Think of your company's network as its central nervous system. It's the digital highway where every piece of critical information—from emails and customer data to financial reports—travels. But what happens when that highway gets congested, or worse, when a malicious driver tries to cause a crash? This is where network traffic analysis (NTA) comes in.
In simple terms, NTA is the practice of capturing, inspecting, and analyzing the data flowing across your network. It’s like having an intelligent traffic control system for your digital infrastructure, one that doesn't just watch cars go by but understands where they're coming from, where they're going, and whether they pose a risk.
Your Digital Highway: Why Traffic Analysis Matters

Without a clear view of your network traffic, you're essentially driving blind. Slowdowns, outages, and security breaches can pop up out of nowhere, causing chaos and bringing business to a halt. NTA provides that crucial visibility.
The real power of NTA isn’t just in watching data packets fly by; it’s about understanding the patterns and establishing a baseline for what "normal" looks like. Once that baseline is set, any deviation—like an employee suddenly uploading terabytes of data to an unknown server at 3 AM—is instantly flagged. It’s the difference between guessing what’s causing a slowdown and knowing exactly which application is hogging all the bandwidth.
Core Functions of Network Traffic Analysis
So, what does network traffic analysis actually do for you day-to-day? It performs several essential jobs that are fundamental to keeping a modern business running smoothly and securely.
Here’s a quick breakdown of what NTA tools are constantly doing behind the scenes.
| Function | Objective | Real-World Analogy |
|---|---|---|
| Security Threat Detection | Identify and flag malicious or anomalous activity before it causes a breach. | A security guard at a building entrance who spots someone suspicious trying to sneak in. |
| Performance Troubleshooting | Pinpoint the exact source of network slowdowns or connectivity issues. | A traffic helicopter reporter identifying the specific accident causing a major highway jam. |
| Capacity Planning | Provide hard data to justify and plan for necessary infrastructure upgrades. | A city planner using traffic count data to decide where to build a new road or add more lanes. |
The importance of these functions is not going unnoticed. The global market for network traffic analytics is on a massive growth trajectory, expected to surge from $6.8 billion in 2025 to $27.7 billion by 2035. That's a compound annual growth rate of 15.1%, a clear sign that businesses are waking up to the need for deeper network insight. You can explore more data on this trend in a market report from Future Market Insights.
By monitoring the flow of data, network traffic analysis acts as a digital detective. It uncovers hidden threats and performance issues that traditional tools might miss, providing the deep insight needed to keep your operations secure and efficient.
Ultimately, NTA shifts your IT strategy from being reactive to proactive. Instead of scrambling to fix things after a system fails or a breach occurs, you can spot the warning signs and neutralize threats before they escalate. It’s about managing your digital highway with precision, ensuring every data packet arrives at its destination safely and on time.
How Network Traffic Analysis Actually Works
To really get what network traffic analysis is all about, you have to look under the hood. It’s not just a single, one-off action; it's a sophisticated process that turns the chaotic mess of raw network data into clear, usable insights. Think of it as a journey, moving from basic data collection to some seriously smart analysis.
Before we get into the nuts and bolts, it helps to have a good handle on networking basics. If you need a refresher on how data gets from point A to point B, the guide on Computer Networking Explained is a great place to start. A little background knowledge makes the next steps much easier to follow.
The First Step: Packet Capture
The very foundation of network traffic analysis is packet capture. Imagine your network traffic is like a river of digital mail. Every piece of that mail is a "packet"—a tiny bundle containing a bit of data, a destination address, and a return address.
Packet capture is the act of grabbing a copy of these individual packets as they fly across your network. Special tools, often called packet sniffers, do this without slowing anything down. It’s like a postal inspector examining each package to see what’s inside and where it’s going, giving you the most detailed view possible.
This process, sometimes called deep packet inspection (DPI), lets an NTA system see not just where data is headed, but what kind of data it is—is it a simple website request, a video call, or maybe a malicious command in disguise?
