Cyber attacks hit businesses every 39 seconds, making robust security measures non-negotiable for organizations of all sizes. The financial impact is staggering, with data breaches costing companies an average of $4.45 million in 2023.
At Clouddle, we’ve seen firsthand how proper cybersecurity tips can prevent devastating attacks. This guide covers practical strategies that actually work in real-world scenarios.
What Cyber Threats Target Your Business Most
Phishing attacks serve as the primary entry point for cybercriminals, with 75% of organizations experiencing successful phishing attempts according to Proofpoint’s 2023 State of the Phish report. These attacks target employees through deceptive emails that mimic legitimate communications from banks, vendors, or internal systems. The most dangerous phishing campaigns use spear-phishing tactics, where attackers research specific employees and craft personalized messages.

Finance departments receive 3x more targeted phishing attempts than other departments, which makes them high-priority targets for security training.
Ransomware Strikes With Unprecedented Success
Ransomware attacks have seen unprecedented success, with ransomware groups experiencing a 55.5% surge in victims, totaling 5,070 in 2023. The most devastating attacks come from groups like LockBit and ALPHV, which infiltrate networks through compromised remote desktop protocols and unpatched vulnerabilities. Small businesses face particular risk because 60% lack proper backup systems, which forces them to either pay ransoms or lose critical data permanently. Healthcare organizations pay the highest ransoms (averaging $1.85 million per incident) because patient data cannot be replaced.
Password Attacks Exploit Human Weakness
Weak passwords remain the easiest attack vector, with 81% of data breaches involving compromised credentials according to Verizon’s 2023 Data Breach Investigations Report. Cybercriminals use credential stuffing attacks, which test millions of stolen username-password combinations across multiple sites within hours. The most common passwords like “123456” and “password” can be cracked in under one second with modern computing power. Multi-account breaches occur when employees reuse the same password across business and personal accounts, which gives attackers access to multiple systems simultaneously.
These threats demonstrate why reactive security measures fall short in today’s threat landscape. Organizations need proactive defense strategies that address vulnerabilities before attackers exploit them.
How Do You Build Effective Security Defenses
Multi-factor authentication blocks over 99.9% of account compromise attacks according to Microsoft’s security research, which makes it the most effective single security control available. Organizations that implement MFA see immediate results, with financial services companies that report 76% fewer successful breaches after deployment. The most secure MFA methods use authenticator apps like Microsoft Authenticator or Google Authenticator rather than SMS codes, which attackers can intercept through SIM swapping attacks. Hardware security keys provide the strongest protection for high-value accounts, with Google that reports zero successful phishing attacks against employees who use hardware keys since 2017.
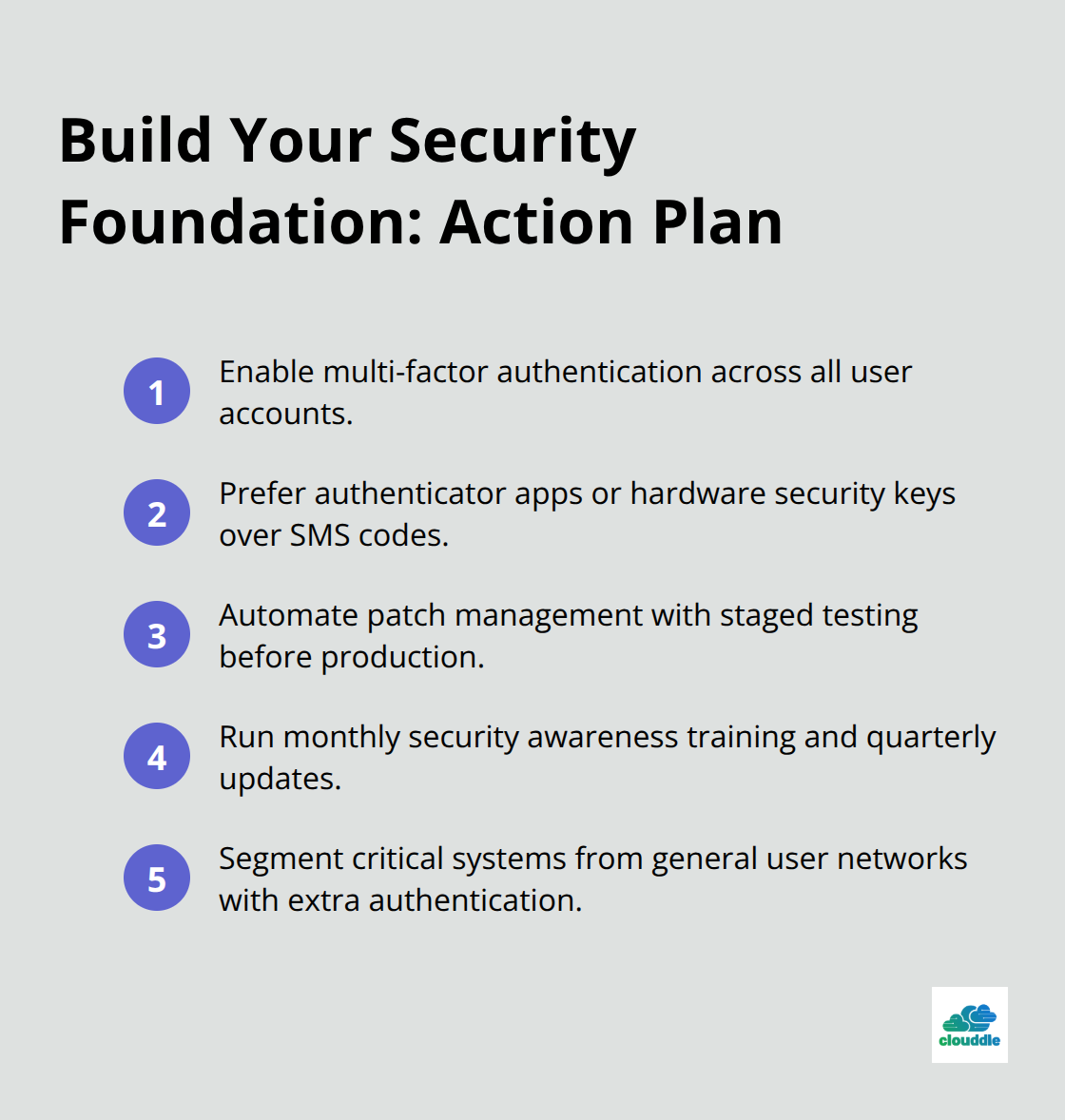
Patch Management Prevents Majority of Breaches
