Network security is a top priority for businesses of all sizes. At Clouddle, we understand the critical role that network security audit tools play in safeguarding your digital assets.
In this post, we’ll explore the top network security audit tools that can help protect your business from cyber threats and vulnerabilities.
Top 5 Network Security Audit Tools
Network security audit tools play a vital role in protecting businesses from cyber threats. Let’s explore five powerful tools that stand out in the field.

Nmap: The Network Scanning Powerhouse
Nmap (Network Mapper) is an open-source tool that has become essential for network administrators and security professionals. It excels at network discovery and security auditing. Nmap sends a series of TCP and UDP packets to the remote host for remote OS detection using TCP/IP stack fingerprinting. Its flexibility allows for both simple and complex scans, making it suitable for businesses of all sizes.
Wireshark: Microscopic Network Traffic Analysis
Wireshark is a robust network protocol analyzer that reveals what’s happening on your network at a granular level. It captures and allows interactive browsing of traffic running on a computer network, providing detailed insights into packet data. Wireshark proves invaluable for identifying unusual traffic patterns (which could indicate a security breach) and troubleshooting network issues.
Metasploit: Real-World Attack Simulation
Metasploit is a penetration testing framework that simulates real-world attacks on your network. It identifies vulnerabilities that malicious actors might exploit. This tool tests your network’s defenses and ensures that your security measures effectively combat known exploit techniques. (Use Metasploit responsibly and only on networks you have permission to test.)
OpenVAS: Comprehensive Vulnerability Scanning
OpenVAS (Open Vulnerability Assessment System) offers full-featured vulnerability scanning. It’s particularly useful for businesses that need to perform regular security audits. OpenVAS scans for thousands of known vulnerabilities and provides detailed reports on potential security issues. Its integration capabilities with other security tools make it a versatile choice for businesses looking to build a comprehensive security stack.
Nessus: User-Friendly Vulnerability Assessment
Nessus is a popular commercial vulnerability assessment tool known for its user-friendly interface and comprehensive scanning capabilities. It identifies vulnerabilities, configuration issues, and even malware that may have slipped past other defenses. Nessus helps organizations improve their remediation efficiency and effectiveness with its Vulnerability Priority Rating (VPR).
These tools bring unique strengths to the table. The key is to choose the right combination that fits your business needs and integrates well with your existing security infrastructure. While tools are essential, they must be paired with solid security practices and regular audits to truly protect your network.
Now that we’ve explored the top network security audit tools, let’s examine the key features you should look for when selecting the right tool for your business.
Essential Features of Network Security Audit Tools
When you select a network security audit tool, certain features can significantly enhance its effectiveness. Let’s explore the must-have features that set top-tier network security audit tools apart.
Advanced Scanning Capabilities
The backbone of any robust network security audit tool is its scanning prowess. You should look for tools that offer both broad and deep scanning options. For instance, Nessus (which we mentioned earlier) can scan over 47,000 CVEs and more than 450 third-party applications. This level of comprehensive scanning ensures that no vulnerability goes undetected.
Real-Time Threat Detection
In today’s fast-paced threat landscape, real-time monitoring is important due to the enhanced and complex network systems in organizations and associated cyber threats. Tools like AlienVault’s USM Anywhere provide continuous monitoring and can detect threats as they happen. A study shows that organizations that centralize their logs have a 30% higher chance of detecting breaches.
Customizable Reporting
Every business has unique reporting needs. The best audit tools offer customizable reports that you can tailor to different stakeholders. For example, Qualys offers over 40 report templates and allows for the creation of custom reports. This flexibility ensures that everyone (from IT staff to C-level executives) can get the information they need in a format they understand.
Seamless Integration
No security tool should operate in isolation. You should look for tools that integrate well with your existing security infrastructure. Many businesses use an average of 45 cybersecurity-related tools (according to IBM). Tools that can seamlessly share data and insights across your security ecosystem amplify their effectiveness and provide a more holistic view of your network‘s security status.

Intuitive User Interface
While powerful features are important, they’re only as good as their usability. A user-friendly interface can significantly reduce the learning curve and improve adoption rates among your team. Tools like Rapid7’s InsightVM offer intuitive dashboards that make complex security data easily digestible, even for non-technical users.
These features form the foundation of effective network security audit tools. As you evaluate different options, consider how each tool measures up in these key areas. The right combination of features will not only uncover vulnerabilities but also provide actionable insights to improve your overall security posture. Next, let’s examine some best practices for conducting network security audits to maximize the effectiveness of these tools.
How to Conduct Effective Network Security Audits
Network security audits are not a one-time event but an ongoing process that requires careful planning and execution. Here’s how to make your audits count.
