provide an incredibly high degree of accuracy. You’ll typically find these protecting high-value assets or critical data centers.
This technology is no longer science fiction; it’s becoming more affordable and dependable every year. For any business that needs absolute certainty about who is accessing specific areas, biometrics are the new gold standard.
Integrated Mobile Management
The power to manage your entire security system from the palm of your hand is no longer a nice-to-have feature—it’s an absolute essential for any modern setup. A single, centralized mobile app puts complete control at your fingertips, whether you’re across the country or just in another part of the building.
This level of integration delivers incredible convenience and a much faster response time. You can arm or disarm the system remotely, check live camera feeds while on vacation, or grant temporary access to a delivery driver without leaving your desk. When an alert hits, you get an instant notification with a video clip, letting you verify the threat and take immediate action.
Just as physical security has evolved, so has digital protection. In today’s tech-driven companies, securing complex IT infrastructure is just as vital as protecting physical entry points. For example, understanding Kubernetes Security Best Practices is crucial for safeguarding the software that runs the business.
By weaving these advanced features together, businesses can build a security posture that isn’t just tougher to break, but also far smarter and more efficient to manage day-to-day.
A Practical Guide to Picking Your Security System
Feeling a bit lost in the sea of options for business security systems? That’s completely normal. The trick is to forget about the fancy tech for a minute and focus on a simple, logical process. Choosing the right system isn’t about buying the most expensive camera; it’s about finding a solution that solves your unique problems.
This framework will walk you through everything, from the initial assessment to making that final call, so you end up with the protection your business actually needs.

The first step is surprisingly low-tech: walk around your own property and try to see it through the eyes of someone who means you harm.
Put on Your “Bad Guy” Hat and Do a Risk Assessment
Before you even glance at a product catalog, you need to understand where you’re vulnerable. Seriously—think like a burglar, a disgruntled former employee, or an opportunistic shoplifter. Where are your weak spots?
Take a literal walk through and around your business. Pay close attention to every way in and out, not just the front door. Look for poorly lit corners, hidden side doors, ground-floor windows, and any spot along your perimeter that offers good cover for someone trying to stay hidden.
A solid risk assessment answers questions like:
- Where are the blind spots? Pinpoint every area, inside and out, where someone could move around without being seen.
- What are your crown jewels? This isn’t just about expensive equipment. Think about server rooms holding sensitive data, inventory stockrooms, or cash offices.
- Who goes where? Map out the daily traffic patterns of employees, customers, and vendors. This will tell you a lot about the access control you might need.
This simple audit turns vague security worries into a concrete list of problems you need to solve.
Set Specific, Achievable Security Goals
Once you know your risks, you can define what success looks like. “Better security” is just wishful thinking. You need specific, measurable goals that a system can actually help you hit. These goals will be your North Star when you start comparing security systems for businesses.
For instance, instead of a vague goal like “stop theft,” get specific:
- Goal 1: Cut inventory shrinkage by 15% in the next fiscal year by monitoring the stockroom and all POS stations.
- Goal 2: Eliminate unauthorized access to the server room by installing a biometric lock.
- Goal 3: Make employees feel safer by adding 24/7 video monitoring to the parking lot and back entrance.
Having these concrete goals makes it a breeze to evaluate whether a proposed system is the right tool for the job.
Budget for the Whole Picture, Not Just the Box
One of the biggest mistakes business owners make is budgeting only for the initial hardware purchase. A realistic security budget has to cover the entire life of the system. That means accounting for the upfront cost, installation fees, potential network upgrades, and—this is a big one—ongoing monitoring and service fees.
Your budget should reflect the total cost of ownership, not just the purchase price. A cheaper initial system with high monthly fees or poor support can end up costing you far more in the long run.
Think of it as an operational investment rather than a one-time purchase. For many companies, a predictable monthly fee that bundles hardware, software, and support is much easier to manage than a huge capital expense. Some providers even offer zero-down-payment deals that roll everything into one operational cost. This is a common approach with managed security solutions, which can simplify budgeting and guarantee you always have support.
Vet Your Vendors Like You’re Hiring a Key Employee
Choosing your security provider is every bit as important as choosing the technology itself. The right company becomes a long-term partner in keeping your business safe. You’ll want to find a provider with a proven track record, especially with businesses like yours.
When you’re talking to potential vendors, get right to the point with targeted questions:
- Do you own and operate your own monitoring center?
- What are your average emergency response times?
- Can your systems integrate with other business software we already use?
- What, exactly, does your support and maintenance plan cover?
More and more, businesses are looking for integrated systems that bring all their security functions—cameras, alarms, access control—into one central platform. It boosts efficiency and gives you a much clearer picture of what’s happening. The right vendor should be more than capable of delivering this kind of unified solution.