Unpatched vulnerabilities cause a significant portion of data breaches, with attackers who exploit known flaws within 15 days of public disclosure according to security research. The most dangerous delays occur with operating system patches, where Windows systems face active exploitation within 24 hours of vulnerability announcements. Organizations need automated patch management systems that test updates in environments before production deployment (rather than manual processes that create delays). Critical infrastructure companies like Equifax suffered massive breaches because they delayed patches for known vulnerabilities for 147 days, which allowed attackers to steal 147 million records.
Security Training Reduces Human Error by 70%
Employee training programs reduce security incidents by 70% when organizations implement them with monthly security awareness training and quarterly security updates. The most effective training focuses on real-world scenarios rather than generic presentations, with hands-on exercises that simulate actual attack methods. Companies that conduct weekly security briefings see 45% better threat recognition rates compared to annual sessions. Healthcare organizations achieve the best results with role-specific training, where nurses learn different security protocols than IT administrators based on their actual job responsibilities and threat exposure levels.
Network Segmentation Limits Attack Spread
Network segmentation prevents lateral movement attacks that allow cybercriminals to access multiple systems once they breach initial defenses. Organizations that implement proper network segmentation contain breaches 200% faster than those with flat network architectures (according to IBM’s Cost of a Data Breach Report 2023). The most effective approach separates critical systems from general user networks, with financial data isolated on separate network segments that require additional authentication. Zero-trust architecture takes this further by treating every connection as potentially hostile, which forces verification for each access request regardless of network location.
These foundational security measures create multiple barriers that attackers must overcome, but advanced monitoring and response capabilities provide the final layer of protection that organizations need to detect and neutralize sophisticated threats.
What Advanced Security Measures Stop Sophisticated Attacks
Zero Trust Architecture Eliminates Network Perimeters
Zero trust security models treat every network connection as potentially hostile, which forces verification for each access request regardless of user location or device. The most effective zero trust deployments require device certificates, user authentication, and application-level permissions for every system interaction. Google’s BeyondCorp implementation demonstrates this approach, where employees access internal applications through secure tunnels that verify identity and device health before they grant access. Organizations implementing zero trust architecture can improve their overall security posture by eliminating implicit trust assumptions within network segments.
Continuous Monitoring Detects Threats Within Minutes
Security Information and Event Management systems analyze network traffic patterns to identify anomalous behavior that indicates potential breaches.
