Network attacks cost businesses an average of $4.45 million per breach in 2023, according to IBM’s Cost of a Data Breach Report. These incidents disrupt operations and damage customer trust.
CloudGuard network security offers comprehensive protection against evolving cyber threats. We at Clouddle help organizations implement robust security measures that prevent costly breaches and maintain business continuity.
What Makes Networks Vulnerable to Attack?
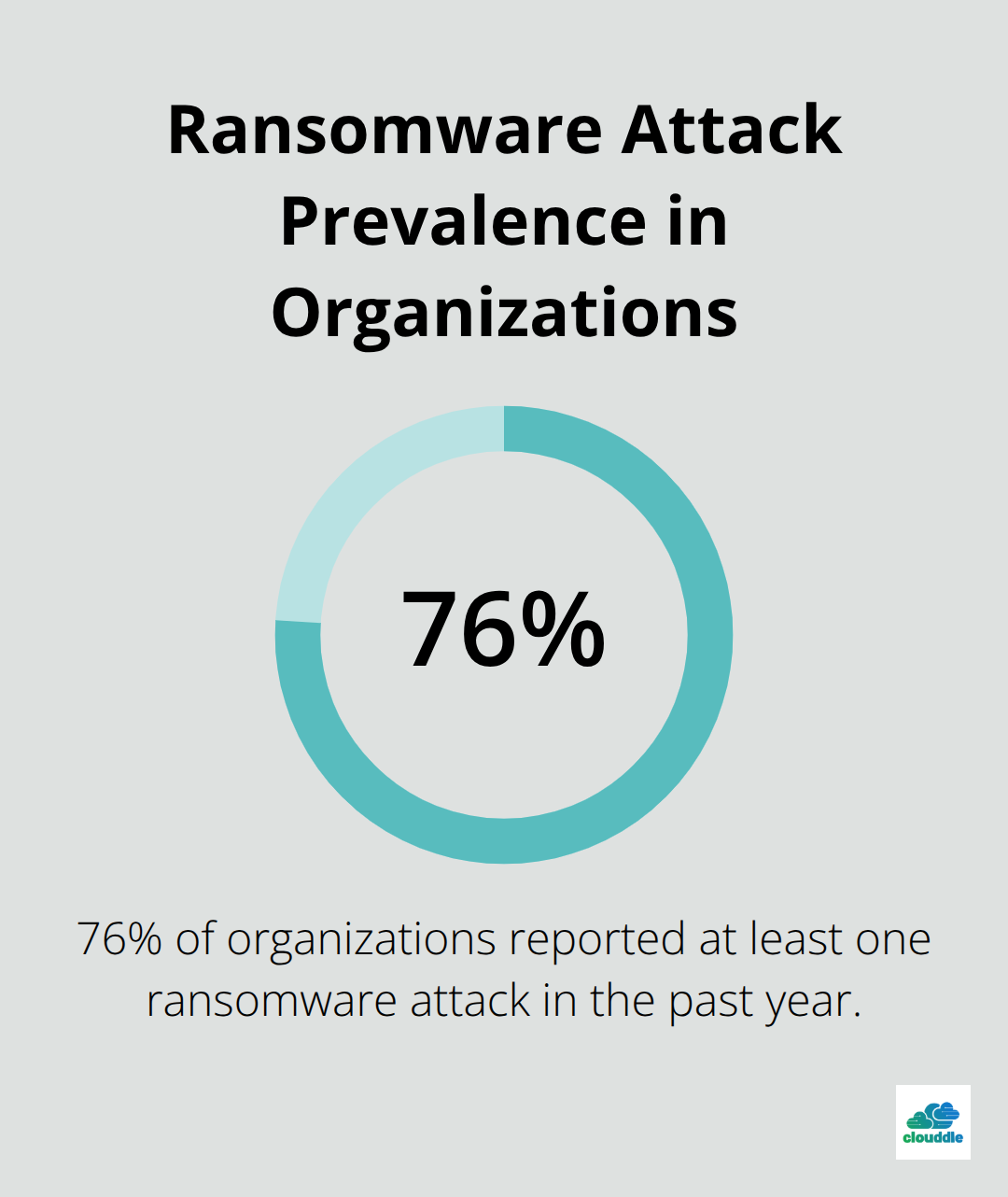
Ransomware Dominates Attack Strategies
Ransomware attacks increased by more than twelve percent over the previous year, with 76% of organizations reporting at least one attack according to Veeam’s Ransomware Trends Report. Cybercriminals exploit Remote Desktop Protocol connections, phishing emails, and unpatched software vulnerabilities. Organizations face operational shutdowns that last weeks, with manufacturing companies experiencing the longest recovery times at 22 days on average. Healthcare systems suffer particularly severe impacts, as patient care disruptions and regulatory penalties add millions to recovery costs.