This level of detail is crucial for finding advanced threats. The only catch is that capturing and storing every single packet on a busy network can eat up a lot of resources. For a high-level view, it's often overkill, which brings us to the next stage.
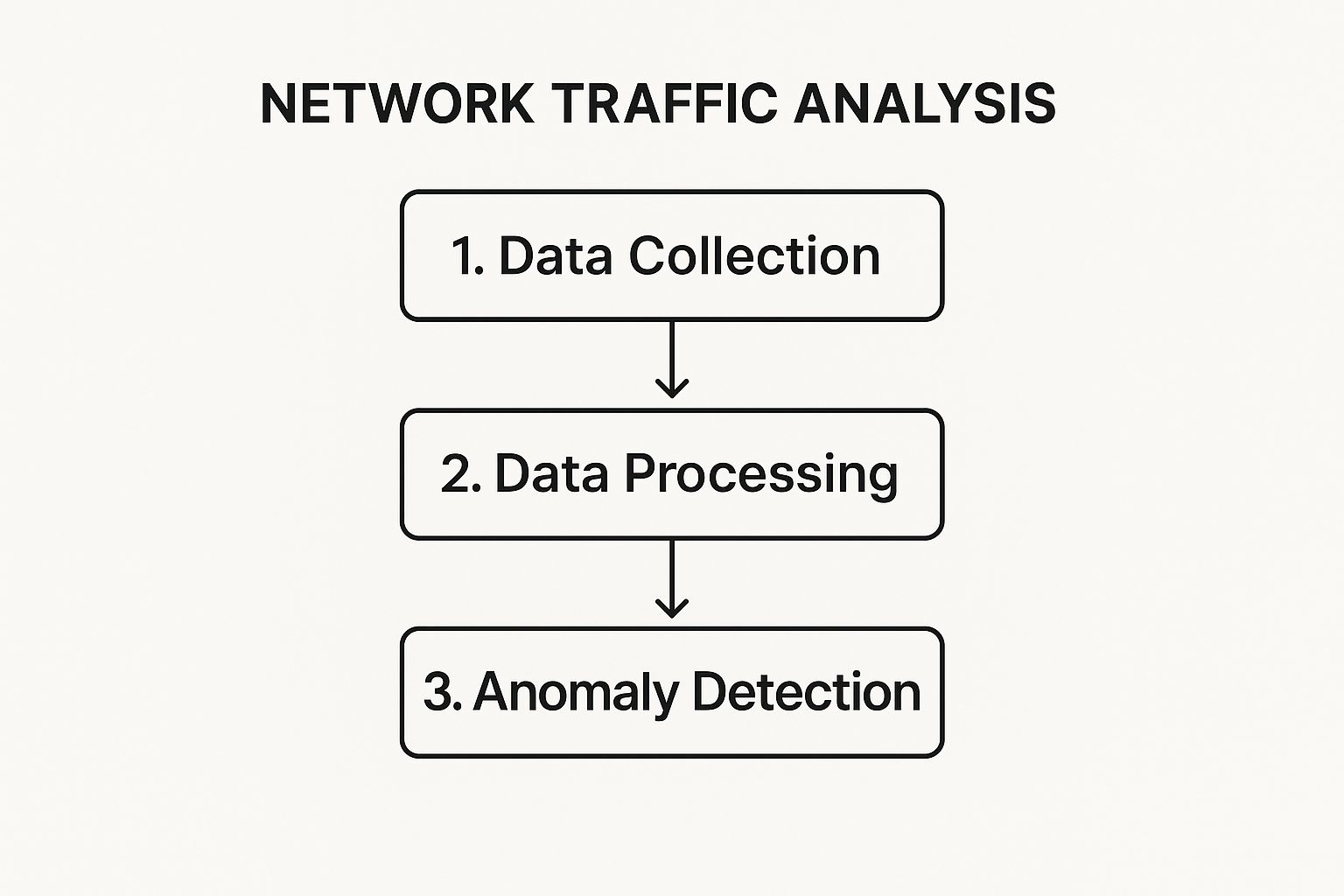
The Second Step: Flow Analysis
If packet capture is like reading every single letter, flow analysis is like tracking the total mail volume between two post offices. It doesn’t open every piece of mail. Instead, it gathers metadata to build a big-picture summary of the conversations happening on your network.
