Perimeter-based security is dead. Hackers now operate inside your network, and traditional firewalls can’t stop them.
Zero trust networking flips the script by treating every user, device, and connection as a potential threat. At Clouddle, we’ve seen organizations cut security incidents dramatically by adopting this approach.
Why Your Current Security Approach Is Failing
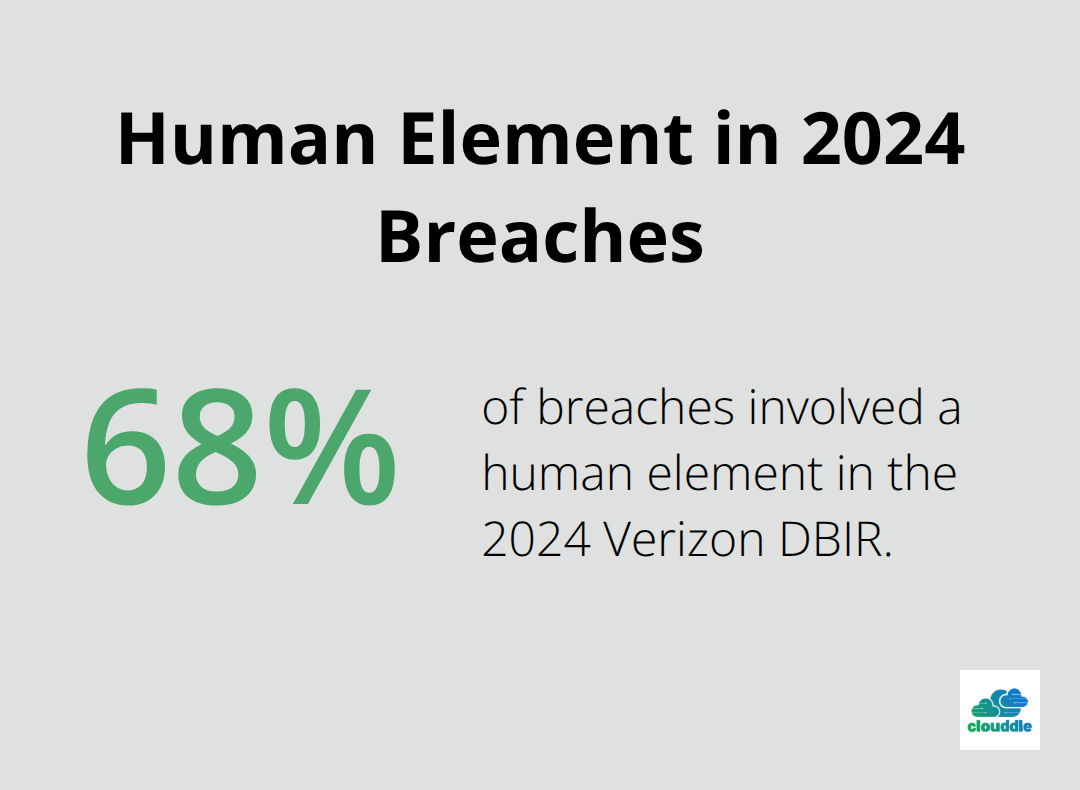
The shift away from perimeter-based security isn’t optional anymore. Organizations treating their networks as fortified castles face breaches regularly, and the numbers prove it. According to the 2024 Verizon Data Breach Investigations Report, 68% of breaches involved a human element, whether through compromised credentials or social engineering. This means your firewall cannot stop an attacker who already possesses valid login credentials. Internal threats have become the primary attack vector, and traditional security models cannot detect or prevent lateral movement once someone enters your network.
Credentials Compromise Has Become the Normal
Credential theft and reuse accelerate at alarming rates. Attackers no longer need to exploit zero-day vulnerabilities or break through your perimeter-they purchase stolen credentials on the dark web for pennies and walk straight in. A compromised password from a contractor, a phishing email that lands with a legitimate-looking login link, or a developer’s API key left in a GitHub repository gives attackers everything they need to gain entry. Once inside, they move laterally across your network, accessing systems they should never touch. Perimeter security cannot stop this threat because the attacker is already authenticated.
Compliance Standards Now Mandate Continuous Verification
Regulatory bodies have caught up to reality. The US Department of Homeland Security and the Office of Management and Budget now require federal agencies to adopt zero trust principles, with OMB Memorandum 22-09 providing explicit implementation guidance. NIST SP 800-207 Zero Trust Architecture has shifted from recommendation to compliance baseline. Organizations in healthcare, finance, and critical infrastructure face mounting pressure to prove they verify every access request in real time, not just at the perimeter. Companies that treat access control as a one-time gate at the network edge will struggle to pass modern audits. The regulatory environment demands that you verify identity and device posture continuously, on every single request, regardless of location or past authentication.
The Cost of Inaction Keeps Rising
Every day you operate without zero trust verification, you expose your organization to preventable breaches. The average cost of a data breach in 2024 reached $4.88 million, according to IBM’s Cost of a Data Breach Report. Organizations that implement zero trust principles reduce their breach costs significantly because they contain incidents within microsegments rather than allowing attackers to roam freely across the entire network. The financial pressure alone-combined with regulatory mandates and the reality that your current defenses fail against internal threats-makes the transition to zero trust not a question of if, but when. Your competitors who move first gain a security advantage that translates directly to lower risk and operational resilience. The question now becomes how to implement zero trust effectively across your infrastructure.
