Enterprise Mobility Management (EMM) is a comprehensive game plan for securing and managing all the smartphones, tablets, and laptops your team uses for work. Think of it as an air traffic control system for your company's mobile devices. It ensures every single device, whether it's owned by the company or the employee, operates safely within your network's airspace.
What Enterprise Mobility Management Really Means

At its heart, EMM isn't just another piece of software. It’s a fundamental framework that helps businesses get a handle on the explosion of mobile devices connecting to their sensitive data. As more companies adopt flexible remote work models, having a solid EMM strategy becomes non-negotiable for maintaining security and control.
But this isn't about just locking down devices. A good EMM strategy actually gives employees the tools they need to be productive from anywhere. At the same time, it provides IT admins the oversight required to protect critical company information. The market growth alone tells the story of its importance; valued at USD 19.05 billion today, the global EMM market is projected to hit USD 69.12 billion by 2030.
Finding The Balance Between Productivity and Security
The main goal of any EMM system is to strike that perfect balance between user freedom and corporate security. It pulls this off by giving IT a single, unified console to manage a whole zoo of different devices and operating systems.
This centralized control helps IT teams solve some of the most persistent headaches that come with a mobile workforce.
Common Mobility Problems and EMM Solutions
This table shows a few common business problems and how a proper EMM strategy provides a direct solution.
| Common Business Problem | How EMM Solves It |
|---|---|
| Lost or stolen devices containing sensitive company data. | Enables IT to remotely locate, lock, or wipe the device to prevent data breaches. |
| Inconsistent security across different device types and operating systems (iOS, Android, Windows). | Applies a universal set of security policies (like password rules and data encryption) across the entire fleet from a single dashboard. |
| Employees using unsecured personal apps for work, creating "shadow IT" vulnerabilities. | Creates a secure, managed corporate app store and separates business apps and data from personal ones, especially in BYOD scenarios. |
| Onboarding a new employee with a work-ready device is slow and requires manual setup. | Automates device enrollment and configuration. New devices can be shipped directly to employees and set up automatically right out of the box. |
| Ensuring devices are compliant with industry regulations like GDPR or HIPAA. | Monitors devices for compliance in real-time and can automatically block access or alert IT if a device falls out of compliance. |
Ultimately, an EMM platform gives you a single source of truth for your entire mobile fleet, ensuring everyone stays secure and compliant without getting in the way of their work.
This approach fits hand-in-glove with modern security models. In fact, you can learn more about how to implement Zero Trust security in our other guide. EMM is a crucial piece of that puzzle, as it helps verify every single device before granting it access to your network—nothing is trusted by default.
Breaking Down the Core Components of EMM
A solid enterprise mobility management strategy isn't just one thing; it's a combination of key technologies working in concert. You can think of it less like a single tool and more like a full toolkit, with each piece designed for a specific job.
Understanding these individual components is the first step. They build on each other to create a complete security and management framework for every company-connected device, from the hardware itself to the apps and the data flowing through them.
This diagram shows how these layers fit together to form a unified system.