A "flow" is just a record of a conversation between two endpoints. Flow analysis pulls out key details from these conversations:
- Source and Destination: Who is talking to whom?
- Volume of Data: How much information was sent back and forth?
- Duration: How long did they talk?
- Protocols Used: What "language" did they use (e.g., web traffic, email)?
This approach is way more efficient than full packet capture and gives you a fantastic map of your network's activity. It’s perfect for spotting broad trends, like a sudden, massive data transfer to an unusual location—a classic red flag for a data breach. To see how this fits into the bigger picture, you can learn more about the broader discipline of what is network monitoring.
The Final Step: Intelligent Baselining
Here’s where modern NTA gets really powerful. It uses machine learning to create a behavioral baseline. Essentially, the system watches your network day in and day out, learning what "normal" activity looks like for your specific business.
This baseline understands all your regular patterns—daily backups, peak business hours, and which applications talk to each other. Once it has this profile of normalcy locked down, the NTA tool can spot anything out of the ordinary in an instant. For example, if a computer in your accounting department, which usually only touches financial software, suddenly tries to connect to a developer's server, the system flags it as suspicious.
This intelligent approach has become essential. With so many people working from home, the old idea of a secure network perimeter is gone. As of 2021, the global IT ecosystem wasn't just the 7,500 physical data centers; it also included countless home networks. This creates blind spots that intelligent baselining is designed to solve. When you consider that 12.7% of employees are fully remote and another 28.2% are hybrid, you can see just how big that challenge is.
Uncovering Threats Hiding in Your Network
While network traffic analysis is a fantastic tool for smoothing out performance issues, its most vital role is in cybersecurity. Think of it as a digital detective patrolling the inside of your network, on the lookout for threats that traditional tools like firewalls and antivirus software can miss. Those defenses are like a high wall around your business, but what happens when a threat is already inside?
This is where NTA really proves its worth. It works from the assumption that a breach may have already happened—a mindset known as "assume breach." Instead of just guarding the gates, it actively patrols the hallways, watching for any strange behavior that points to an active threat. This shift from pure prevention to rapid detection is absolutely critical for limiting the damage an attack can cause.
Spotting Dangers That Slip Past Your Defenses
Your traditional defenses are essential, but they aren't perfect. Determined attackers can often find a way around them. Once they’re in, their activity creates network traffic that, to a trained eye or an intelligent system, looks completely out of place.
NTA is built to catch these subtle clues. It doesn't just see two computers talking; it understands the context of their conversation. Tools like Wireshark, a popular network protocol analyzer, are indispensable for this kind of deep-dive packet inspection, giving you a granular view of everything happening on your network.
Here are a few real-world examples of what NTA can uncover:
-
Malware Phoning Home: When malware infects a device, it often tries to contact a command-and-control (C2) server to get instructions. NTA can spot these unusual, often encrypted, communication patterns to unknown external servers, even if the malware itself is completely hidden.
-
Insider Data Theft: Imagine a disgruntled employee trying to walk away with sensitive company data. NTA can flag an unusually large data transfer from their workstation to a personal cloud drive or an external IP address, especially if it’s happening at 2 a.m.
-
Early Ransomware Warnings: Before ransomware starts encrypting files, it typically scans the network to find the most valuable data. NTA can detect this widespread scanning behavior as an anomaly, giving your security team a crucial heads-up to intervene before the real damage begins.
By focusing on behavioral anomalies instead of just known threat signatures, network traffic analysis can detect zero-day exploits and brand-new attack methods that have never been seen before. It answers the question, "Is anything happening on my network that shouldn't be?"
