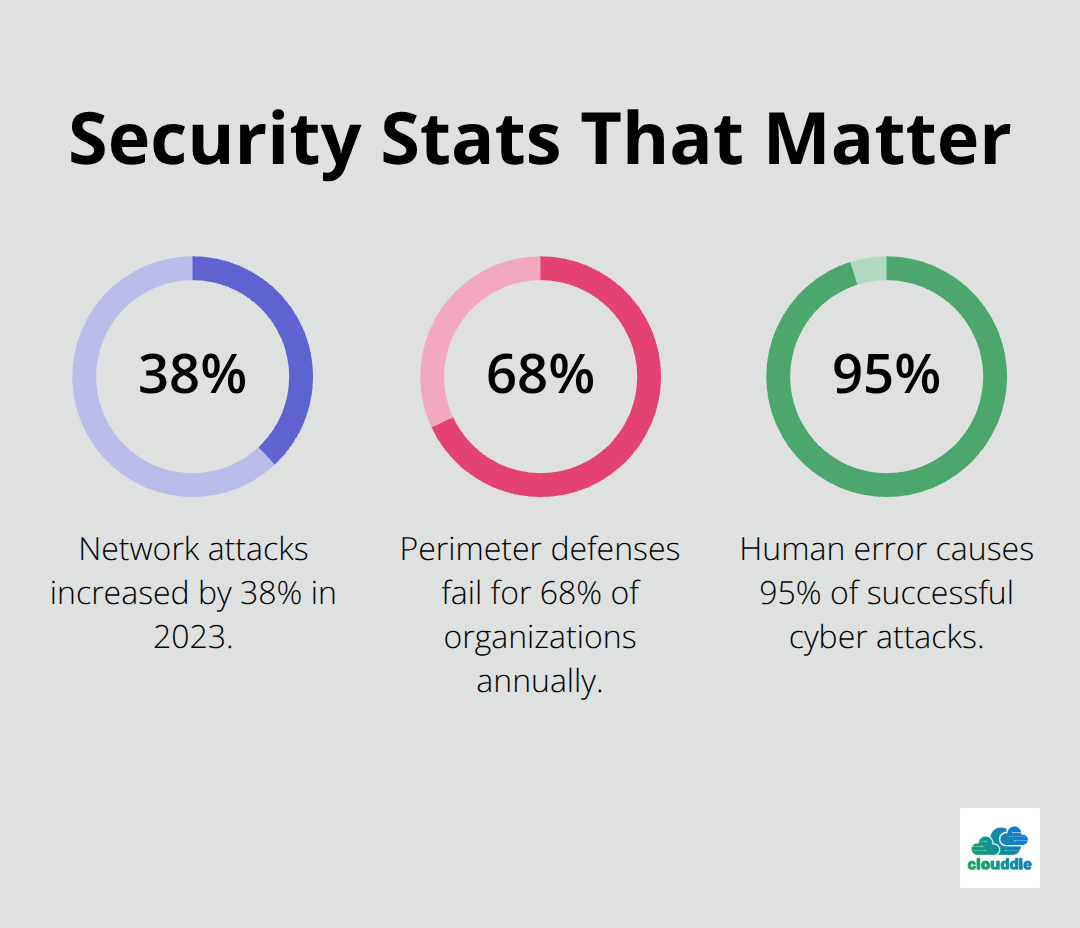
Network attacks increased by 38% in 2023, making robust security measures more important than ever. Most organizations still rely on outdated protection methods that leave critical vulnerabilities exposed.
We at Clouddle see companies struggle with knowing how to improve network security effectively. This guide provides actionable steps to strengthen your defenses and protect your digital assets.
What Should Your Security Assessment Include
Most security assessments miss critical vulnerabilities because organizations focus on surface-level scans instead of comprehensive analysis. A proper security audit must examine your entire network infrastructure, including forgotten legacy systems that hackers love to exploit. Start with asset discovery to map every device connected to your network – from IoT sensors to forgotten test servers that employees set up months ago. According to Cybersecurity Ventures, companies with incomplete asset inventories face 67% more successful breaches than those with comprehensive maps.
Network Vulnerability Detection
Your vulnerability identification process should prioritize systems based on business impact, not just technical severity scores. Focus first on internet-facing applications and database servers that contain sensitive information. Use automated tools like Nessus or OpenVAS, but supplement them with manual tests to catch logic flaws that automated tools miss.