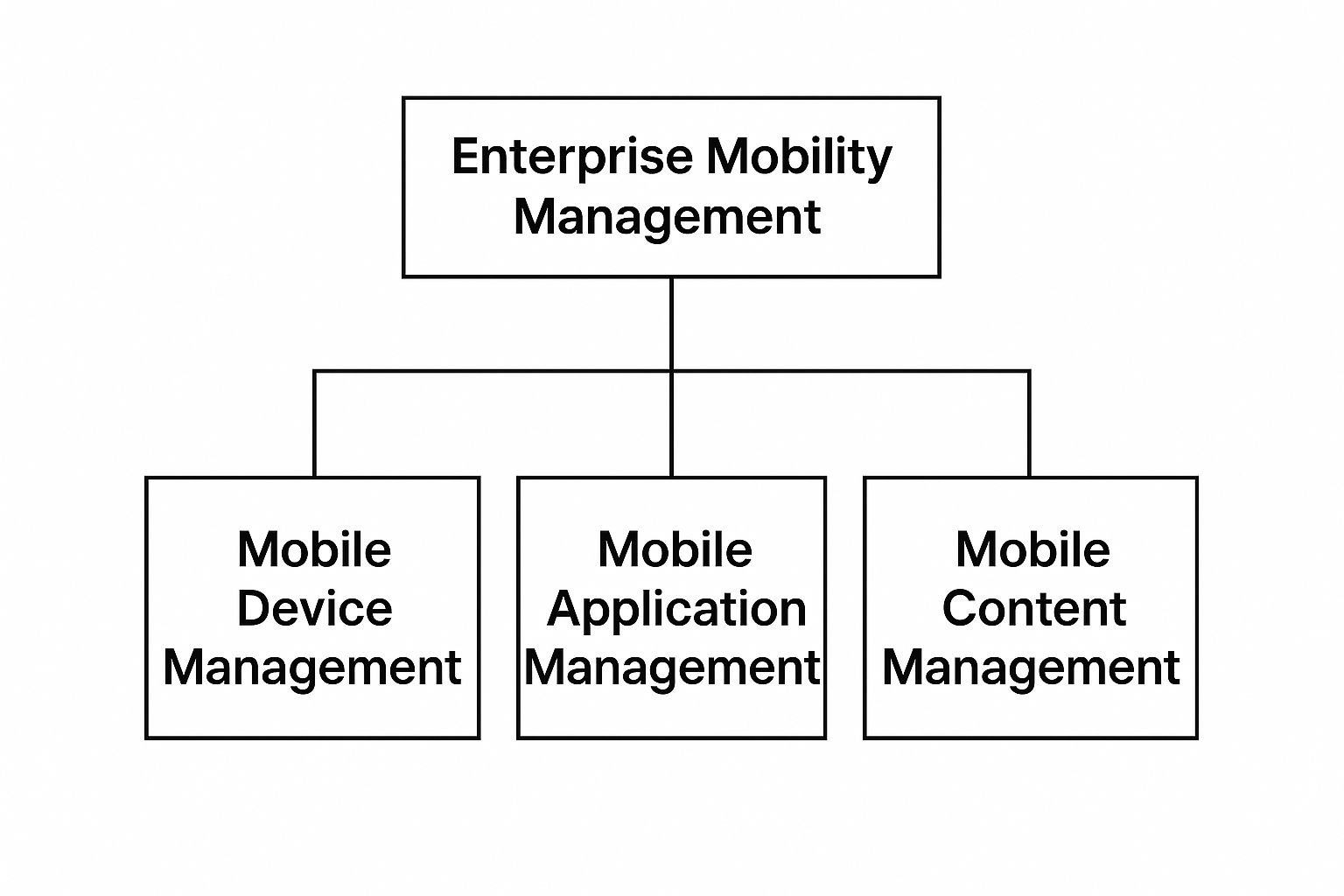
As you can see, each part supports the others to give your IT team comprehensive oversight and control.
Device and Application Management
Let's start with the two foundational pillars: Mobile Device Management (MDM) and Mobile Application Management (MAM).
Think of MDM as the "rulebook" for the physical device. It gives your IT admins the power to enforce security policies directly on a phone or tablet. This means they can set password requirements, enforce encryption, and, most importantly, remotely wipe a device if it’s lost or stolen. Good MDM is a non-negotiable part of any wider strategy, and you can see how it fits into broader IT asset management best practices.
MAM, on the other hand, acts like an "app store bouncer." Its focus is much narrower—it only controls corporate applications and the sensitive data inside them. This is what allows IT to create a secure, separate container for work apps on an employee's personal phone, all without ever touching their private photos or messages. Protecting that data is paramount, which requires a deep understanding of essential mobile app security best practices.
Content and Access Control
Next up is Mobile Content Management (MCM), which you can imagine as a "secure digital briefcase." MCM makes sure that company documents, files, and media are only accessed and shared through approved, secure channels. It’s all about preventing data leaks.
Finally, Identity and Access Management (IAM) serves as the "digital ID card." It’s the gatekeeper, verifying that only authorized users are allowed to access specific applications and corporate data.
By integrating these components, EMM ensures that the right person, using a secure device and approved apps, is accessing the right corporate information—and nothing more. This layered security is vital for any modern business.
It’s no surprise that the market overwhelmingly prefers cloud-based EMM solutions. They currently hold between 56-78% of the market share because they are far more scalable and cost-effective than old-school on-premise setups.