A Critical Layer in Modern Security
The world of cybersecurity is always in flux, with hybrid cloud setups and zero-trust security models adding new layers of complexity. It's getting harder for organizations to keep up. In this environment, managed detection and response (MDR) services, which lean heavily on NTA, are growing at a 14.5% compound annual growth rate. This growth highlights a key shortage of expert analysts needed to do this work in-house.
This trend underscores a critical point: NTA doesn't replace your firewall or antivirus. It’s a complementary and necessary layer that gives you visibility inside your network. Your firewall might block a known malicious IP address, but NTA can spot a compromised—but legitimate—device communicating in a way it never has before.
By learning the normal rhythm of your network, NTA provides the context needed to identify real threats from all the noise. For anyone looking to build this capability, our guide on https://clouddle.com/blog/how-to-analyze-network-traffic-for-enhanced-security/ offers practical steps and strategies. It all comes down to having a security posture that is both strong at the borders and vigilant within, ensuring threats have nowhere left to hide.
Boosting Performance Beyond Security
While most people think of network traffic analysis as a security tool, that’s only half the story. The truth is, it's just as powerful for optimizing network performance, ensuring everything runs smoothly, and making smart infrastructure decisions. For any IT team, it’s the difference between fumbling in the dark and working with the lights on.
Think of it like this: your network is a highway system. When a major traffic jam happens (your app slows down), you could just guess where the problem is. Or, you could use traffic cameras to see the entire system, find the exact accident causing the backup, and clear it quickly. Network traffic analysis gives you those cameras.
From Guesswork to Data-Driven Troubleshooting
We’ve all been there—a critical application slows to a crawl, and the finger-pointing begins. Is it the internal network? The internet provider? Is the app’s server just having a bad day?
Without real data, IT teams are stuck chasing ghosts, wasting hours while productivity plummets. Network traffic analysis cuts right through the noise. By mapping out the data flows, it can tell you exactly where the bottleneck is. Maybe a forgotten background update is suddenly hogging all the bandwidth, leaving your most important tools starved for resources.
Network traffic analysis provides concrete evidence to answer the "why is it slow?" question. It pinpoints the root cause, whether it's a misconfigured device, a bandwidth-hungry user, or an underperforming external service, allowing for a swift and targeted resolution.
This ability to isolate problems is a game-changer. It means less downtime, happier users, and a far more reliable digital foundation for your business.
Optimizing Resources and Planning for Growth
Beyond just fixing what's broken, network traffic analysis is brilliant for proactive management. It gives you a crystal-clear picture of how your bandwidth is actually being used day-to-day. This insight helps you spot trends, allocate resources intelligently, and plan for future needs.
It helps you answer crucial operational questions with confidence:
- Who are the top talkers? NTA shows you exactly which users, devices, or apps are the biggest bandwidth consumers, helping you enforce fair-use policies.
- When are our peak hours? Understanding your traffic patterns lets you schedule heavy tasks like data backups for quiet, off-peak times to avoid disrupting the workday.
- Do we need more bandwidth? Instead of guessing, NTA provides the hard data to justify an upgrade, showing exactly when and why your current capacity is hitting its limit.
The same data that helps you spot a threat can also help you find a performance bottleneck. It's all about looking at the same information through two different, equally important lenses.
Security vs Performance: How NTA Solves Both
The table below breaks down how analyzing the same network events can solve both security and performance challenges.
| Challenge | Security Application | Performance Application |
|---|---|---|
| Unusual Traffic Spikes | Identifies potential data exfiltration or a DDoS attack. | Pinpoints a "bandwidth hog" application causing slowdowns for others. |
| New Traffic Patterns | Detects malware communicating with a command-and-control server. | Reveals a new, unauthorized application straining network resources. |
| High Volume of Connections | Spots a compromised device scanning the network for vulnerabilities. | Identifies a misconfigured server overwhelming a critical database. |
Ultimately, using network traffic analysis for performance management ensures your digital infrastructure is an asset that drives your business forward, not a problem that holds it back.
Getting Started with Network Traffic Analysis
Putting network traffic analysis to work is more than just installing a new piece of software. It’s a strategic process that turns a flood of raw data into real, actionable insights. The first thing you need to do is get crystal clear on your goals. What are you trying to achieve?
