The security landscape has fundamentally shifted. Attackers no longer respect network boundaries, and traditional perimeter defenses have become obsolete.
At Clouddle, we’ve seen firsthand how organizations struggle with outdated security models. Zero trust network security represents a complete departure from this approach-it assumes no user or device is trustworthy by default, regardless of location.
This framework is no longer optional for organizations serious about protecting their assets.
Why Your Current Security Model Is Failing
Legacy Systems Create a False Sense of Protection
The numbers tell a stark story. According to the State of Zero Trust 2025, a growing 27% of companies are using peer-to-peer mesh VPNs, and 34% use cloud-delivered ZTNA platforms, yet organizations still cite security risks as their top frustration with legacy systems. This contradiction reveals a critical gap: companies know their defenses are broken but struggle to move away from them.
Traditional perimeter-based security assumes that threats come from outside your network boundary and that internal traffic is inherently safe. This assumption has collapsed. Cloud adoption, remote work, and distributed systems have eliminated the concept of a clear network edge, yet most organizations haven’t updated their security posture accordingly.
The result is predictable and dangerous. When organizations report security incidents regularly, and employee error accounts for 12% of data breaches, it becomes clear that controlling access at the network perimeter alone is insufficient. Attackers no longer need to breach your firewall; they exploit compromised credentials, phishing attacks, and weak authentication to move laterally within your network undetected.
Performance Degradation Compounds Security Weakness
The performance impact of legacy systems compounds the security problem. Organizations using traditional VPNs report significant operational friction: 34% struggle with remote growth, 32% experience slow connections, and 26% face hindered cross-team collaboration. More telling, employees at companies still using legacy VPNs report that time-to-market for new products is twice as slow as their peers using modern access models.

This isn’t just a convenience issue; it directly affects business outcomes.
Security tools have also fragmented across most organizations. A staggering 92% of companies use more than one tool to manage network security, creating integration gaps, visibility blind spots, and operational complexity that ironically weakens security. When your security stack doesn’t communicate internally, attackers exploit the gaps between systems.
Employee Workarounds Undermine Your Defenses
The State of Zero Trust 2025 also revealed that 83% of employees bypass security measures to stay productive, with 87% of developers admitting to circumventing controls through personal devices or unapproved tools. This behavior isn’t malicious; it reflects a fundamental misalignment between security policies and how modern work actually happens.

Organizations forcing outdated access models onto distributed teams inadvertently push those teams toward riskier workarounds.
Zero Trust Demands Three Concrete Changes
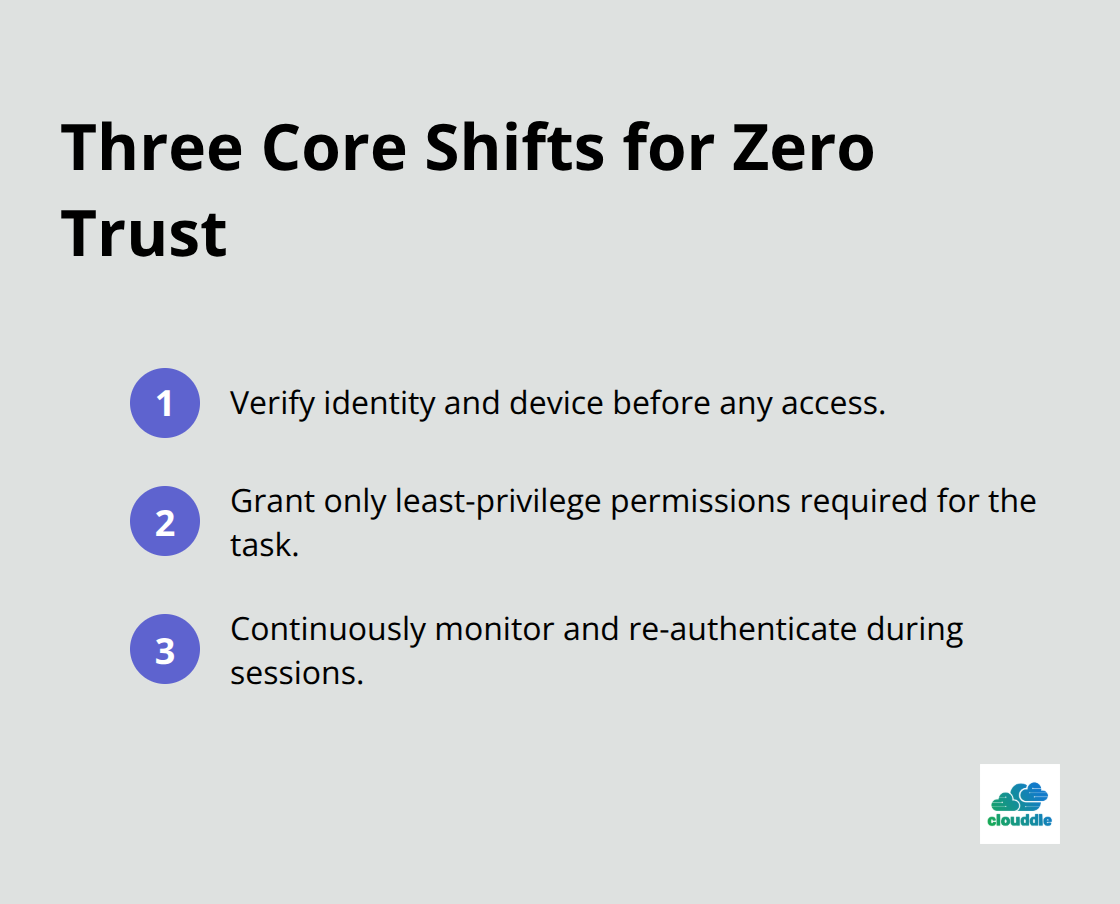
Zero Trust rejects the perimeter-based model entirely. Instead of trusting anything inside the network boundary, it treats every access request as a potential threat requiring explicit verification. This shift demands three concrete changes.