While large enterprises make up the bulk of the market revenue (52-59%), we're seeing a huge uptick in small and medium-sized businesses adopting EMM as remote and mobile work becomes the norm.
The Business Case for EMM Implementation

It’s one thing to understand the technical side of enterprise mobility management, but it's another to see how it truly impacts the business. Putting an EMM solution in place isn't just another line item for the IT budget; it's a strategic investment that pays dividends by solving some of the biggest headaches that come with a mobile workforce.
The most obvious win is a huge step up in data security. Think about it: a company laptop left in a taxi or a work phone stolen from a coffee shop. With EMM, IT can remotely lock or completely wipe that device in minutes. What could have been a catastrophic data breach becomes a simple, manageable incident, keeping your trade secrets and customer data safe.
Beyond crisis management, an EMM solution is your best friend when it comes to navigating the tangled mess of industry regulations.
Simplifying Compliance and Boosting Productivity
If you're in a heavily regulated field like healthcare or finance, EMM is practically non-negotiable. It gives you the power to enforce the strict data protection rules required by standards like GDPR and HIPAA. This means ensuring every phone and tablet that touches sensitive data has the right encryption and access controls, which makes audits smoother and helps you sidestep massive fines.
On top of that, EMM is a massive productivity booster. It gives your team secure and easy access to the exact apps and files they need, wherever they happen to be working. This cuts down on the daily friction, letting people get more done, more quickly.
A solid EMM strategy flips the script on mobile devices. They stop being a potential security risk and become a powerful tool that drives productivity and directly impacts your bottom line.
This isn't just a niche idea; the market growth tells the story. In the United States alone, the EMM market is on track to hit USD 14.0 billion by 2025. This explosive growth is driven by the very real needs of modern business: tight cybersecurity, regulatory pressure, and the unstoppable rise of Bring Your Own Device (BYOD) policies.
For a deeper dive into market trends, you can explore the full research about enterprise mobility management.
How EMM Works in the Real World
It's one thing to talk about EMM in theory, but where does the rubber meet the road? The real power of EMM isn't just in its features, but in how it’s tailored to solve very specific problems across different industries. Let's look at a few examples of how it works on the ground.
Think about the fast-paced environment of a hospital. Doctors and nurses are constantly on the move, using tablets to pull up patient charts, check test results, and update records. An EMM system is the invisible guardian here, making sure every one of those devices is fully encrypted and requires a strong password.
If a tablet is ever lost or stolen, the IT department can remotely wipe all its data in seconds. This isn't just a technical convenience; it's what prevents a massive data breach and a potential HIPAA violation, allowing medical staff to focus on patient care with confidence.
EMM in Retail and Corporate Environments
Now, picture a nationwide retail chain. Each store has a mix of point-of-sale (POS) systems, handheld inventory scanners, and mobile payment terminals. With EMM, a central IT team can lock every device into a "kiosk mode," so it can only run the specific app it needs. This stops employees from browsing the web or accidentally installing unapproved software.
They can also push out critical software updates to thousands of devices across hundreds of stores simultaneously, often overnight. This ensures that every location is running the latest, most secure software for processing customer payments.
This kind of control is also essential in the corporate world, especially as more companies adopt "Bring Your Own Device" (BYOD) policies. Your sales team, for example, probably uses their personal smartphones for everything from checking email to accessing the company's CRM.
An EMM solution addresses this by creating a secure, encrypted "container" on an employee's personal phone. This digital partition keeps all work-related apps and data completely separate from their personal photos, messages, and apps. The company can manage its container without ever seeing or touching the employee's private information.
This approach strikes the perfect balance, giving the company the security it needs while respecting employee privacy.
Of course, for any of these scenarios to work, you need a rock-solid network. Consistent, secure connectivity is the backbone that allows EMM policies to function. For any business juggling a fleet of mobile devices, having a professionally managed network is a game-changer. You can learn more about how managed Wi-Fi services create the reliable foundation needed for a smart mobility strategy.
A Practical Guide to EMM Implementation

Getting an enterprise mobility management strategy off the ground is about much more than just installing new software. Think of it as a strategic project that demands careful planning to succeed. A good rollout is like a roadmap—it helps you anticipate bumps in the road and ensures everyone in the organization can adopt the new system smoothly. It really has to be a team effort, bringing your IT, security, and leadership teams together.