Are you on the hunt for hidden security threats lurking in your network? Or are you trying to pinpoint those frustrating performance bottlenecks that slow everything down? Maybe it's a bit of both.
Your answer here sets the stage for everything that follows. If security is your main driver, you'll likely focus on monitoring data moving in and out of your network. But if performance is the name of the game, you’ll probably want to zoom in on the internal traffic between your most important servers and applications.
Finding Your "Normal"
With your goals in hand, the next step is to figure out which parts of your network need the most attention. You don't have to watch every single byte of data with the same level of scrutiny. Start with your high-value assets.
Think about servers that hold sensitive customer information, the pathways for your mission-critical applications, and the main entry and exit points of your network. These are your crown jewels.
Once you’ve identified these critical zones, the real work begins: establishing a baseline of normal traffic patterns. This means letting your analysis tool watch and learn the unique rhythm of your network over time, usually for a few weeks.
Think of this baseline as your network's fingerprint. It's the definitive picture of what "normal" looks like, allowing the system to instantly flag anything out of the ordinary—like a server that suddenly starts talking to a strange address it has never contacted before.
Without a solid baseline, you'll drown in false alarms. An endless stream of alerts makes it nearly impossible to see the real threats when they appear.
Building a Cohesive Defense
Network traffic analysis truly shines when it’s part of a team. Integrating its insights with your other security tools creates a much smarter, more resilient defense system. The most common and powerful pairing is with a Security Information and Event Management (SIEM) platform.
This connection lets you correlate what's happening on the network with other security events. For example, your NTA tool might spot a suspicious connection from a workstation, while at the same time, your endpoint protection flags a weird process running on that exact machine. A SIEM can connect those dots, escalating it as a high-confidence alert that demands immediate attention.
This layered approach gives you a much fuller picture of what's going on. Of course, a strong defense also requires solid gatekeeping. To learn more about shoring up your network's front door, check out our guide on how to implement network security authentication. When you combine strong authentication with deep traffic visibility, you build a truly formidable barrier.
In the end, a thoughtful implementation—whether you do it yourself or work with a partner—transforms your network from a mysterious black box into an open book. It gives you the clarity you need to keep your operations safe, smooth, and efficient.
Weaving NTA into Your Managed IT Strategy
Knowing what network traffic analysis can do is one thing. Actually putting it to work and managing it around the clock? That’s a whole different beast. For most businesses, the idea of hiring dedicated cybersecurity experts, investing in specialized tools, and running a 24/7 monitoring operation is just too much to take on.
This is exactly where a managed IT services partner changes the game.
Instead of building an entire NTA program from scratch—with all the costs and headaches that come with it—you can simply have it built into your service plan. At Clouddle, we’ve made advanced network traffic analysis a core part of our managed IT and security services. We turn what would be a massive operational burden into a seamless, powerful advantage for your business.
The responsibility shifts from your team to ours. Our experts take care of the constant monitoring, the deep analysis, and the instant alerts, which lets your team focus on what they do best: running your business.
The Proactive Edge of a Managed Solution
A managed NTA service flips your entire approach from reactive to proactive. You’re no longer waiting for a user to complain about a slow application or, worse, for a data breach to make itself known. Our team is already watching the flow of data, hunting for the earliest signs of trouble.
This forward-thinking stance means we can spot and fix potential problems long before they blow up into full-blown crises. It’s like having a team of digital detectives patrolling your network’s every corner, making sure everything is running smoothly and securely, day and night.
Partnering with a managed service provider like Clouddle gives you access to enterprise-grade technology and a deep bench of security talent, but without the enterprise-level price tag. We take complex network data and turn it into clear, actionable insights that protect and sharpen your business operations.
We bridge the gap between understanding NTA and seeing it deliver real results. Our team doesn't just flood you with cryptic alerts. We give you context and clear guidance, explaining what we found, why it matters, and the steps we’re already taking to handle it.