Financial Losses Compound Beyond Initial Breach Costs
Data breaches trigger cascading financial damage that extends far beyond immediate response expenses. Ponemon Institute research shows business disruption accounts for 51% of total breach costs, while regulatory fines and legal fees add another 23%. Customer churn rates spike 7.8% after security incidents, with financial services losing $5.87 million per breach on average. Small businesses face bankruptcy risks (60% close within six months of a major cyberattack according to the National Cyber Security Alliance).
Network Security Investment Lags Behind Threat Growth
Global cybersecurity spending is forecast to grow 11.3% to reach more than $188.3 billion in 2023, yet breach costs continue to rise at 15% annually. Organizations allocate only 3.5% of IT budgets to security despite facing 4,000 cyberattacks daily. The security skills shortage affects 3.5 million positions worldwide, which forces companies to rely on automated solutions. Legacy network infrastructure creates additional vulnerabilities (78% of organizations run outdated systems that lack modern threat detection capabilities).
These vulnerabilities demand comprehensive security solutions that can adapt to evolving threats and provide real-time protection across all network layers.
How Does CloudGuard Stop Advanced Threats?
AI-Powered Detection Blocks Zero-Day Attacks
CloudGuard achieves a 99.9% malware prevention rate and stops sophisticated attacks that traditional firewalls miss. The platform uses machine learning algorithms to analyze file behavior in real-time and identifies malicious patterns within milliseconds. This AI-driven approach eliminates the signature update delays that leave networks vulnerable for hours or days after new threats emerge.
Real-Time Traffic Analysis Prevents Lateral Movement
CloudGuard monitors both north-south and east-west traffic across hybrid cloud environments and provides complete visibility into network communications. The platform analyzes network events and detects anomalous behaviors that indicate compromised systems. The unified management console aggregates threat intelligence from multiple sources and enables security teams to identify attack patterns across distributed infrastructure.
Automated Playbooks Reduce Response Times
CloudGuard’s automated response capabilities eliminate manual intervention delays during security incidents. The platform executes pre-configured playbooks that isolate compromised systems, block malicious traffic, and alert security teams within seconds of threat detection. Integration with Infrastructure as Code tools enables automatic policy updates across CI/CD pipelines and prevents security gaps during rapid deployment cycles. Check Point’s position as leader in the 2025 Gartner Magic Quadrant for Hybrid Mesh Firewalls validates CloudGuard’s automated orchestration capabilities.

Dynamic Policy Management Adapts to Infrastructure Changes
CloudGuard enforces security policies that scale automatically as workloads evolve and migrate between environments. The platform adapts to changes in tags and metadata without manual configuration updates (maintaining consistent protection across private and public clouds). Dynamic object awareness updates security rules based on real-time infrastructure changes and eliminates policy gaps during rapid scaling events. This automated adaptation becomes essential when organizations implement proper configuration strategies and deployment practices.
How Do You Deploy CloudGuard Successfully?
Start with Comprehensive Network Discovery
Organizations must map every device, connection, and data flow before they deploy CloudGuard security policies. Network discovery tools identify more assets than manual inventories according to Lansweeper research, which includes shadow IT devices that create security gaps. Scan all network segments and document application dependencies, as CloudGuard’s micro-segmentation requires accurate topology data. Schedule discovery scans during off-peak hours to minimize performance impact and prioritize critical systems that handle sensitive data or regulatory compliance requirements.
