Cybercriminals launch 4,000 attacks every minute, making traditional security methods obsolete. Organizations need smarter defenses that can adapt and respond at machine speed.
Artificial intelligence for cybersecurity transforms how companies protect their digital assets. We at Clouddle see AI as the game-changer that turns reactive security into proactive defense, stopping threats before they cause damage.
How AI Stops Cyber Attacks in Real Time
Pattern Recognition at Machine Scale
AI systems process network traffic at speeds no human analyst can match. These systems scan millions of data points per second, examining packet headers, payload content, and communication patterns. FortiGuard Labs reports that AI-powered systems analyze massive volumes of data and identify patterns that indicate compromise beyond human capabilities.
Modern AI tools create detailed user profiles through behavioral analytics. These profiles differentiate between normal and suspicious activities across networks. When an employee accesses sensitive files at 3 AM from an unusual location, AI flags this deviation within milliseconds. The system compares current behavior against established baselines and triggers alerts for any significant deviations.
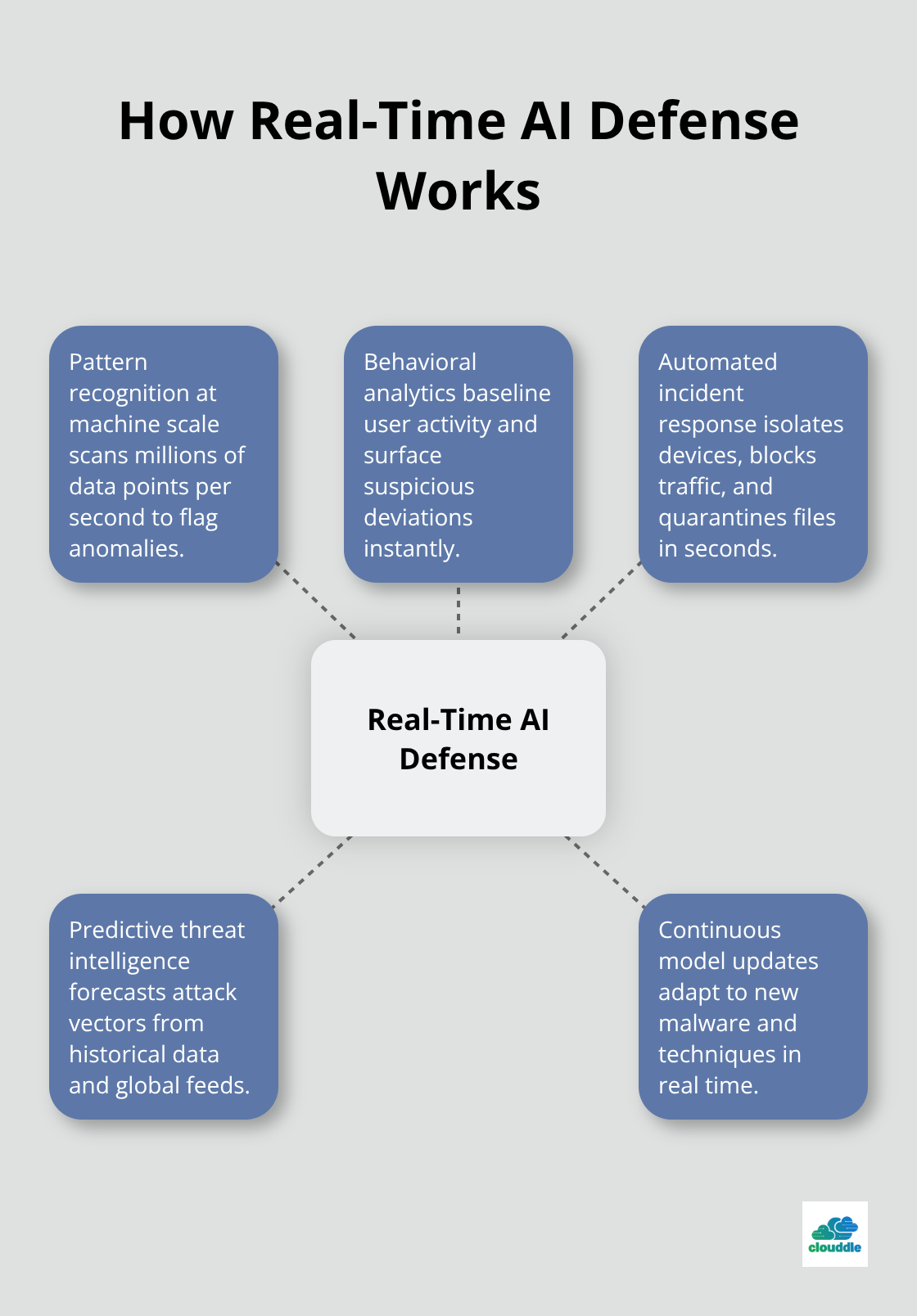
Automated Incident Response Systems
Data breaches cost organizations significantly, with the average global breach reaching USD 4.88 million according to IBM’s 2024 report. Automated response systems isolate compromised devices, block malicious traffic, and quarantine suspicious files without human intervention. These systems execute predefined playbooks that contain threats while they alert security teams for further investigation.