How Clouddle Delivers NTA as a Service
Plugging NTA into a managed service framework is the most effective way to boost both your security and your network performance. Forget about buying, configuring, and maintaining complex hardware and software. You get all the benefits in a ready-to-go solution.
Our approach is built on a few key pillars designed to deliver maximum value with minimal disruption:
-
24/7 Expert Monitoring: Our Security Operations Center (SOC) is staffed by people who live and breathe network analysis. They use top-tier tools from partners like SolarWinds and ManageEngine to watch your traffic for anomalies, threats, and performance hiccups—24/7/365.
-
Actionable Intelligence Reports: We boil down mountains of raw data into simple, clear reports. You’ll see exactly how your bandwidth is being used, which applications are the most resource-hungry, and get straightforward alerts on anything that looks suspicious.
-
Rapid Incident Response: When we spot a credible threat, we don't just send you an email. We take action. Our team follows proven protocols to investigate, contain, and shut down threats, significantly reducing their potential impact on your business.
-
Continuous Optimization: The insights we gather from NTA aren't just for security. We use them to give you ongoing recommendations for making your network faster and more resilient. That might mean reconfiguring a firewall, suggesting a bandwidth upgrade, or updating a security policy to close a loophole.
Ultimately, integrating NTA with a managed service from Clouddle is about gaining peace of mind. It’s the assurance that your digital foundation is not just running, but is secure, resilient, and perfectly tuned to help you grow.
Answering Your Questions About Network Traffic Analysis
Even after diving into the details, you probably have a few practical questions about what network traffic analysis really looks like in action. Let's tackle some of the most common ones to clear things up.
Think of this as the "nuts and bolts" section, designed to bridge the gap between theory and real-world application.
Is Network Traffic Analysis Legal?
Absolutely. When you're analyzing traffic on a network you own or have explicit permission to manage, it's not just legal—it's a fundamental part of responsible IT management and cybersecurity.
The best way to think about it is like a business owner setting up security cameras inside their own store. You're not spying on the public street; you're monitoring your own property to protect your assets, employees, and customers. The same principle applies here. You're monitoring your digital infrastructure to keep it safe and running smoothly.
What Is the Difference Between NTA and a Firewall?
This is a fantastic question because they're both security tools, but they play very different roles on the team. A firewall is your network's gatekeeper. It stands at the border and makes simple "yes" or "no" decisions based on a strict set of rules about who gets in and who stays out.
Network traffic analysis (NTA), on the other hand, is your internal security detail. It operates under the assumption that a threat might have already slipped past the gatekeeper. NTA's job is to watch everything happening inside the network, looking for behavior that just doesn't seem right.
A firewall is the bouncer at the club door checking IDs. NTA is the security team inside, watching the crowd for suspicious activity. You really need both to be secure.
So, while a firewall is all about enforcing access rules, NTA is about detecting subtle anomalies and patterns that could signal a sophisticated attack that a rule-based system would completely miss.
Can NTA See Encrypted Traffic?
This is a tricky one, and the answer is both yes and no. NTA can't break the encryption to read the content of the data—your sensitive information stays scrambled and secure. However, it can still extract a ton of useful information from the "envelope" the data is traveling in.
Even when traffic is encrypted, an NTA tool can analyze critical metadata, such as:
- Who is talking to whom: It knows the source and destination of the communication.
- How much they're talking: It sees the size and frequency of the data packets.
- When they're talking: It can spot communications happening at unusual times.
By piecing together this metadata, NTA can still spot trouble. For instance, it can easily identify a compromised laptop sending small, encrypted packets to a known malicious server in the middle of the night. It doesn't need to know what is being sent to know something is wrong. This powerful technique is often called Encrypted Traffic Analysis (ETA).
Ready to get a clear view of your network without adding more to your team's plate? Clouddle Inc builds network traffic analysis directly into our managed IT services. We provide the 24/7 expert monitoring that keeps your business secure and efficient. Find out how our proactive security approach can protect what you’ve built by visiting https://www.clouddle.com.