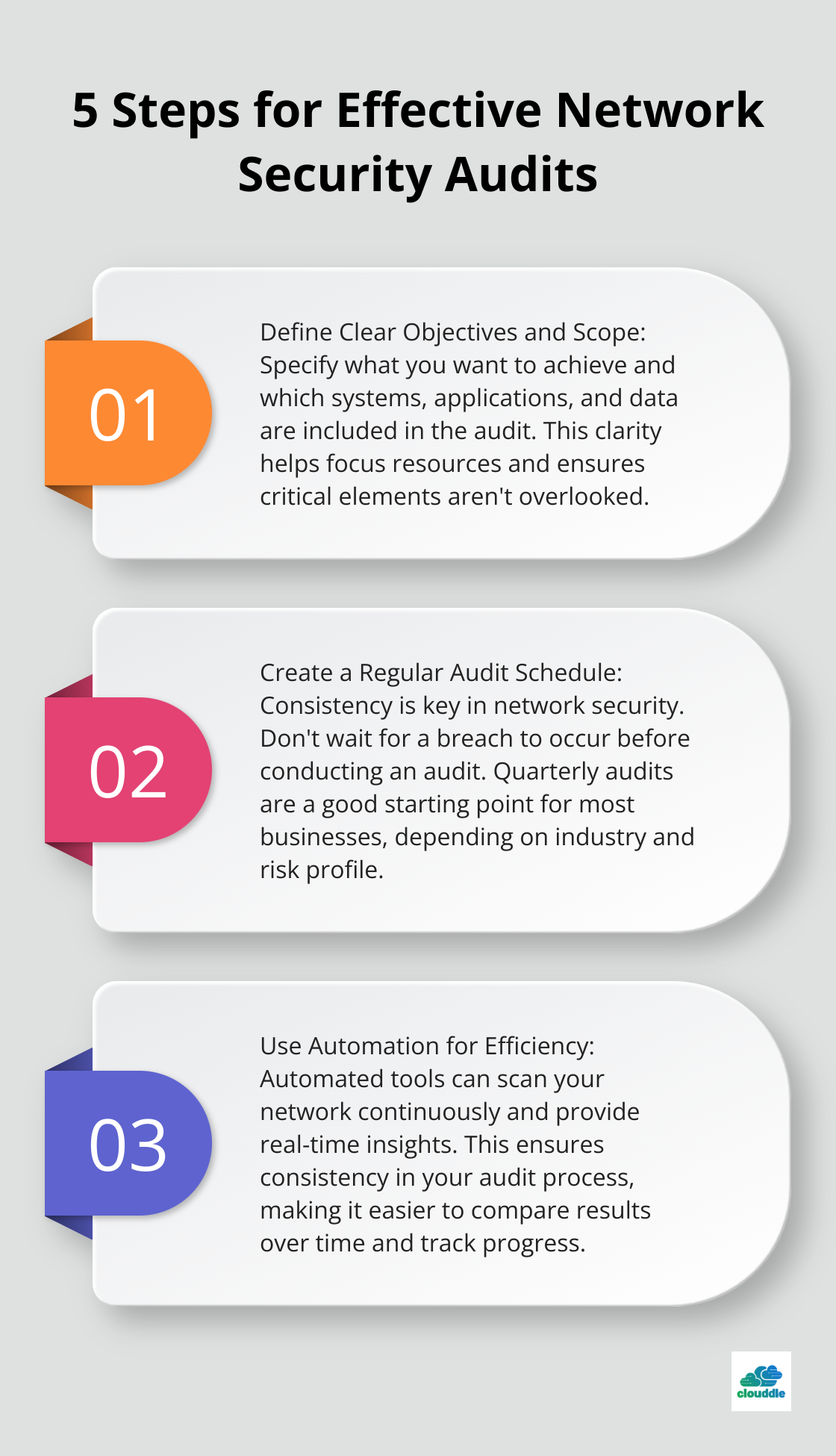
Define Clear Objectives and Scope
Before you start an audit, define what you want to achieve. Are you looking to identify vulnerabilities in a specific system, or do you need a comprehensive review of your entire network? Specify which systems, applications, and data are included in the audit. This clarity helps focus resources and ensures you don’t overlook critical elements.
Create a Regular Audit Schedule
Consistency is key in network security. Don’t wait for a breach to occur before you conduct an audit. The frequency of audits depends on your industry and risk profile, but quarterly audits are a good starting point for most businesses.
Use Automation for Efficiency
Manual audits take time and are prone to human error. Automated tools can scan your network continuously and provide real-time insights. Automation also ensures consistency in your audit process, which makes it easier to compare results over time and track progress.
Involve Key Stakeholders
Include representatives from various departments in your audit process. This approach ensures you consider different perspectives and address security concerns across the organization. IT teams, management, and end-users all have unique insights that can contribute to a more comprehensive audit.
Document and Analyze Findings
Thorough documentation of audit results is essential. Create detailed reports that outline discovered vulnerabilities, potential risks, and recommended actions. Analyze these findings to identify patterns or recurring issues. This analysis will help you prioritize your security efforts and allocate resources effectively.
Final Thoughts
Network security audit tools provide essential protection for businesses in today’s digital landscape. These tools offer robust defense against vulnerabilities and cyber threats, allowing organizations to create comprehensive security strategies. Regular network security audits give crucial insights into network health, identify potential weaknesses, and ensure compliance with industry standards.
Businesses must prioritize network security to create a strong defense against cyber threats. This approach safeguards valuable data and maintains customer trust. Network security is not just a technical necessity-it’s a business imperative in the digital age.
We at Clouddle understand the critical role of robust network security in business operations. Our managed IT and security services help businesses navigate the complex world of cybersecurity (ensuring protected networks and smooth operations). Contact us today to learn how we can enhance your network security posture.