How to Build Zero Trust Into Your Access Control
Zero trust isn’t a single switch you flip. It’s a framework that requires identity verification at every access request, device posture checks before granting permissions, and continuous monitoring across your entire infrastructure. The shift demands that you stop trusting based on location or past authentication and start verifying every single transaction. The practical reality is straightforward: most companies fail because they treat zero trust as a technology problem rather than an operational one.
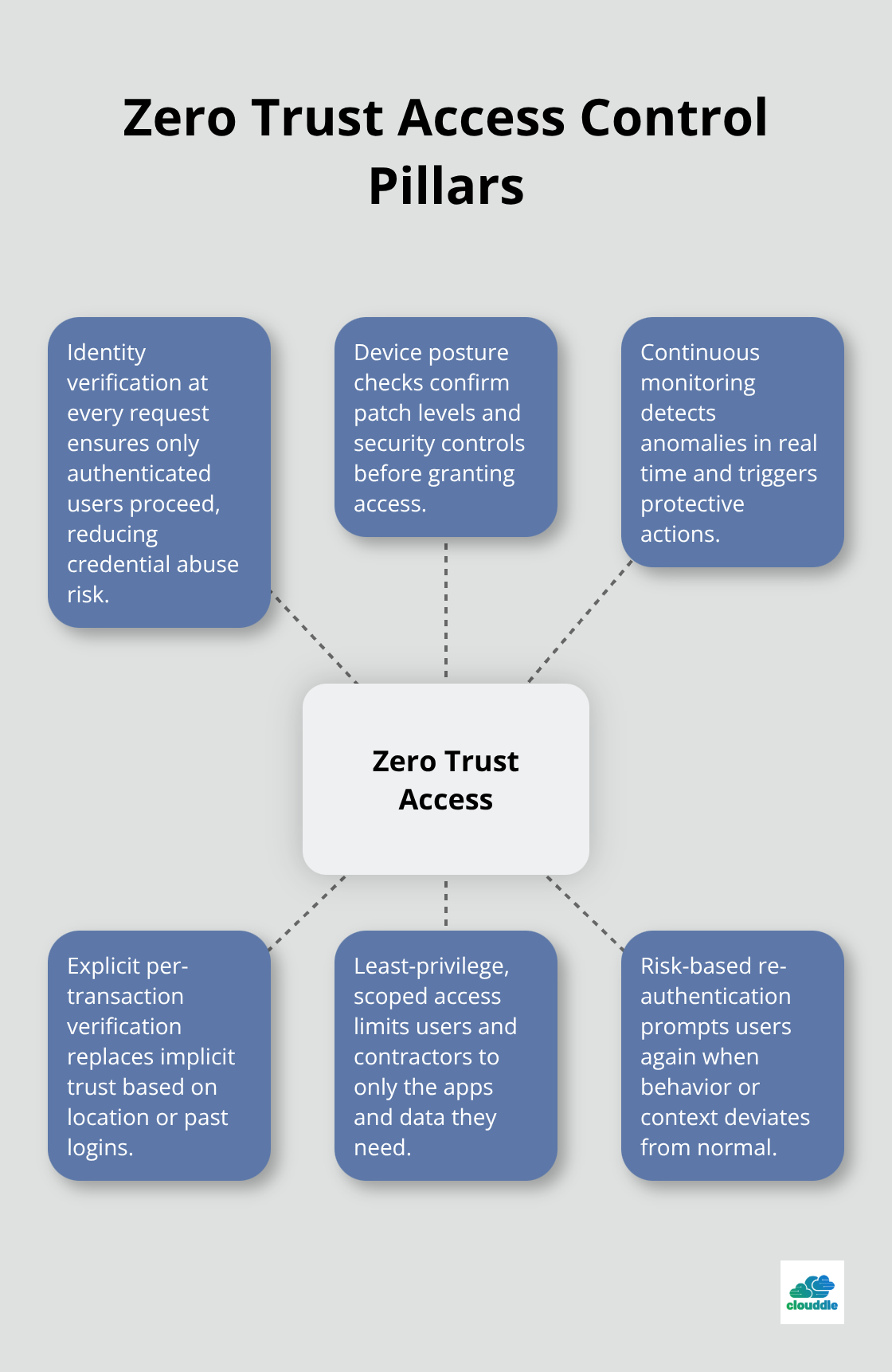
Your team needs to understand that every access decision-whether a user logs into an application, a device connects to the network, or a service communicates with another service-must include explicit verification. The DHS CISA framework defines this as granting access to all resources including applications, devices, printers, and IoT on a per-request basis with identity and device context. This means you cannot rely on a single login at the start of the day. Instead, you implement continuous re-authentication based on real-time risk signals.