AI-driven Security Information and Event Management solutions enhance threat detection speed through advanced data analysis. Organizations implementing AI for incident response benefit from automated incident response capabilities that transform security operations. The automation removes routine tasks from cybersecurity staff and reduces human error rates significantly.
Predictive Threat Intelligence
AI transforms cybersecurity from reactive to predictive approaches. Machine learning algorithms analyze historical attack data to forecast future threats and identify attack vectors before criminals deploy them. The 2025 Global Threat Landscape Report demonstrates how AI acceleration increases cyberattack sophistication (making predictive capabilities essential for defense).
These systems continuously update threat models based on global intelligence feeds. They adapt to new malware families and attack techniques in real time, creating dynamic defense mechanisms. Organizations can strengthen their defenses before attacks occur rather than respond after damage happens.
Network security applications expand these AI capabilities even further, particularly in areas where traditional security measures fall short.
How AI Transforms Network Security Operations
AI revolutionizes network security through three fundamental applications that address the most persistent vulnerabilities in modern infrastructure. These intelligent systems create comprehensive defense mechanisms that adapt to threats in real time, moving beyond traditional reactive approaches.
Behavioral Analytics Replace Password Dependencies
User authentication becomes dramatically more secure through behavioral analytics that track keystroke patterns, mouse movements, and application usage habits. These systems create unique digital fingerprints for each user and detect account takeovers within seconds when login patterns deviate from established norms. The 2025 Cybersecurity Skills Gap Global Research Report shows that 87% of professionals see AI enhancing cyber roles, particularly in authentication processes where traditional password-based systems fail against sophisticated attacks.
AI-powered authentication systems analyze over 100 behavioral indicators per session. They monitor typing speed, pause patterns between keystrokes, and even pressure sensitivity on touchscreens. When attackers compromise credentials, their behavioral patterns immediately trigger security alerts (even if they possess correct passwords).
Smart Firewalls Abandon Static Rules
Modern firewalls powered by AI abandon static rule sets for dynamic threat assessment capabilities. These intelligent systems analyze traffic patterns, payload content, and connection behaviors to make real-time decisions. Unlike conventional firewalls that rely on predefined signatures, AI-driven solutions identify zero-day exploits and polymorphic malware through anomaly detection.