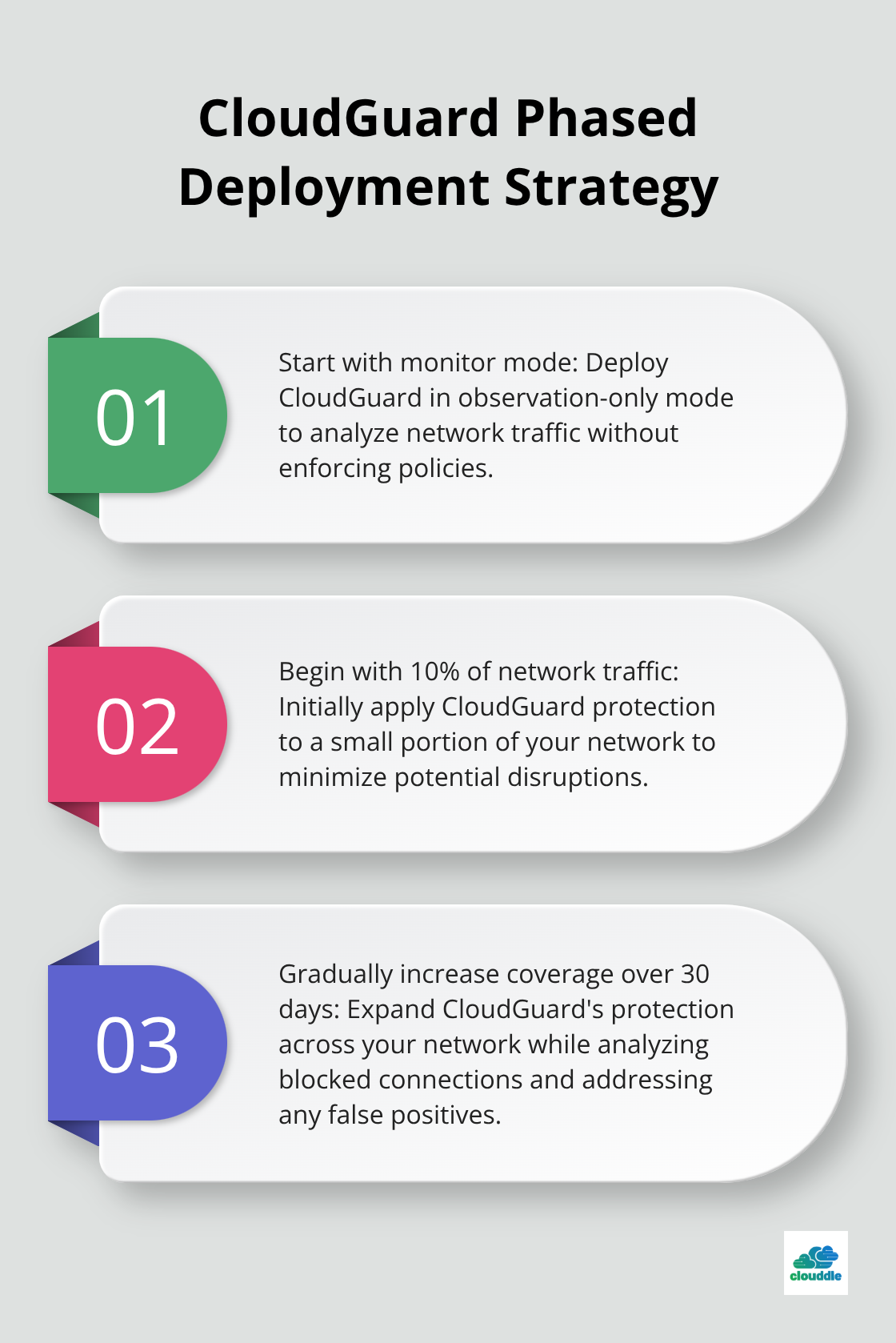
Deploy in Phases with Traffic Monitoring
CloudGuard deployment succeeds when organizations start with monitor mode before they activate enforcement. Begin with 10% of network traffic and gradually increase coverage over 30 days while you analyze blocked connections and false positives. Configure dedicated virtual networks for CloudGuard gateways to improve management isolation and reduce configuration complexity. Use route servers instead of user-defined routes in larger networks that change frequently. Test automated failover capabilities during planned maintenance windows and verify API configurations update route tables correctly.
Train Teams on Unified Management Operations
Security teams need hands-on practice with CloudGuard’s centralized console before production deployment. Establish clear escalation procedures for threat alerts and define response times for different incident severity levels. Create custom dashboards that display relevant metrics for each team role, as generic views reduce operational efficiency. Document policy exceptions and approval workflows, since CloudGuard’s automated responses require human oversight for business-critical applications (monthly sessions on new features maintain team proficiency with evolving security capabilities).
Configure Automated Response Playbooks
CloudGuard executes pre-configured playbooks that isolate compromised systems and block malicious traffic within seconds of threat detection. Set up integration with Infrastructure as Code tools to enable automatic policy updates across CI/CD pipelines and prevent security gaps during rapid deployment cycles. Test response scenarios during controlled exercises to validate playbook effectiveness and adjust timing parameters based on network performance requirements.
Final Thoughts
CloudGuard network security transforms how organizations protect their digital infrastructure against sophisticated cyber threats. The platform’s 99.9% malware prevention rate and AI-powered detection capabilities stop zero-day attacks that bypass traditional security solutions. Organizations that implement CloudGuard experience 40% faster incident response times through automated playbooks and unified management consoles.
The financial benefits extend beyond immediate threat prevention. Companies avoid the .45 million average cost of data breaches while they reduce operational disruptions that affect customer trust and revenue. CloudGuard’s automated policy management eliminates manual configuration errors and scales protection across hybrid cloud environments (without additional staffing requirements).
We at Clouddle specialize in comprehensive security solutions that protect business operations and support growth objectives. Our managed IT and security services help organizations deploy CloudGuard effectively while we maintain 24/7 support and flexible service agreements. Contact us to assess your network security requirements and develop a proactive protection strategy.