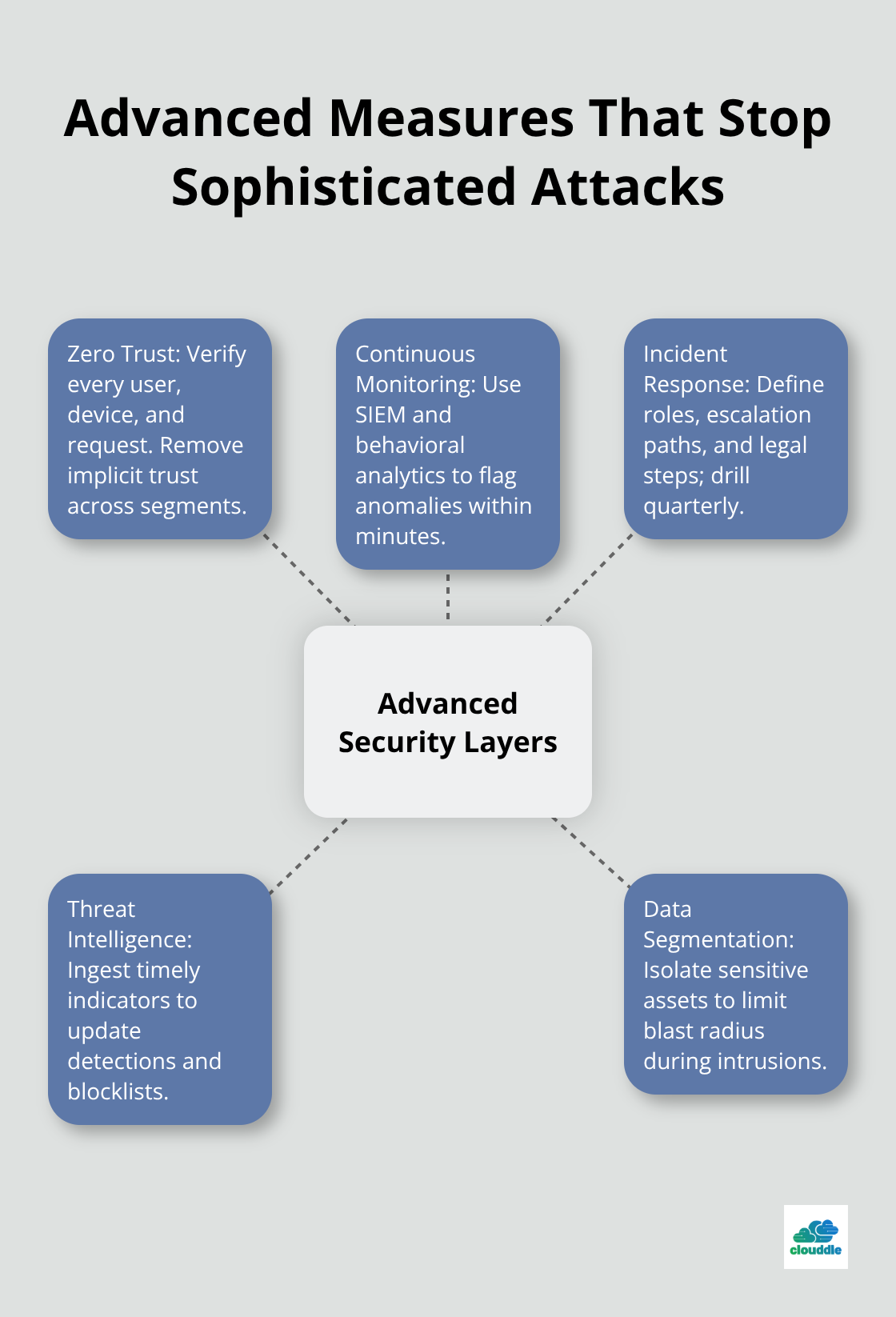
Organizations with 24/7 security monitoring detect threats significantly faster than those that rely on manual detection methods. The most sophisticated platforms use machine learning algorithms to establish baseline user behavior patterns, which triggers alerts when employees access unusual systems or transfer large data volumes outside normal patterns. Healthcare organizations achieve the best results with behavioral analytics that detect ransomware encryption activities within minutes of initial file modifications. Real-time threat intelligence feeds from sources like the Cybersecurity and Infrastructure Security Agency provide immediate updates about attack vectors and compromised IP addresses.
Incident Response Plans Reduce Recovery Time Significantly
Organizations with tested incident response plans contain breaches faster than those without formal procedures. The most effective response plans assign specific roles to team members, with clear escalation procedures and communication protocols that activate within minutes of threat detection. Tabletop exercises that teams conduct quarterly help practice response procedures, with financial services companies that conduct regular drills showing better coordination during actual incidents. Response plans must include legal notification requirements, with disclosure mandates in many jurisdictions that require immediate legal team involvement when personal data faces potential exposure.
Final Thoughts
These cybersecurity tips transform your organization’s security posture from reactive to proactive defense. Multi-factor authentication blocks 99.9% of account compromises, while regular patch management prevents exploitation of known vulnerabilities within critical 15-day windows. Employee training reduces security incidents by 70%, and network segmentation contains breaches 200% faster than flat architectures.
The threat landscape evolves constantly, with ransomware victims that increased 55.5% in 2023 and phishing attacks that target 75% of organizations. Your security measures must adapt accordingly through continuous monitoring, regular security audits, and updated incident response procedures. Organizations that fail to implement these fundamental protections face exponentially higher breach risks and recovery costs.
Start with the fundamentals: deploy MFA across all systems, establish automated patch management, and conduct monthly security training sessions. Then advance to zero trust architecture and behavioral monitoring systems that detect threats within minutes. We at Clouddle provide comprehensive security services that help organizations implement these advanced protections while you focus on core business operations (rather than managing complex security infrastructure internally).