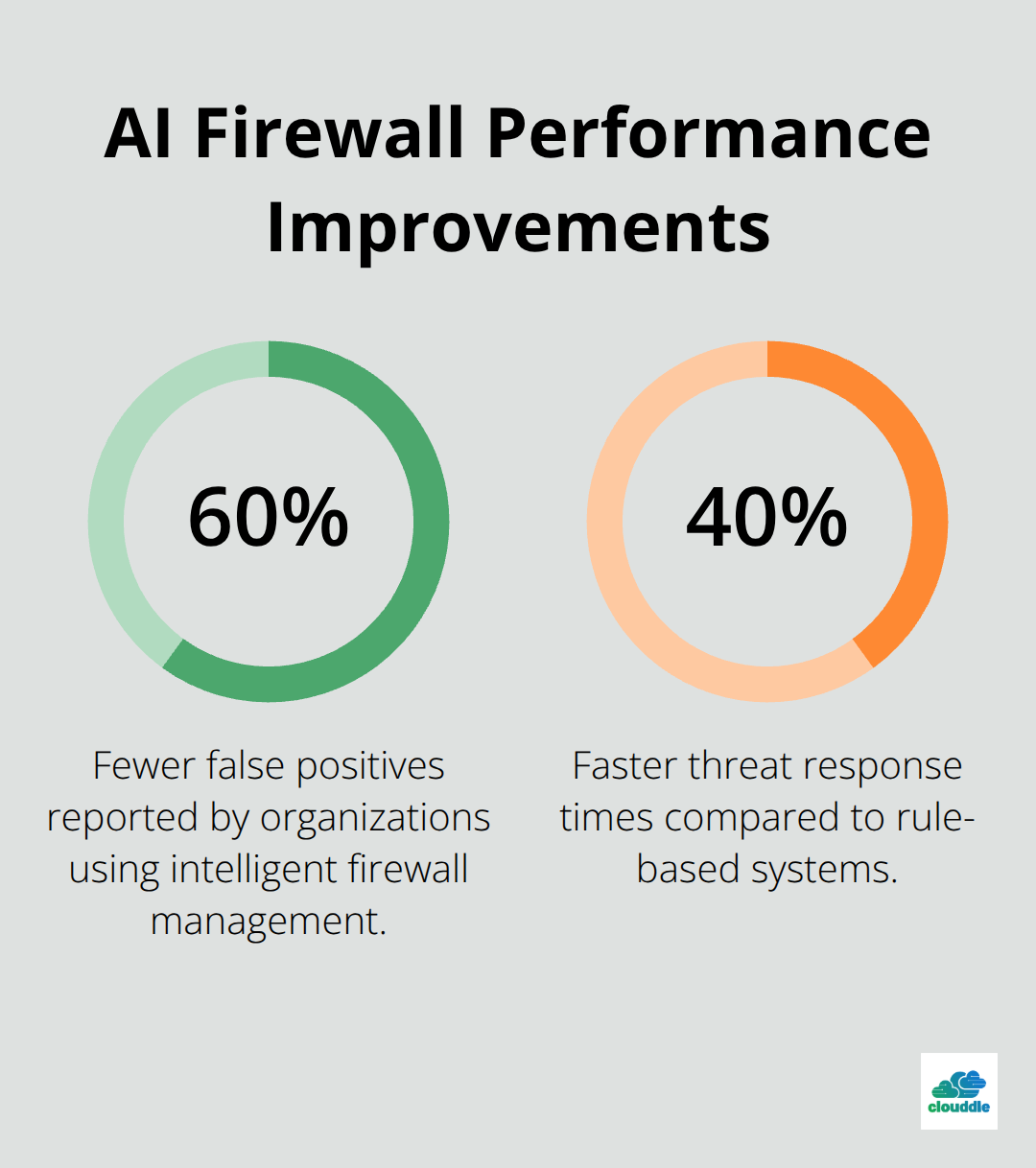
Organizations that implement intelligent firewall management report 60% fewer false positives and 40% faster threat response times compared to rule-based systems. These firewalls learn from every blocked attack and automatically update their defense mechanisms without manual intervention.
Continuous Vulnerability Assessment Replaces Quarterly Scans
Automated vulnerability assessment transforms security posture management from quarterly scans to continuous operations. AI systems scan network infrastructure 24/7 and identify configuration weaknesses, outdated software versions, and exposed services without disruption. These tools prioritize vulnerabilities based on exploitability, business impact, and current threat intelligence rather than generic severity scores.
CISA processes terabytes of data daily through AI for network anomaly detection, which demonstrates the scale and effectiveness of automated assessment capabilities in critical infrastructure protection. These systems correlate vulnerability data with active threat campaigns to focus remediation efforts on the most dangerous exposures.
The success of AI in network security depends heavily on proper implementation strategies that align with organizational needs and existing infrastructure.
How Do You Deploy AI Security Successfully
Organizations face three critical decisions when they implement AI cybersecurity solutions that determine success or failure. The first involves tool selection based on specific threat landscapes rather than marketing promises. Companies must evaluate AI security platforms against their actual attack vectors, with only 1%-10% of supply chains being protected according to recent threat intelligence.
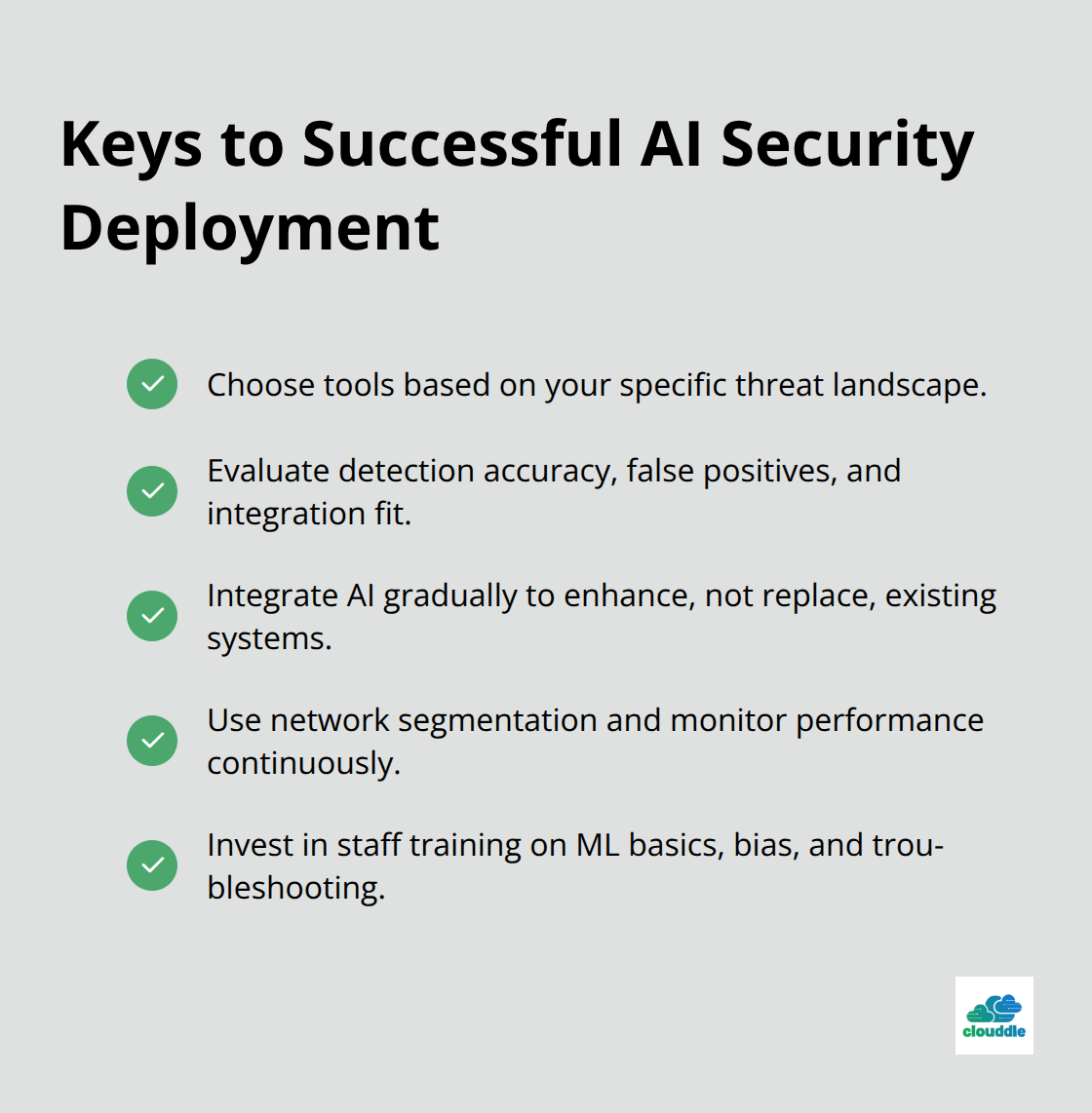
Organizations that handle healthcare data need AI tools specialized in HIPAA compliance and medical device protection, while financial institutions require solutions optimized for payment fraud detection and regulatory reporting. The evaluation process should focus on detection accuracy rates, false positive percentages, and integration capabilities rather than feature lists or vendor reputation alone.
Integration Architecture Determines Performance
Successful AI security implementations require careful integration with existing SIEM systems, firewalls, and endpoint protection platforms. Organizations that attempt to replace entire security stacks with AI solutions experience significant disruption and coverage gaps during transition periods.