First, organizations must implement identity-based access controls that verify who users are and what devices they use before granting access, regardless of network location. Second, access must follow the principle of least privilege, granting only the minimum permissions needed for specific tasks. Third, systems must continuously monitor and authenticate throughout the session, not just at entry.
The Timeline for Change Is Accelerating
The transition isn’t instantaneous, but it’s unavoidable. According to the State of Zero Trust 2025, 42% of organizations believe their current security model will be outdated within two years. The drivers pushing this change are concrete: 38% cite major security incidents as the primary catalyst, 30% point to employee complaints about slow access, and 29% cite compliance or audit findings.
Organizations that wait until a breach forces their hand will face far greater costs than those who implement Zero Trust proactively. The question isn’t whether your organization will adopt Zero Trust, but whether you’ll do so on your own timeline or in response to a crisis. Understanding the core principles behind this framework-and how to apply them-determines whether your transition strengthens your security posture or leaves you vulnerable during the shift.
How to Build Zero Trust in Three Steps
Start with Identity Verification
Identity verification forms the foundation of Zero Trust, and it must happen before any user or device accesses your network. The State of Zero Trust 2025 report reveals that only 23% of organizations have fully automated identity-based access controls, meaning the vast majority still rely on manual processes or fragmented systems that create security gaps.
Audit your current identity infrastructure first. Map which applications require access, identify who legitimately needs that access, and document what permissions they actually use versus what they have been granted. Most organizations discover they’ve granted far more access than necessary during this audit.
Implement multi-factor authentication across all critical applications immediately, not as a future phase. This single step blocks 99.9% of account-based attacks according to Microsoft security research. Next, integrate your identity system with your network access controls so that authentication happens once and propagates across your entire environment. Organizations using Okta or Ping Identity for identity management report faster implementation than those attempting to bolt identity controls onto legacy VPN infrastructure.
The goal is straightforward: every access request, regardless of whether the user works in your office or remotely, must pass validation against your identity system before the connection establishes.
Enforce Least Privilege Access
Least privilege access means granting permissions that expire or adjust based on real-time context, not static roles that persist indefinitely. The access retention problem is severe: the State of Zero Trust 2025 found that 68% of former employees retain access to their previous employer’s systems, creating persistent security exposure.
Implement Just-In-Time access provisioning where permissions grant only when needed and automatically revoke after a defined period or when the task completes. For developers and IT staff accessing production systems, this typically means access lasting hours rather than days.
Microsegmentation complements least privilege by dividing your network into isolated zones so that even if an attacker compromises one system, they cannot move laterally to others without additional authentication. This approach limits breaches by reducing an attacker’s ability to move laterally in the network.