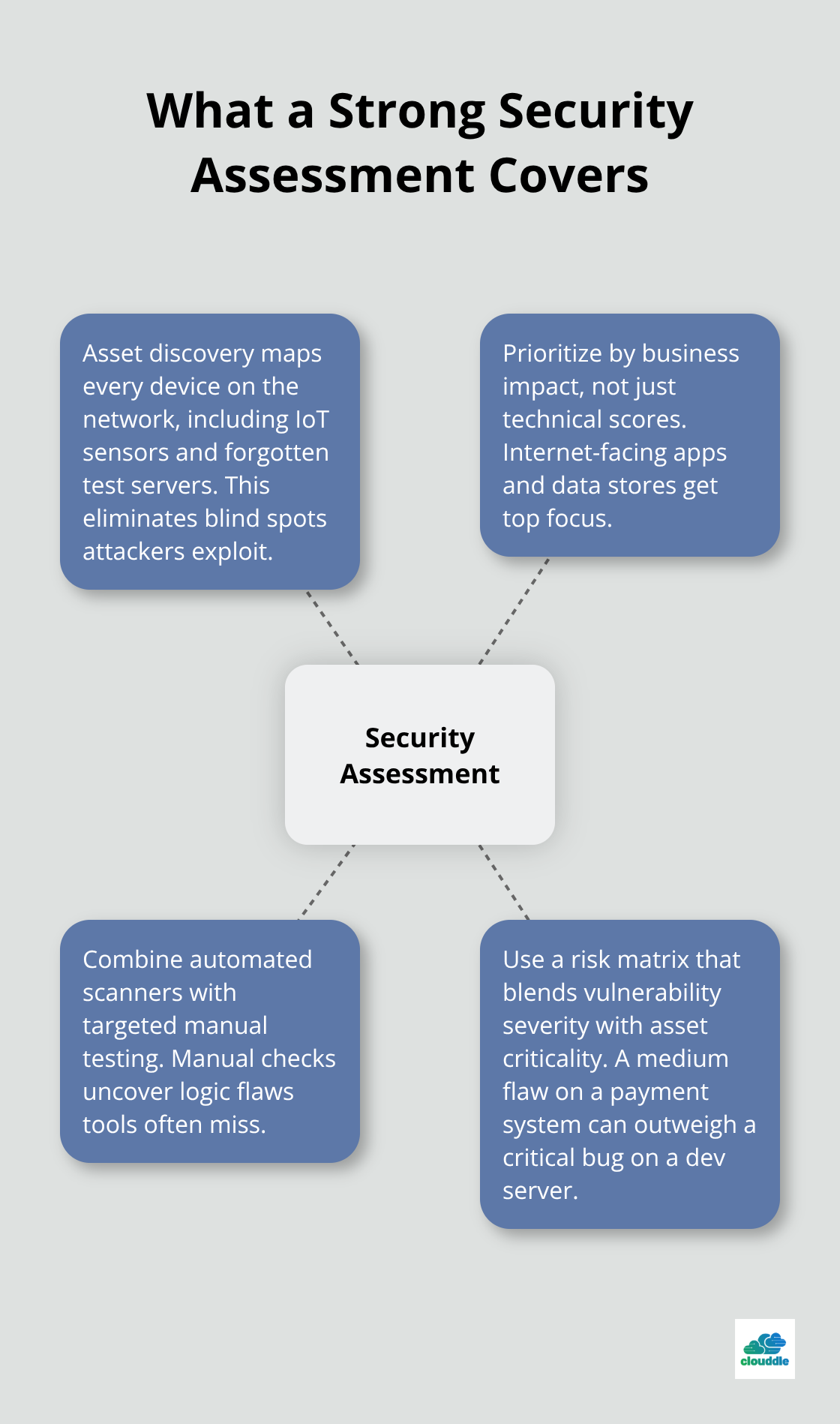
With 2025 on track to set an all-time high for reported vulnerabilities with 21,000+ CVEs disclosed in the first half alone, organizations face an unprecedented challenge in keeping systems secure. Create a risk matrix that combines vulnerability severity with asset criticality – a medium-severity flaw in your payment system poses higher risk than a critical vulnerability in a development server.
Strategic Implementation Plans
Your security implementation plan must address the highest-risk vulnerabilities first while it considers operational constraints. Prioritize quick wins like disabled unused services and changed default passwords before you tackle complex projects like network segmentation. Build implementation timelines that account for business operations (never schedule major security changes during peak business periods). Include rollback procedures for every security change, because poorly implemented security measures can disrupt operations more than the vulnerabilities they aim to fix.
Asset Classification and Priority Matrix
Classify your network assets based on data sensitivity and business function to guide protection efforts. Critical assets include payment processors, customer databases, and core business applications that require immediate attention during incidents. Secondary assets encompass internal tools and development environments that need protection but allow for longer response times. This classification system helps security teams allocate resources effectively and respond to threats with appropriate urgency (rather than treating all alerts equally).