The most effective approach involves gradual integration where AI tools enhance existing capabilities rather than replace them completely. Network segmentation becomes essential for AI deployment (allowing organizations to test behavioral analytics on non-critical segments before they expand coverage). Integration with existing infrastructure determines deployment success more than feature lists with continuous monitoring of system performance, threat detection rates, and operational impact before full deployment.
Staff Development Accelerates AI Adoption
AI security tools require specialized skills that traditional cybersecurity training programs do not cover. 88% of organizations have experienced significant cybersecurity consequences due to skills deficiencies, indicating that organizations must invest in upskilling current employees rather than hiring new AI specialists due to talent scarcity.
Security teams need training in machine learning fundamentals, algorithm bias recognition, and AI system troubleshooting to maximize tool effectiveness. Organizations that provide comprehensive AI training report faster threat response times and fewer system configuration errors compared to those that rely on vendor support alone.
Training programs should include hands-on experience with AI model tuning, threat hunting with machine learning tools, and incident response procedures specific to AI-generated alerts. Cybersecurity awareness training must address the practical challenges teams face when they manage AI-powered security systems (rather than theoretical concepts that provide little operational value).
Final Thoughts
Artificial intelligence for cybersecurity delivers measurable advantages that transform organizational defense capabilities. Organizations that implement AI report 60% fewer false positives and 40% faster threat response times compared to traditional security methods. These systems process millions of data points per second and detect threats that human analysts miss entirely.
The next 18 months will bring increased regulatory scrutiny on AI usage in cybersecurity practices. Organizations must prepare for compliance requirements while they leverage AI’s predictive capabilities. Shadow AI presents emerging risks as unauthorized applications potentially compromise security frameworks (making governance frameworks essential for risk mitigation).
Organizations should start with gradual AI integration rather than complete system replacement. Focus on staff development programs that address machine learning fundamentals and algorithm bias recognition. We at Clouddle provide managed IT and security services that help organizations build the foundation they need for effective AI cybersecurity deployment.