Common Questions About Business Security Systems
When you get down to the brass tacks of choosing a security system, it’s the practical questions that matter most. We get it. To help you feel confident about your decision, we’ve compiled the questions we hear most often from business owners, along with some straight-to-the-point answers.
How Much Should I Budget for a Business Security System?
This is always the first question, and the honest answer is: it really depends on what you need to protect. Budgeting for security systems for businesses isn’t just about the upfront price tag on the cameras; it’s about the total cost of keeping your business safe over the long haul.
You’ll need to think about a few things: the size of your property, how complex your day-to-day operations are, and the level of protection you’re comfortable with. For a small retail shop, a solid basic setup might start in the low thousands. But for a sprawling warehouse or a multi-floor office building, you could be looking at an investment of tens or even hundreds of thousands for a system that covers every angle.
The main costs break down into three areas:
- Initial Hardware: This is all the physical gear—cameras, sensors, access control readers, and the recording devices.
- Installation Fees: Getting a pro to install it ensures everything is wired correctly and placed for maximum effect.
- Ongoing Subscriptions: Think of this as the “service” part of your security service. It covers things like cloud storage for your footage, software updates, and professional monitoring.
Instead of getting hung up on the initial sticker price, try to see it as an investment. A good system doesn’t just cost money—it saves money by cutting down on theft, potentially lowering your insurance premiums, and even helping you spot operational hiccups. The best first step is always to get a few quotes from trusted vendors based on a professional risk assessment of your property.
Can I Install a Business Security System Myself?
You certainly can, especially with all the DIY systems out there. But for a business, we almost always recommend professional installation. The stakes are just higher than they are at home. A security system is only as reliable as its installation, and a small mistake—a camera blind spot, a loose wire—can create a huge security hole.
A professional installer does more than just screw cameras to a wall. They’re trained to think like a thief, placing cameras to eliminate blind spots. They know the local building codes to ensure wiring is safe and compliant, and they know how to make sure all the different parts of your system—from the keypad to the cameras to the sensors—actually talk to each other flawlessly.
For anything more complex than a few standalone cameras—especially systems that tie in access control, fire alarms, and professional monitoring—professional installation isn’t just a good idea. It’s essential for making sure the system actually works when you need it most.
Paying for a professional install is a small price for the peace of mind you get knowing your business is properly protected.
What Is the Difference Between Active and Passive Monitoring?
This is a big one, because it determines what actually happens when an alarm is triggered. The key difference is who responds.
With passive monitoring (sometimes called self-monitoring), you are the first responder. The system sends an alert directly to your phone or computer, and it’s up to you to check the live feed, figure out if it’s a real threat or just the wind, and then decide whether to call the police. This can work for very small businesses with low-risk environments, but it puts all the pressure on you.
Active monitoring is completely different. It connects your system to a 24/7 professional monitoring center staffed by trained security experts. When an alarm goes off, they’re the ones who get the signal.
Here’s the typical play-by-play:
- A sensor is tripped at your business.
- The signal goes directly to the monitoring station.
- A trained operator immediately verifies the alarm, often by looking at a live video feed to confirm it’s not a false alarm.
- Once the threat is confirmed, they dispatch the police, fire department, or other emergency services for you.
For most businesses, active monitoring is the way to go. It guarantees a fast, professional response, especially when you’re not there.
How Do Cloud-Based Systems Protect My Data?
It’s natural to feel a little uneasy about storing sensitive security footage “in the cloud.” But for modern systems, it’s actually far more secure than keeping it on a hard drive in your back office. Reputable cloud security providers build in layers of protection that would be nearly impossible for a single business to manage on its own.
First, your data isn’t just sitting on-site where it can be stolen or destroyed. Video footage and access logs are encrypted and transmitted to highly secure data centers. This means if there’s a fire, a flood, or a thief who knows to grab the recorder, your evidence is still safe and sound.
Second, the best cloud providers use incredibly tough cybersecurity measures, like end-to-end encryption and constant security audits, to protect your data from hackers. Their digital defenses are often far more sophisticated than what a typical business can maintain internally.
Finally, cloud platforms give you tight control over who sees what. You can grant specific permissions to different employees, so only authorized people can view footage or manage the system. Every action is logged, which creates a perfect audit trail and keeps your sensitive information on a need-to-know basis.
Ready to implement a security solution that’s built for your business needs? The expert team at Clouddle Inc specializes in designing and installing integrated security, Wi-Fi, and cloud systems with 24/7 support and zero down payment options. Discover how we can protect your assets and streamline your operations today.