Identity and Device Posture Replace Network Location
Your access control decisions must pivot away from network location entirely. The NIST SP 800-207 Zero Trust Architecture framework emphasizes that decisions should depend on verified identity, device security posture, and contextual factors-not whether someone is inside or outside your corporate network. This means implementing hardware-based multi-factor authentication rather than SMS codes or email one-time passwords, which remain vulnerable to interception. When a contractor onboards, they receive access to only the specific applications they need for their role, not broad network access. When a device hasn’t received security patches in 30 days, access policies automatically restrict it to lower-sensitivity resources.
Start by auditing what your current users actually access versus what they’re theoretically permitted to access. Most organizations find massive privilege creep where employees retain access from previous roles or projects they no longer touch. Eliminating this overpermissioning immediately reduces your attack surface.
Microsegmentation Stops Lateral Movement
Once an attacker gains initial access, zero trust microsegmentation prevents them from moving freely across your network. Rather than treating your entire network as one flat zone, you partition it into smaller segments where each segment enforces strict access policies. A compromised endpoint in your guest Wi-Fi network cannot automatically access your financial systems or patient records, even if the attacker obtains valid credentials. The DHS Zero Trust Maturity Model links higher maturity levels to greater automation and analytics, meaning mature deployments use behavioral analysis to detect when a device or user deviates from normal access patterns.
If an employee’s account suddenly attempts to access 200 files in your data repository when they normally access 5, automated policies trigger re-authentication or block the request entirely. Continuous monitoring isn’t optional-it’s the foundation that makes everything else work. Tools that track network traffic, connected device inventory, and real-time behavior enable you to catch breaches within microsegments rather than after attackers have stolen your entire database. This segmentation approach transforms your network from a single point of failure into a series of isolated zones that contain damage and slow attackers significantly.
How Zero Trust Transforms Enterprise Security Operations
Enterprise Organizations Reduce Breach Containment Time
Enterprise organizations implementing zero trust report measurable reductions in breach containment time and lateral movement incidents. Microsoft deployed zero trust across its own operations as part of the Secure Future Initiative, embedding verification principles into its security infrastructure to protect user accounts, devices, applications, and data across distributed environments. Organizations that transition from perimeter-based models to identity-centric access control consistently detect and isolate compromised accounts before attackers move laterally. The shift requires replacing implicit trust with explicit verification at every transaction, and companies that execute this transition properly find that their security operations teams spend less time responding to widespread breaches and more time on strategic security improvements.
Federal agencies mandated by OMB Memorandum 22-09 to adopt zero trust principles now use continuous verification to prevent attackers from exploiting stolen credentials. When you implement microsegmentation alongside identity verification, a compromised credential no longer grants access to your entire network; instead, the attacker faces re-authentication requirements and behavioral anomaly detection that triggers immediate alerts.
Remote Workforces Operate Without Network Bottlenecks
Remote workforces operating across multiple devices and cloud applications benefit enormously from zero trust because access decisions no longer depend on network location. Traditional VPN approaches create bottlenecks and false assumptions of security simply because users connect through company infrastructure, but zero trust replaces this model with per-request verification regardless of whether employees work from offices, home networks, or client sites.
Organizations onboarding contractors or temporary staff can grant immediate access to specific applications without provisioning broad network permissions, reducing both security risk and administrative overhead. Hardware-based multi-factor authentication combined with continuous device posture monitoring means that a contractor’s unpatched laptop automatically receives restricted access to lower-sensitivity resources until security patches are applied.
Critical Infrastructure Operators Protect Public Safety
Critical infrastructure operators protecting power grids, water systems, and telecommunications networks increasingly adopt zero trust principles because the consequences of breach containment failures extend beyond financial loss to public safety. The DHS Zero Trust Maturity Model demonstrates that mature implementations use automation and analytics to detect anomalous behavior in real time, enabling security teams to stop attacks within microsegments rather than after compromise spreads across interconnected systems.
Final Thoughts
Zero trust networking has shifted from emerging best practice to operational necessity. Organizations across every sector now recognize that network location no longer determines trustworthiness, and access decisions must rest on continuous verification of identity and device posture. The regulatory environment, threat landscape, and financial consequences of breaches have made this transition unavoidable.
Starting your zero trust journey requires three concrete actions. First, audit your current access permissions and eliminate privilege creep where employees retain access from previous roles. Second, implement identity verification at every access request using hardware-based multi-factor authentication rather than weaker alternatives. Third, deploy microsegmentation to partition your network into isolated zones where breach containment happens automatically.

These steps build incrementally as your team gains experience with continuous verification and behavioral monitoring. Organizations operating under zero trust principles reduce breach response costs, lower compliance audit friction, and free security teams from reactive incident response to strategic improvements. Your workforce gains seamless access to applications they need without network bottlenecks, contractors onboard in minutes rather than days, and remote employees operate without VPN constraints. Automation handles continuous verification and policy enforcement rather than requiring manual security reviews, which improves operational efficiency significantly.
Implementing zero trust requires more than technology alone-it demands operational commitment and strategic planning. Clouddle’s managed IT and security services help organizations build the foundation that makes zero trust sustainable. The transition starts today with a clear-eyed assessment of your current posture and a commitment to verification over assumption.