Once you complete your comprehensive assessment and establish clear priorities, you can move forward with implementing the essential security measures that will protect your most valuable assets.
How Do You Implement Core Security Controls
Multi-factor authentication stops 99.9% of automated attacks according to Microsoft research, yet only 22% of organizations enforce MFA across all systems. Start with your most critical applications like email, VPN access, and administrative consoles before you expand to secondary systems. Use app-based authenticators like Microsoft Authenticator or Google Authenticator instead of SMS, which criminals can intercept through SIM swapping attacks. Configure MFA to require approval from two different device types – something users know (password) plus something they have (phone) plus something they are (biometric when available). Deploy conditional access policies that trigger additional verification when users access sensitive data from new locations or devices.
Advanced Perimeter Defense Systems
Your firewall configuration determines whether attackers can reach internal systems, so default deny-all rules work better than attempts to block specific threats. Configure next-generation firewalls with deep packet inspection to analyze traffic content, not just headers and ports. Deploy intrusion prevention systems that can block attacks in real-time rather than just detect them after damage occurs. Position network sensors at critical chokepoints (internet gateways, data center entrances, and between network segments) to catch lateral movement attempts.
Set up automated responses for high-confidence threats like known malware signatures, but route suspicious activities to security analysts for investigation. Modern IPS systems can process over 100 Gbps of traffic while they maintain microsecond response times.
Systematic Patch Management
Software vulnerabilities get exploited rapidly after public disclosure, with threat actors exploiting 161 vulnerabilities with assigned CVEs in the first half of 2025 alone, which makes rapid patches essential for survival. Create separate patch groups based on system criticality – security appliances and internet-facing servers get patches within 72 hours while internal workstations can wait up to two weeks. Test patches in isolated environments that mirror production systems before deployment to avoid broken business operations. Use automated patch management tools like Microsoft WSUS or Red Hat Satellite to handle routine updates while you maintain manual approval for critical system changes.
Network Segmentation Strategy
Network segmentation limits attack spread when perimeter defenses fail (which happens to 68% of organizations annually according to IBM Security). Create separate network zones for different business functions – guest networks, employee workstations, servers, and IoT devices should never share the same network segment. Implement VLANs with strict access controls between segments to prevent lateral movement. Configure micro-segmentation for high-value assets like database servers and payment systems that require additional isolation layers.
These foundational security controls create the framework for protection, but effective security requires continuous monitoring and employee awareness to maintain strong defenses against evolving threats.
How Do You Maintain Strong Security Over Time
Human error causes 95% of successful cyber attacks, which makes employee education your most powerful defense tool. Train employees monthly on specific threats they encounter daily – phishing emails that request password changes, USB drives left in parking lots, and social engineering calls that ask for system access. Use simulated phishing campaigns to test awareness levels and provide immediate feedback when employees click suspicious links. Companies that conduct quarterly security awareness training experience 70% fewer successful breaches than organizations with annual training programs. Focus training on real-world scenarios specific to your industry rather than generic cybersecurity concepts that employees forget within weeks.
Real-Time Threat Detection Systems
Network monitoring must operate continuously because attacks happen outside business hours when security teams are unavailable. Deploy Security Information and Event Management systems that correlate logs from firewalls, servers, and applications to identify attack patterns that individual systems miss. Configure automated alerts for critical events like multiple failed login attempts, unusual data transfers, or connections to known malicious IP addresses. Establish clear escalation procedures that route low-priority alerts to junior analysts while critical threats reach senior security staff immediately. Modern SIEM platforms can process over 10,000 events per second while they maintain response times under five seconds for high-priority incidents. Create incident response playbooks that specify exact steps for common attack scenarios (ransomware, data breaches, and insider threats).
Continuous Vulnerability Management
Quarterly vulnerability assessments fail to catch threats that emerge between scans, which leaves organizations exposed for months. Implement continuous vulnerability scans that run automated tests daily against internet-facing systems and weekly against internal networks. Penetration tests should occur monthly for critical systems and quarterly for secondary infrastructure to identify weaknesses that automated tools miss. Track vulnerability remediation metrics such as mean time to patch and percentage of critical vulnerabilities fixed within 72 hours. Organizations that maintain continuous scan programs detect threats faster than those that rely on periodic assessments.
Automated Response Protocols
Manual incident response creates delays that allow attackers to cause more damage while security teams investigate alerts. Configure automated responses for high-confidence threats like known malware signatures or connections to command-and-control servers. Set up systems that automatically isolate infected devices from the network and block suspicious IP addresses at the firewall level.