The very first step? Hammering out clear and detailed mobility policies. Before you even think about looking at different EMM vendors, you need to establish the rules for how mobile devices will be used. This means creating a formal Bring Your Own Device (BYOD) policy that clearly outlines what's expected for security, privacy, and acceptable use when employees access company data on their personal phones and tablets.
This policy becomes your north star, guiding every decision you make and defining the level of control your EMM solution needs to have.
Building Your Implementation Plan
Once you have a solid policy, you can get into the more technical side of things. A successful EMM deployment relies on a step-by-step approach that puts stability and employee buy-in first. If you rush it, you’re just asking for pushback from employees and technical headaches that were completely avoidable.
Here are the key stages you'll want to follow:
- Choose the Right EMM Solution: Let's be clear: not all EMM platforms are the same. You need to evaluate vendors based on what your policies demand, the security features you can't live without, and how well it can grow with your company. Ask yourself: does this solution actually work well with the specific devices and operating systems our people use every day?
- Plan a Phased Rollout: Whatever you do, don't try a "big bang" launch where everyone gets it at once. Start small. A pilot group, usually from your IT department or another tech-friendly team, is perfect for working out the kinks. This gives you a chance to get real feedback and tweak the settings before you push it out to the entire company.
- Prioritize Communication and Training: People need to know what's happening and why. Be transparent about the reasons for the new system, highlighting the security improvements and how it helps them work more flexibly. Offer simple training sessions and easy-to-read guides to show employees how to enroll their devices and what changes to expect.
An EMM implementation isn’t just an IT project; it’s a change management initiative. Getting your employees on board with clear communication is just as crucial as getting the technical configuration right.
At the end of the day, the goal is to make security feel invisible, not like a burden. A well-planned implementation turns your EMM solution into a tool that helps your team get their work done securely from anywhere, rather than a frustrating roadblock. This approach causes less disruption and truly sets you up for success down the line.
A Few Common Questions About EMM
Even after getting the basics down, you might still have a few questions about how enterprise mobility management would actually work for your business. Let's clear up some of the most common ones that pop up.
What’s the Real Difference Between EMM and MDM?
This is a big one, and it’s easy to get them mixed up. The simplest way to think about it is that Mobile Device Management (MDM) is a core part of EMM, but it isn't the whole story. MDM is all about controlling the physical device itself—things like enforcing passcodes, encrypting the hardware, or remotely wiping the entire phone if it gets lost.
Enterprise mobility management (EMM) is the full package. It takes MDM and builds on it by adding more focused layers of control, like Mobile Application Management (MAM) to secure just the work apps, and Mobile Content Management (MCM) to protect sensitive files and documents.
If MDM is the security guard for the building, EMM is the entire security system—guards, cameras, and keycard access for specific rooms included. It gives you a much more complete and flexible way to handle security, especially when personal devices are involved.
How Does EMM Actually Work with a BYOD Policy?
EMM is a perfect fit for a "Bring Your Own Device" (BYOD) world. Its secret weapon is a technology called containerization. This feature creates a secure, encrypted "work bubble" on an employee's personal smartphone or tablet.
Think of it as a digital briefcase on their phone. All the company apps and data live inside this container, completely walled off from their personal photos, texts, and apps. Your IT team has full control over what happens inside the work container—including the ability to wipe only that corporate data—without ever touching the employee’s personal stuff. This separation is key to respecting employee privacy while keeping company data locked down.
Is EMM Just for Big Companies?
Not anymore. It’s true that EMM used to be a tool mainly for huge corporations with deep pockets. But the game has completely changed. With remote and hybrid work now the norm, businesses of every size are dealing with the same mobile security challenges.
Thankfully, many EMM providers now offer cloud-based solutions that are affordable, scalable, and easy to implement. This puts top-tier mobile security within reach for small and medium-sized businesses (SMBs), even if you don't have a big IT team. Good security is a necessity for everyone now, not a luxury for the Fortune 500.
A great EMM strategy needs a reliable and secure network to stand on. Clouddle Inc specializes in managed technology solutions that create that stable foundation, helping you protect your mobile devices and empower your team. Find out more about our integrated security and networking services at https://www.clouddle.com.