Monitor Access Patterns Continuously
Monitor access patterns continuously and establish baselines for normal behavior. When a user suddenly requests access to resources they’ve never touched before, or when access patterns deviate from historical norms, your system should flag this for review or require additional verification. This continuous monitoring transforms security from a static checkpoint at login into an ongoing verification process throughout the entire session.
Real-time monitoring also reveals when employees attempt workarounds or request access outside normal patterns. These moments present opportunities to adjust policies or provide better access tools rather than forcing users toward riskier alternatives. The organizations that succeed with Zero Trust treat monitoring as a feedback mechanism that improves both security and usability simultaneously, which means your next step involves selecting the right tools and platforms to operationalize these three principles across your entire infrastructure.
How Zero Trust Protects Organizations Across Industries
Financial Services: Reducing Breach Risk Through Access Control
Organizations implementing Zero Trust move from reacting to breaches toward preventing them entirely. Financial institutions face constant pressure from regulators and sophisticated attackers targeting customer data and transaction systems. When a major bank implemented identity-based access controls with continuous authentication, they reduced unauthorized access attempts by 94% within six months. The shift required mapping every application and identifying which employees legitimately needed access to payment systems. Developers accessing production environments now receive access for specific tasks lasting hours rather than days, eliminating the risk of forgotten credentials granting persistent access. The bank’s security team reports that lateral movement detection improved dramatically because microsegmentation now isolates critical systems, preventing attackers from moving between networks even if they compromise an initial endpoint. This approach costs less than responding to a single major breach, which averages $2.94 million according to IBM’s 2024 Cost of a Data Breach Report.
Healthcare: Securing Patient Data Across Multiple Locations
Healthcare organizations face different but equally urgent pressures. Patient data breaches trigger regulatory fines, lawsuits, and destroyed trust. A large healthcare provider implemented Zero Trust to secure access to electronic health records across multiple hospitals and clinics. They discovered that 340 employees retained access to patient data from previous roles, creating exposure that audits had missed. Zero Trust enforcement immediately revoked these permissions while implementing role-based access that adjusted automatically when employees transferred departments. Continuous monitoring revealed that 12% of their workforce was circumventing security controls to access records faster, signaling that their original policies created friction with clinical workflows. Rather than forcing stricter rules, they adjusted approval processes and invested in faster authentication, reducing access request time from 45 minutes to 3 minutes. Patient data access now requires explicit verification every session, and attempts to access records outside a clinician’s department trigger immediate alerts.
Enterprise: Managing Distributed Workforces Globally
Enterprise companies managing distributed workforces across multiple countries face complexity that legacy VPNs cannot handle. A global technology company with 8,500 employees struggled with 32% reporting slow VPN connections that delayed product launches. They implemented identity-centric Zero Trust using cloud-delivered access controls. Employees now authenticate through their identity provider and receive access provisioned in seconds rather than hours, experiencing consistent performance whether working from offices, home, or traveling. The company reduced onboarding time to network access from 2 days to 15 minutes, directly improving time-to-productivity for new hires. Security incidents decreased because every access request passes through their identity system, which flags suspicious patterns like an engineer accessing sales databases or a contractor accessing source code repositories outside their project.
Final Thoughts
Zero Trust network security is no longer a theoretical framework reserved for organizations with unlimited budgets. The evidence is clear: companies implementing these principles reduce breach risk, improve employee productivity, and align security with how modern work actually happens. The financial services, healthcare, and enterprise organizations discussed earlier adopted Zero Trust because legacy security models were failing them, not because it was trendy.
Your organization faces the same choice. The State of Zero Trust 2025 shows that 42% of companies believe their current security model will be outdated within two years. Start now with three concrete steps: audit your identity infrastructure and implement multi-factor authentication across critical applications, enforce least privilege access through Just-In-Time provisioning and microsegmentation, and establish continuous monitoring that treats every access request as a potential threat requiring verification. Organizations successfully implement Zero Trust incrementally, starting with identity controls and expanding to network segmentation and cloud-delivered security services as their maturity increases.
Map your current access patterns, identify where legacy systems create security gaps, and prioritize securing your most critical applications and data first. We at Clouddle provide the connectivity and security foundation you need to implement Zero Trust effectively, with 24/7 support ensuring your team isn’t managing this alone. The organizations protecting themselves from modern threats aren’t waiting for the perfect moment to start-they’re starting now.