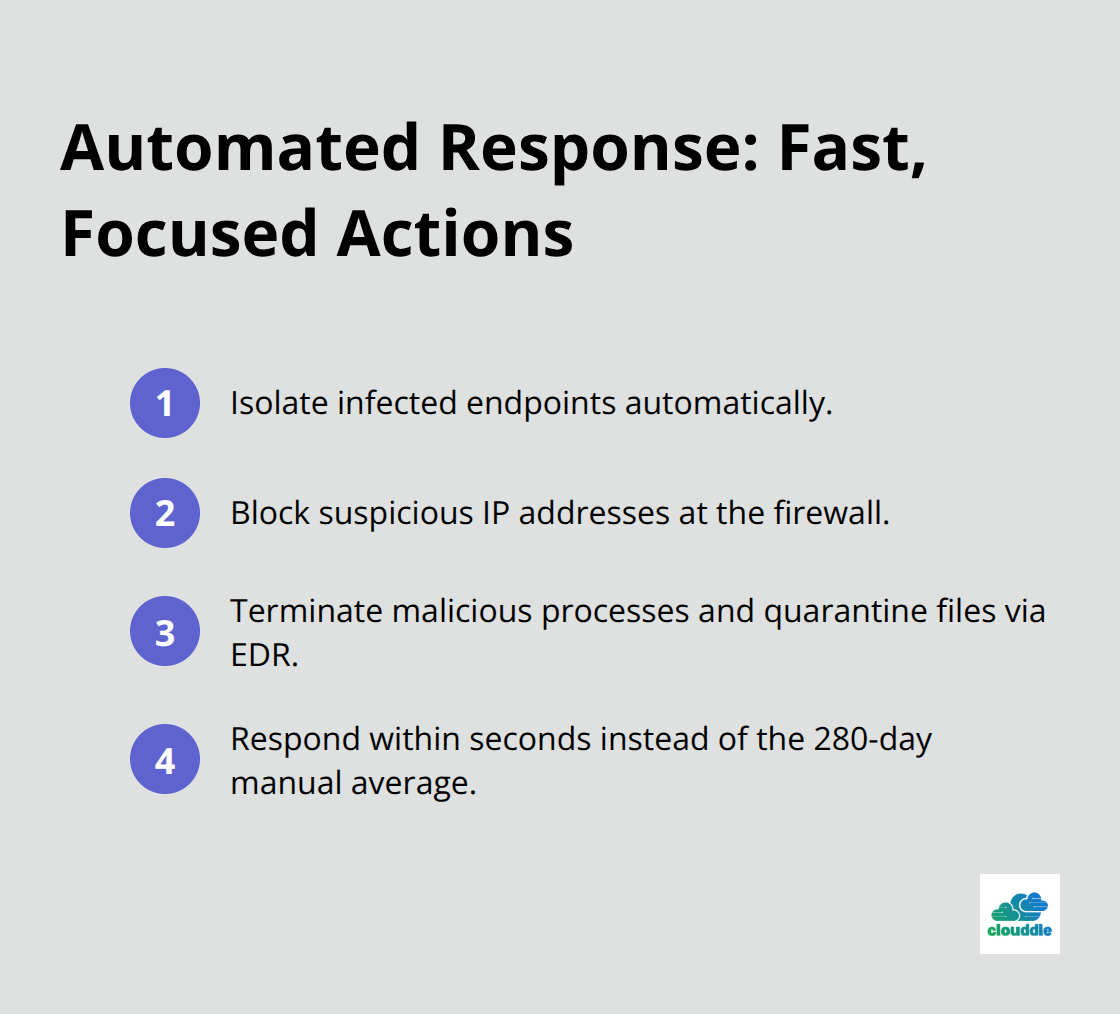
Deploy endpoint detection and response tools that can terminate malicious processes and quarantine affected files without human intervention. Automated systems can respond to threats within seconds compared to the average 280 days it takes organizations to identify and contain breaches manually.
Final Thoughts
Network security demands systematic implementation of multiple defense layers that work together. Organizations that combine comprehensive assessments, strong authentication, advanced firewalls, and continuous monitoring reduce breach risk by 85% compared to those with basic protection methods. These integrated approaches create resilient defenses against sophisticated attack vectors.
Proactive security measures cost significantly less than reactive breach response. The average data breach costs .88 million while comprehensive security programs typically require 10-15% of that investment annually. Companies that implement regular vulnerability assessments and employee training programs detect threats 200 days faster than reactive organizations (which often struggle with delayed incident response).
Your next steps should focus on immediate wins while you build long-term security capabilities. Start with multi-factor authentication deployment and firewall configuration reviews within the next 30 days. Schedule monthly security awareness training and quarterly penetration tests to maintain strong defenses. Understanding how to improve network security means you treat it as an ongoing process rather than a one-time project. We at Clouddle help organizations implement these security measures through our managed IT and security services.


